Chapter 10. Security
Deploying Trino at scale, discussed in Chapter 5, is an important step toward production usage. In this chapter, you learn more about securing Trino itself as well as the underlying data.
In a typical Trino cluster deployment and use, you can consider securing several aspects:
-
Transport from the user client to the Trino coordinator
-
Transport within the Trino cluster, between coordinator and workers
-
Transport between the Trino cluster and each data source, configured per catalog
-
Access to specific data within each data source
In Figure 10-1, you can see how the different network connections of Trino need to be secured. The connection to your clientâfor example, the Trino CLI or an application using the JDBC driverâneeds to be secured. The traffic within the cluster needs to be secured. And the connections with all the different data sources need to be secured.
Letâs explore these needs in more detail in the following sections, starting with authenticating to Trino as a user.
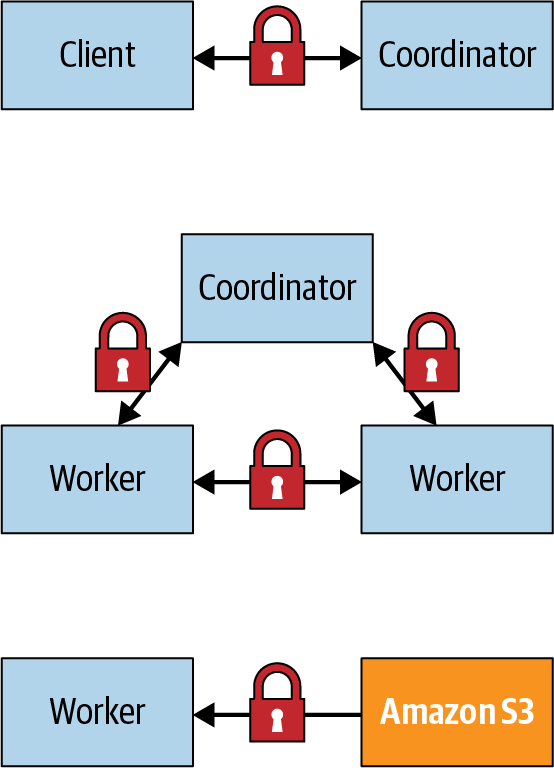
Figure 10-1. Network connections of Trino usage to secure
Authentication
Authentication is the process of proving an identity to a system. Authentication is essential to any secure system. A variety of authentication methods are supported by computer systems, including Kerberos, password with Lightweight Directory Access Protocol (LDAP), certificate authentication, and ...
Get Trino: The Definitive Guide, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

