Chapter 4. D
Dark.Fail
Dark.Fail is a vital directory service on the Tor network. While Google has used google.com since 1998 and Amazon has used amazon.com since 1994, that sort of consistency and reliability is seldom seen on what many refer to as the Dark Web. Tor network domain names change frequently (sometimes multiple times a day), so Dark.Fail’s clearnet (the regular internet outside of the Dark Web) site, dark.fail, is a constantly updated directory of Dark Web URLs on the Tor network and I2P, the two most popular encrypted proxy networks.
The anonymizing nature of proxy networks makes them a popular medium for illegal activity. Dark.Fail lists many illegal darknet markets, but it also lists Tor websites for mainstream entities such as the New York Times, the BBC, and Facebook. In most countries outside of China, the Tor network and its accompanying browser are perfectly lawful, and so is simply visiting darknet markets. The moment you buy or sell illegal goods and services, that’s when you’ve broken the law.
See also “Dark Web/darknet”, “Invisible Internet Project (I2P)”, “Tor (The Onion Router)”
Dark Web/darknet
The darknet is a part of the internet that is only accessible through a particular proxy network, usually Tor or I2P. The web component of the darknet is called the Dark Web. For simplicity, all of the Dark Web is part of the darknet, but not all of the darknet is the Dark Web. In most of the world, it’s lawful to use the darknet as long as you’re not breaking other laws while doing so. (The term clearnet, by contrast, refers to the ordinary internet.)
To access the darknet, you need to install Tor Browser or an I2P client on your PC or mobile device, make sure that your firewalls don’t block Tor or I2P, and connect to the internet. You can’t access Tor with an I2P client, and you can’t access I2P through the Tor Browser, but you can still access the clearnet through Tor and I2P.
Here’s how proxy networks work: your endpoint (PC or phone) sends packets to a Tor or I2P entry node. That node sends packets to the next node, and so on, until the packets go through the exit node and to the internet server you’re communicating with. Each node in the route only knows the IP addresses for the nodes it’s sending or receiving from, and only the entry and exit nodes know your endpoint’s IP address or the server’s IP address. There’s end-to-end encryption throughout the Tor or I2P route, so you’re anonymous (unless someone spies on your packets through an exit node).
The Dark Web, and the darknet in general, are often portrayed as solely evil places. A technology designed for anonymous communication will inevitably be used for crime, and darknet markets do sell illegal drugs, malware, cyberattack services, sensitive stolen data, and other kinds of illicit goods and services. Criminals and threat actors often plan their crimes on darknet forums and chat services, and law enforcement agencies access the darknet to monitor those plans and investigate crime. Many such markets have been shut down, but it would be very difficult to eliminate the darknet completely.
But the fact that a medium can be used for crime doesn’t mean that medium shouldn’t exist. The darknet is also a crucial means for investigative journalists, whistleblowers, and hacktivists to communicate for the benefit of society, while protecting their anonymity from hostile governments, militaries, and other such powerful entities.
See also “Cybersecurity”, “Dark.Fail”, “Dread forums”, “Exploit”, “Hacktivism”, “Malware”, “Invisible Internet Project (I2P)”, “Silk Road”, “Tor (The Onion Router)”
DARPA (Defense Advanced Research Projects Agency)
The Defense Advanced Research Projects Agency (DARPA) is a US government agency under the US Department of Defense (DoD) that was founded in 1958. There have been periods where it was named the Advanced Research Projects Agency (ARPA)—between 1958 and 1972, and again during Bill Clinton’s presidency from 1993 to 1996. ARPAnet, the technological precursor to the modern TCP/IP-based internet, was launched in 1969.
DARPA and the National Aeronautics and Space Administration (NASA) have a common origin: both were responses to the Soviet space program launching the Earth’s first artificial satellite, Sputnik, in 1957. It was the height of the Cold War, and American ingenuity would not be outdone by those communist Soviets! So the Space Race commenced. NASA focuses on advancing American space exploration and research, while DARPA develops new technologies for the military.
DARPA doesn’t have its own research facilities or laboratories—unusual for the DoD. It has minimal bureaucracy, and its leaders typically serve only about three to five years. DARPA recruits the “best and brightest” to conduct bold and innovative (and usually secretive) projects during their short terms of employment. It saddens me that war is such a driver of computer technology, but war is one of America’s top financial priorities!
There’s at least one direct connection between DARPA and Cult of the Dead Cow (cDc), the notorious hacker culture pioneering hacktivist group: after Michael “MafiaBoy” Calce’s infamous series of DDoS attacks, DARPA recruited cDc member Peiter “Mudge” Zatko in 2000 to help prevent future such attacks. At DARPA, Mudge created a program to offer grants to hackers to help improve the US government’s security posture.
The most important technological advance that came out of DARPA is surely ARPAnet, which has its own entry in this book. Others include:
DARPA’s oN-Line System (NLS), unveiled in 1968, which is ARPAnet’s father, the internet’s grandfather, and the World Wide Web’s great-grandfather. The very first computer mouse, raster-scan video monitors, screen windowing, and hypertext links, and some very rudimentary computer networking, were all invented for NLS.
The NAVSTAR Global Positioning System (GPS), which began development in 1973.
The Personalized Assistant that Learns (PAL) artificial intelligence program started at DARPA in 2002 with the goal of designing “cognitive computing systems to make military decision-making more efficient.” Its voice interaction functions became a part of the creation of Siri in 2007.
The High-Productivity Computing Systems (HPCS) program, launched in 2002, gives grants to IBM, Cray, Hewlett-Packard, Silicon Graphics, and Sun Microsystems to develop better-performing and more affordable (relatively speaking) supercomputers.
See also “ARPAnet”, “Artificial intelligence (AI)”, “Calce, Michael “MafiaBoy””, “Cult of the Dead Cow (cDc)”, “Internet”, “Supercomputers”, “TCP/IP (Transmission Control Protocol/Internet Protocol)”
Data
See “Azure”, “Binary”, “CIA triad (confidentiality, integrity, availability)”, “Cleartext”, “Common Vulnerabilities and Exposures (CVE)”, “Cryptography”, “Cybersecurity”, “Dark Web/darknet”, “Denial-of-service (DoS, DDoS) attacks”, “Diffie-Hellman key exchange”, “Floppy disk”, “Ham radio”, “Hexadecimal numbering”, “Hopper, Grace”, “Internet”, “Key”, “Networking”, “Packet switching”, “Piracy”, “Pretty Good Privacy (PGP)”, “Quantum computing”, “Ransomware”, “Rivest-Shamir-Adleman (RSA) cryptography”, “Zettabyte Era”
Da Vinci, Leonardo
Leonardo da Vinci (1452–1519), born in Florence, Italy, is probably the most famous person from the 15th-century Italian Renaissance, and certainly the earliest historical figure with an entry in this book. He’s someone I think of as being a “hacker” before being a hacker was a thing. (I would say being a hacker has been “a thing” since the 1950s at MIT’s Tech Model Railroad Club.)
Of course, da Vinci painted the most famous piece of visual art in history, the Mona Lisa, as well as The Last Supper and many other masterpieces. His drawing The Vitruvian Man is still seen in countless medical anatomy textbooks and classrooms.
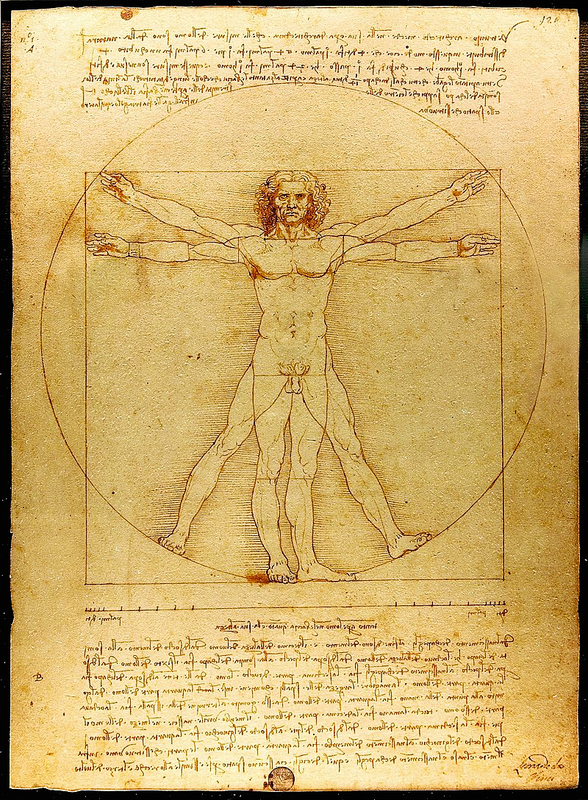
The term STEM (science, technology, engineering, and mathematics) didn’t exist in da Vinci’s era, but he was highly accomplished in all four of those areas. The Vitruvian Man combines da Vinci’s fascination with human anatomy and proportion with concepts he learned from the architect Vitruvius Pollio.
Da Vinci was also famed for his inventions. Some were precursors to modern aircraft, but couldn’t be built without motor engines, which didn’t exist yet. He was truly thinking centuries into the future.
Imagine what could have happened for hacker culture if we could put da Vinci in a room with Ada Lovelace, Alan Turing, and Hedy Lamarr! Perhaps that room could be a meeting of the Tech Model Railroad Club or the Homebrew Computer Club. It would make a great holodeck simulation for Captain Picard and Commander Data.
See also “Homebrew Computer Club”, “Tech Model Railroad Club”
Debian
Debian is one of the oldest and most popular Linux kernel-based operating systems. Pre-Alpha Debian Linux 0.01 was released in September 1993, and the first public beta, Debian Linux 0.90, was released in January 1994. Beta development took quite a long time, because the first stable release, Debian 1.1 didn’t come out until June 1996. As of November 2022, the latest Debian release is the Alpha 1 version of Debian 12.0.
Debian is maintained by the Debian Project, which describes itself as “an association of individuals, sharing a common goal: We want to create a free operating system, freely available for everyone. Now, when we use the word ‘free’, we’re not talking about money, instead, we are referring to software freedom.” Now that’s hacker culture!
Interestingly enough, people use Linux distributions based on Debian even more often than “vanilla” Debian. The nature of the open source community, where code is freely shared, means that developers are welcome to develop their own forks of other applications and operating systems. (A fork is a copy of an existing software project to which another entity has added their own modifications.)
It’s difficult to find reliable usage statistics for open source operating systems on consumer PCs, but many web servers run Debian and forks of Debian. According to W3Techs.com, as of 2022, 6.1% of websites were using web servers in Debian and 12.6% of websites were using web servers in Ubuntu, one of the most popular Debian forks. There are also forks of Ubuntu that use different graphical user environments. For instance, Kubuntu combines Ubuntu with the KDE user environment. Linux Mint is another popular Debian fork.
See also “Git/GitHub”, “Linux”
DEC (Digital Equipment Corporation)
Digital Equipment Corporation (DEC) was an innovative underdog computer maker that dominated enterprise computing from the 1960s through the 1980s. Its machines, mainly minicomputers, looked as serious as the competing products that IBM was making, and its leadership and corporate culture were progressive—a David to IBM’s Goliath. Hackers in the 1960s loved DEC’s computers, including MIT’s Tech Model Railroad Club.
Ken Olsen and Harlan Anderson, colleagues at MIT’s Lincoln Laboratory in the 1950s, noticed that students preferred computers that were easier to interact with than punch-card machines like the IBM 650 and that could provide real-time feedback.
Olsen and his brother Stan founded a company to produce a user-friendly computer, but initially had difficulty securing financing; investors were wary of investing in computer companies, which mostly didn’t last long. Olsen and Anderson were advised to not use the word “computer” in their name. They named the company Digital Equipment Corporation and planned to market their products as laboratory equipment, which brought in enough funding to get the company up and running in a former 19th-century wool mill in Maynard, Massachusetts.
In 1961, DEC produced its first proper computer, the PDP-1. PDP stood for “programmable data processor,” to avoid the dreaded C-word. The PDP-1 model sold for $120,000 (about $1 million today), but Olsen gave one to MIT, where the Tech Model Railroad Club used it to create Spacewar!, widely considered to be the first video game ever.
To sell to more businesses and institutions, DEC produced relatively more affordable computers, all things being relative: 1962’s PDP-4 was “only” $65,000, or about $640,000 in 2023 dollars. It was similar in capability to the PDP-1, but slower.
In 1970, the PDP-11 was DEC’s big breakthrough in minicomputers (which meant it was the size of a home appliance, not a room or a building floor). It used 8-inch floppy disk drives and memory that was physically similar to the memory our PCs use today. It was so popular that DEC sold technologically upgraded versions of it through 1996.
Olsen was a popular and very progressive leader whose employees actually enjoyed working for him. He made an effort to employ female and racially marginalized engineers and even offered employees home mortgages. One employee, Jerry Bernath, quoted Olsen’s often-used refrain: “Do what’s right and do the right thing!’”
DEC had the foresight to register the dec.com domain name in 1985, several years before the World Wide Web, and its machines could network with ARPAnet in the 1970s and the TCP/IP-based internet in the 1980s.
By 1990, DEC was number two in global computer sales, second only to IBM. But the early 1990s recession was hard on DEC, and they lost market share to Hewlett-Packard and Sun Microsystems. In 1992, Olsen retired. His replacement, Robert B. Palmer, was very unpopular with DEC employees. A former DEC employee explains that “GQ Bob,” known for driving a Porsche 911 to work, “was never one of us, and he never wanted to be one of us.”1
DEC launched AltaVista, a popular web search engine, in 1995 (three years ahead of Google). In 1998, DEC was acquired by Compaq for a whopping $9.6 billion, the biggest computer industry acquisition at the time. But Compaq couldn’t understand how to leverage DEC’s international market, and in 2002, Hewlett-Packard bought Compaq. The DEC brand had disappeared by 2004. I truly believe that if Ken Olsen had been replaced with a leader with an equally progressive, employee-friendly mindset, DEC would still exist today.
See also “ARPAnet”, “Hewlett-Packard (HP)”, “Minicomputers”, “Tech Model Railroad Club”, “World Wide Web”
Deep Web
People sometimes confuse the Deep Web with the Dark Web. The Dark Web is part of the Deep Web, but the vast majority of the Deep Web is on the clearnet (the ordinary internet, which isn’t locked behind proxy networks like Tor or I2P). The definition of the Deep Web is everything on the web that isn’t indexed by mainstream search engines. Search engines like Google and Bing (you might use Bing and not even know it, it’s the search engine underneath DuckDuckGo) have web crawler bots that survey the web by going to a web page, and then going to as many links in those web pages as possible. A web page that isn’t linked effectively to web crawled web pages is going to be missed.
If you have a web browser handy, go ahead and visit https://www.oreilly.com. That’s the website for O’Reilly Media. It’s on the clearnet, because you were able to visit the site without using Tor or I2P. Google Search results for “O’Reilly Media” show O’Reilly’s official website as the top search result. That’s clear evidence that the O’Reilly Media site is part of the Surface Web and not the Deep Web.
Some of the Deep Web is very old content, and some consists of things like databases and parts of web applications (like your Gmail inbox) that shouldn’t be search-engine indexable for security reasons.
As of this writing, the URL for Dark.Fail is:
You need to use Tor Browser in order to access that website. So it’s on the Dark Web, not the clearnet, and everything on the Dark Web is also on the Deep Web. So Dark.Fail isn’t Surface Web either.
Simple, eh?
If you want to try finding Deep Web content that’s Deep Web because it’s old, one of the best resources is Wayback Machine at Internet Archive. Wayback Machine is constantly taking snapshots of pages all over the web, both user-generated and automated.
There’s a Save Page Now web form on the home page. Enter the URL of any webpage you want, and it’ll snapshot it for you. The snapshots Wayback Machine stores can be explored like regular web pages. Most of the time, you can even click on links in the snapshots, and it’ll load a snapshot of the web page that was intended to be linked. Wayback Machine’s snapshots go all the way back to the 1990s. If there’s a very old web page that probably isn’t hosted on its original web server anymore, that’s the best place to find it. Thank you, Internet Archive, for this valuable service!
See also “Dark.Fail”, “Dark Web/darknet”, “Internet”, “World Wide Web”
DEF CON
DEF CON is a cybersecurity and hacking conference that has taken place every year since June 1993. Now it happens every August in Las Vegas. Though the conference is not a military event, its name is a reference to the US Military’s Defense Readiness Condition system, as mentioned in the 1980s hacker movie WarGames, which uses five threat levels. DEF CON 5 is the lowest perceived threat level, and DEF CON 1 indicates the maximum threat level and the need to prepare for war.
Jeff Moss, otherwise known as Dark Tangent, founded DEF CON when he was 18 years old. In a video from 2007, he discussed DEF CON’s roots in phone phreaking:
I just happened to have a bulletin board set up, and I had an OK job. So I paid my phone bill, unlike most back then, everybody else was phreaking [phone hacking] the connections. And so I became a big hub for eleven of these international networks...all these different networks from back in the day, and because of that, I was connected to pretty much all the communication that was going on in the underground that was active in those days.
DEF CON holds smaller events year round, such as movie nights over Discord and in-person security training sessions.
See also “Cybersecurity”, “Phreaking”, “WarGames (1983 film)”
Demoscene
The demoscene is where hacker culture meets art and music, as hackers explore the visual and musical potential of computers old and new. Many of the demoscene’s most prominent demogroups started in the late 1990s and early 2000s, and the earliest demos were made in the 1980s. Demogroups often maintain older PCs and operating systems as tools for their art, like the Commodore Amiga, Atari ST, Commodore 64, MS-DOS, ZX Spectrum, and Amstrad CPC. Most of the demoscene videos I’ve watched look like trippy synthwave music videos.
Demoscene.info states: “Demo-making is teamwork.... Graphicians and musicians create suitable pieces of art, the programmers fit all the parts together in an extensive amount of detail work to finally make it an executable program: the demo.”
The precursor to the demoscene was the “display hacks” of the 1950s: programs “with the same approximate purpose as a kaleidoscope: to make pretty pictures” and explore what a computer’s display output can do, according to The Cathedral and the Bazaar author Eric S. Raymond.
Some of the better-known demogroups include Conspiracy, MFX, Farbrausch, Haujobb, and Kolor. Demogroups often enter their demos in competitions, where they’re judged for their artistry and technical proficiency.
Denial-of-service (DoS, DDoS) attacks
Denial-of-service (DoS) attacks are one of the most common cyberattacks. They target the A in the CIA triad of cybersecurity: availability. A DoS attack overwhelms a networked target with so many packets of data that it shuts down.
A distributed denial-of-service (DDoS) attack uses a network of synchronized computers to perform a DoS, which is often more effective than a DoS attack which uses just one. DDoS attacks are most often performed by botnets, in which a cyberattacker commands a network of zombie malware-infected computers to engage in attacks. A computer may be infected by zombie malware without the user noticing.
Web servers are frequent targets of DoS and DDoS attacks, although any kind of networked computer can be a target. Sometimes networking devices such as routers can be targets as well.
Here are a few types of DoS attacks:
- Ping of Death
- Ping of Death DoS attacks involve sending malicious ping packets to a server that go over that server’s data size limit, causing it to crash.
- UDP flood
- Some internet protocols use User Datagram Protocol (UDP) packets instead of the more common Transmission Control Protocol (TCP) packets. A UDP packet doesn’t contain a header to guide its sequence. In a UDP flood DoS attack, a mass of UDP packets are sent to a bunch of random IP ports on the same target. That forces the target to repeatedly check for the application listening at each port. When it finds none, the targeted server can crash.
- HTTP flood attacks
- In an HTTP flood attack, one of the most common ways to DoS attack, the attacker floods a web server with a large number of
HTTP GETorPOSTrequests that look legitimate but aren’t, until the server crashes. - Low Orbit Ion Cannon
- Low Orbit Ion Cannon (LOIC) may be one of the most infamous DDoS attack tools. It was developed by Praetox Technologies for legitimate penetration testing purposes but has been abused by cyberattackers many times.
See also “CIA triad (confidentiality, integrity, availability)”, “Cybersecurity”, “Malware”, “Networking”, “Packet switching”, “Ping”
Developers
See “Crunch time”, “Git/GitHub”, “Programming”, “Whiteboard interviews”, “World Wide Web”
DevOps
DevOps is one of the most commonly used methodologies for deploying applications, both through cloud platforms and through internal enterprise networks. It’s all about combining the development team (the programmers) with the operations team (the IT department) to deploy and maintain responsive applications. To understand DevOps properly, first you must understand Agile development.
Applications and software projects deployed through the Agile methodology release new code and new features in small pieces to be responsive to changing client needs, rather than as fewer, larger updates. An Agile application updates in lots of little ways continuously, rather than going from version 1.5 one year to version 1.6 the next year. Ideally, this means it is always relevant and functional according to whatever the client’s needs are at any given time.
In DevOps, all of the work is as synchronized, frequent, and up to date as possible. Developers and operations work and collaborate simultaneously at each stage of development. IT people monitor the network’s usage and operation and share information with the developers, who are constantly working on patches and new features. It’s a way to apply hacker ingenuity to big corporate software needs. And the development of the application is a constant process. As soon as a patch or new feature is tested to be stable, it’s deployed!
DevOps and Agile development emerged around 2007 and 2008 and are considered an improvement on other application development methodologies, particularly the older, slower “waterfall” style.
The common wisdom in the cybersecurity industry now is that security testers must continuously audit and test code for security vulnerabilities in every step of the application development process. When security is implemented that way into DevOps, it’s called DevSecOps.
See also “Bug”, “Cybersecurity”, “Penetration testing”
Diffie, Whitfield
Did you buy something online today? Did you input your credit card number without it being breached by cyberattackers? One of the people you can thank is Whitfield Diffie (1944–), one of the founders of public-key cryptography.
Diffie loved math and started reading about cryptography in his youth. As a young man, he joined the MITRE Corporation, partly motivated by his desire to avoid being drafted to fight the Vietnam War. He also worked as a guest researcher at MIT’s Artificial Intelligence Laboratory, co-founded by AI scientist John McCarthy. McCarthy left MIT for Stanford University, and in 1969, Diffie followed, joining the Stanford Artificial Intelligence Laboratory.
Reading David Kahn’s The Codebreakers: The Story of Secret Writing (McMillan, 1967) fueled Diffie’s passion for digital privacy. He was especially interested in one-way functions, which would be important to developing cryptography technology with a public vector.
Public-key cryptography, which is necessary for encrypting internet communications, uses asymmetric keys. With symmetric keys, the math for the decryption key is the encryption key in reverse; that’s good for private-key cryptography because it’s all in a contained system. But the internet is public. If the encryption key sent to your web browser can be used to calculate the decryption key, that renders the cryptography pointless. It’s like leaving your house key right outside your front door.
In 1974, Diffie began collaborating with fellow cryptographer Martin Hellman, and the following year they were joined by cryptographer and puzzle-maker Ralph Merkle, from the University of California, Berkeley. Merkle’s puzzles influenced the development of the technology Diffie and Hellman would become known for: the Diffie-Hellman key exchange.
Diffie and Hellman introduced the Diffie-Hellman key exchange in a groundbreaking 1976 paper.2 Today it is used in RSA cryptography, which makes it part of all kinds of data-in-transit encryption.
I asked Diffie how the internet might be different if not for the advent of public key cryptography. He replied, “I assume it would depend far more on verified email addresses, in the way you currently prove that an email address is yours by receiving a PIN at the address and typing it into a website. I couldn’t have made a living fighting over whether encryption should be trapdoored; the police would be able to read everything.”
Diffie says quantum-safe public-key cryptography could be possible, but he does not believe the Diffie-Hellman key exchange could be applied to it. He does believe that quantum-safe public-key cryptography can be possible. He pointed me to the National Institute of Standards and Technology’s (NIST) Post-Quantum Cryptography project.
Diffie is now a consulting scholar at Stanford’s Center for International Security and Cooperation. He was inducted into the US National Security Agency’s Hall of Honor in 2020.
See also “ARPAnet”, “Berkeley, University of California”, “Cryptography”, “Diffie-Hellman key exchange”, “Hellman, Martin”, “Key”, “Massachusetts Institute of Technology (MIT)”, “Quantum computing”, “Rivest, Ron”, “Rivest-Shamir-Adleman (RSA) cryptography”, “Stanford University”
Diffie-Hellman key exchange
Whitfield Diffie and Martin Hellman invented the Diffie-Hellman key exchange in 1976, during ARPANet’s heyday. To secure data in a computer network, it needs to be encrypted while in transit. ARPAnet was the largest computer network in history at that point and needed that sort of security. The solution is public-key cryptography, which uses an asymmetric cipher. To encrypt data, users must receive a public key. Then the server on the receiving end uses a private key to decrypt the data. The cipher must be asymmetrical, meaning that knowing the public key doesn’t reveal the private key. The key exchanges must be kept secret in order to be secure. That’s where the Diffie-Hellman key exchange comes in.
Diffie and Hellman published a whitepaper in which they explained their goal: to “minimize the necessity of secure key distribution channels and supply the equivalent of a written signature.”3
They were inspired by cryptographic puzzles created by Berkeley computer scientist Ralph C. Merkle. Interestingly enough, RSA cryptography co-inventor Ron Rivest was one of the editors of Merkle’s paper.
See also “ARPAnet”, “Cryptography”, “Diffie, Whitfield”, “Hellman, Martin”, “Key”, “Rivest, Ron”, “Rivest-Shamir-Adleman (RSA) cryptography”
Disk, disc
See “Floppy disk”
DOOM (video game)
DOOM (1993) was a groundbreaking first-person shooter video game that left its mark on hacker culture. A whole franchise of DOOM games have been released since, but this entry focuses on the original, which debuted for MS-DOS with the shareware release of its first episode, Knee-Deep in the Dead, through the University of Wisconsin’s FTP server.
id Software’s John Carmack developed the Doom engine, which was eventually released as open source software under the GNU Public License. That opened the door for fans to develop a massive collection of fan levels and mods. DOOM has also been ported to just about every video game system and platform in existence (I think only Tetris can hold a candle to DOOM in that department). Some are quite obscure, like Symbian (a mobile operating system by Nokia that was never commercially successful), Flipper Zero (a recently released penetration testing device for cybersecurity hackers), and Texas Instruments TI-84 Plus graphing calculators. DOOM has even been run on ATMs and DSLR cameras.
If this inspires your hacker spirit, you should know that Android runs on a lot of the embedded systems in Internet of Things devices. Just find a way to port the Android 25th anniversary release, and you could be the first person to play DOOM on a smart refrigerator!
See also “Android operating system”, “DOS (Disk Operating System)”, “Open source”
DOS (Disk Operating System)
DOS stands for Disk Operating System. DOS operating systems generally have an ASCII text-based user interface, rather than a graphical user interface (GUI). The name DOS has been used for many operating systems over the years, but most of the time, when an old nerd talks about DOS, they’re referring to the Microsoft (MS-DOS) or IBM (PC-DOS) versions. Until 2001, every consumer version of Windows ran on top of MS-DOS.
The story of DOS starts with Gary Kildall and his company, Digital Research. In 1974, Kildall developed CP/M, an innovative operating system for the business market, designed for 8-bit microcomputers. It processed basic input and output tasks through hardware, so that applications would mainly interface with the operating system. This made it much easier to support a variety of 1970s microprocessor hardware from different vendors. It probably also made application development easier, since you could simply develop an application to run in CP/M rather than creating separate applications for specific models of business microcomputers. (A similar sort of broad hardware and vendor support would make Microsoft a smash success, with MS-DOS and Windows for “IBM compatible” PCs.)
If you want to try using DOS today, check out FreeDOS, an GNU Public License open source project. If you need to run a supported OS directly on legacy hardware that ran PC-DOS/MS-DOS, FreeDOS is the way to go. If you want to play classic DOS games or emulate DOS utilities on a modern Windows, macOS, Linux, or BSD/UNIX-based PC, go for DOS Box, an MS-DOS emulator which runs as its own application.
See also “DOOM (video game)”, “IBM”, “Microcomputers”, “Microsoft”, “Open source”, “Shareware/freeware/abandonware”
Draper, John
Dread forums
Dread is a website on the Dark Web that’s modelled on Reddit and can only be opened via Tor.4 Anyone can make their own subdread (the Dread version of a subreddit) based on an area of interest. Moderators control what types of posts are allowed and can ban users who break their rules. Most subs never become popular, but a handful can have millions of active users. The most popular subdreads focus on darknet markets and how to engage in cybercrime.
There is no connection or affiliation between Reddit and Dread. When Reddit cracked down on cybercrime subreddits in 2018, anonymous founder HugBunter simply replicated its model.
Dread was offline in early 2023 when I first researched this entry, but as of October 2023, it’s back online. That’s the nature of the darknet: sites are often subject to DDoS (distributed denial-of-service) attacks from law enforcement and other cybercriminals, and are thus unreliable.
See also “Dark Web/darknet”,“Denial-of-service (DoS, DDoS) attacks”, “Reddit”, “Tor (The Onion Router)”
DRM (Digital Rights Management)
DRM, which stands for digital rights management, is a controversial form of software code used to ensure that only paying customers have access to particular digital content. DRM is applied to a wide range of media, including music, videos, video games, software applications, paywalled websites and web apps, digital journals and periodicals, and ebooks. It is designed to restrict intellectual property rights under a capitalist system, and thus DRM goes against the spirit of hacker culture, wherein “knowledge should be free.” As the Free Software Foundation’s anti-DRM campaign, Defective By Design, describes it:
DRM creates a damaged good; it prevents you from doing what would be possible without it. This concentrates control over production and distribution of media, giving DRM peddlers the power to carry out massive digital book burnings and conduct large scale surveillance over people’s media viewing habits.
If we want to avoid a future in which our devices serve as an apparatus to monitor and control our interaction with digital media, we must fight to retain control of our media and software.
In fact, DRM often prevents paying consumers from using media in ways that are within their legal rights: it can interfere with using public library books, accessing public-domain media, making backup copies, and using media for nonprofit or educational purposes, as outlined under the “fair use” or “fair dealing” exemptions in copyright laws.
If you’re reading an ebook version of this very book, there could well be DRM on it, depending on where you bought it. While O’Reilly doesn’t place DRM on its ebooks, sellers like Amazon Kindle, Google Play, and Apple can and often do. If you pirated this book, you or the pirate likely cracked that DRM.
See also “Creative Commons licenses”, “Piracy”
Dungeons & Dragons (game franchise)
Dungeons & Dragons (DnD) was the first popular tabletop roleplaying game (RPG) and is still hugely popular. It was invented by Gary Gygax and David Arneson and was first published in 1974 by Gygax’s company, Tactical Studies Rules (TSR). Wizards of the Coast, a subsidiary of Hasbro, bought the rights to DnD from TSR in 1997. DnD’s long-lived commercial success has inspired thousands of other tabletop RPGs. The common element in these games is that they tell a story in which players make decisions and roll dice for their characters, and they can be played without computers, in person, as a social activity (though many players these days do play over the internet).

In the game, a small group of people (known as a “party”) invent fantasy characters for themselves to play. Each player uses a paper character sheet to design their character’s biography and statistics; optionally, they can also use a toy figure to represent their character. Each character is assigned a class (such as Rogue or Cleric) and a race (such as Elf or Human),5 and these classifications influence the characters’ skills, available spells, strengths, and weaknesses by modifying the results of their die rolls. Players use a set of seven dice, including a 4-sided die, a 6-sided die, an 8-sided die, a 10-sided die, a percentile die, a 12-sided die, and a 20-sided die.
The game is facilitated by a player called the Dungeon Master (DM), who tells the story and judges how players can implement game rules. Most DMs use official game books to guide character and world creation. The DM may provide a hand-drawn world map or physical props to represent the story’s world.
Although DnD is the ultimate in nerdy, low-tech fun, it has many connections to hacker culture. A lot of hackers are into DnD, including innovators from the Silicon Valley scene. DnD has also inspired many, many video game RPGs and JRPGs. And in the fifth edition of DnD (the most recent as of this writing), players can even choose a Hacker subclass for their Rogue characters. As the DnD Wiki describes it:
As a hacker, you gain access to knowledge utilized to fade out of sight, infiltrate technology, and eventually even tap into the spellweave to block access to it. This is the common lot of a hacker, abusing technology to your whim, and with this nefarious capability, what a new world you can build....
See also “Roleplaying games (RPGs)”
1 Quoted in Steven Levy, Hackers: Heroes of the Computer Revolution: 25th Anniversary Edition (O’Reilly, 2010).
2 Whitfield Diffie and Martin Hellman, “New Directions in Cryptography,” IEEE Transactions on Information Theory 22, no 6 (November 1976): 644–54.
3 Whitfield Diffie and Martin Hellman, “New Directions in Cryptography,” IEEE Transactions on Information Theory 22, no. 6 (November 1976): 644–54.
4 This entry is adapted from a blog post I wrote for Hack the Box in 2021.
5 Wizards of the Coast announced in 2022 that the “race” system will transition to “species” in new editions.
Get Hacker Culture A to Z now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

