Recipe 1-9: Obscuring Sensitive Data in Logs
This recipe shows you how to use ModSecurity to obscure sensitive data that is captured within the audit logs.
Ingredients
- ModSecurity Reference Manual18
- sanitiseArg action
- sanitiseMatchedBytes action
HTTP audit logging comes with a catch-22: Some sensitive user data probably is captured within the logs, such as passwords or credit card data. We want to log these transactions, but we do not want to expose this sensitive data to anyone who may access these logs. ModSecurity has a few different rule actions that can be used to obscure selected data within the audit logs. Let’s look at a few sample use cases.
Login Passwords
Let’s use the WordPress login form shown in Figure 1-6 as an example.
Figure 1-6: Sample WordPress login form
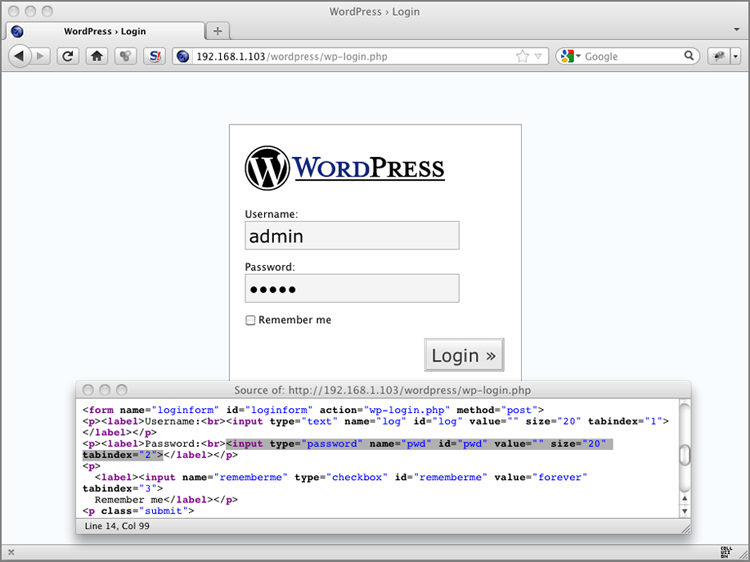
In Figure 1-6, we see from the HTML source code that the password being submitted is passed in a parameter called pwd. If we want to obscure the password payload in the logs, we can add the following sample rule that uses the ModSecurity sanitiseArg action:
SecRule &ARGS:pwd "@eq 1" "phase:5,t:none,id:'111',nolog,pass,\
sanitiseArg:pwd"When the login form is submitted, this is how the transactional data now appears in the audit log file:
--e947184b-A-- [20/Feb/2012:09:54:24 --0500] T0Jen8CoAWcAAQ0jNzcAAAAA 192.168.1.103 59884 192.168.1.103 80 --e947184b-B-- POST /wordpress/wp-login.php HTTP/1.1 ...Get Web Application Defender's Cookbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

