Recipe 2-3: Manual Scan Result Conversion
This recipe shows you how to manually create ModSecurity virtual patches to mitigate vulnerabilities identified by Arachni scan results.
Ingredients
- ModSecurity Reference Manual5
- SecRule directive
- chain action
Now that you know about the vulnerabilities from running an Arachni scan in Recipe 2-2, you must now figure out how to best mitigate the identified issues. We can write specific ModSecurity rules to patch these issues virtually. Before writing the rules, however, we must choose which security model to use: blacklist (negative) or whitelist (positive). Let’s look at the benefits and drawbacks of each model, along with sample virtual patches.
Blacklist (Negative) Security Model
The blacklist security model uses rules or signatures that describe attack traffic. This is essentially a misused detection system. The OWASP ModSecurity CRS uses this security model extensively. The idea is simple: You look for specific characters or sequences of characters as input. If they are found, you block them. Let’s look at a practical example from the Arachni scan report from Recipe 2-2. Figure 2-13 shows a SQL Injection vulnerability.
Figure 2-13: Arachni SQL Injection vulnerability
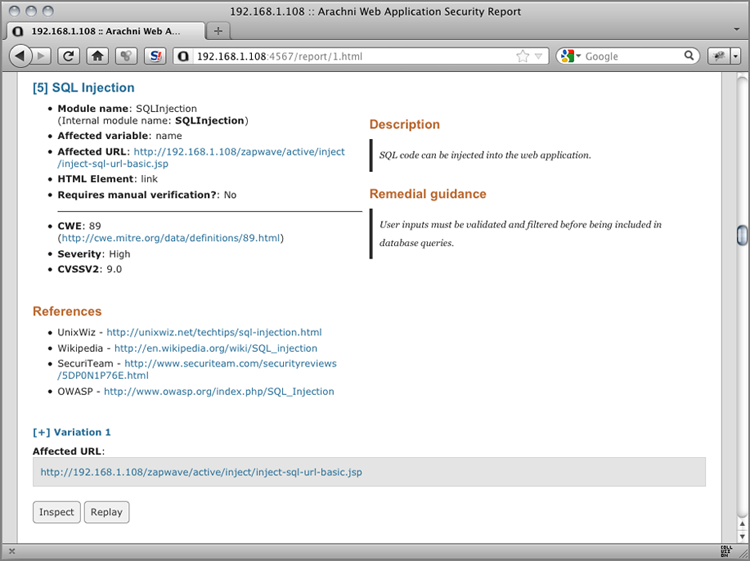
This vulnerability lists the name parameter on the /zapwave/active/inject-sql-url-basic.jsp page. If you click the Replay button, a new browser tab opens. You ...
Get Web Application Defender's Cookbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

