Reese: Anyone who’s trying to use the override would have to hack through the reactor’s firewall. That would take massive computer power, which NRC could see coming a mile away.
Jack: Is it possible that NRC could miss this due to unusually heavy traffic on the Internet?
Reese: I don’t follow.
Jack: Well, less than an hour ago millions of computers around the world were streaming the trial of the Secretary of Defense. Is it possible that this trial was just some kind of a Trojan horse to disguise a massive attack on nuclear power plants’ firewalls?
Reese: That might be possible.[22]
Successful enterprise security monitoring demands focus. In this fictitious attack from Fox’s popular television series 24, the network security team (NRC) missed a targeted, critical attack due to a decoy surge in network traffic. The depicted scenario demonstrates how difficult it is to monitor effectively when all systems are given “equal” attention. Focused monitoring requires considerable tuning and quick recognition of benign traffic. For example, an Oracle 11i-based ERP system will generate thousands of messages per hour from its various components. Without tuning and a strong understanding of the environment, the network monitoring staff will waste their time following dead ends.
Example 4-1 contains an example of a Snort alert that could result from monitoring an Oracle system.
Example 4-1. Snort alert from monitoring an Oracle system[23]
[**] [1:2650:2] ORACLE user name buffer overflow attempt [**] [Classification: Attempted User Privilege Gain] [Priority: 1] [Xref => http://www.appsecinc.com/Policy/PolicyCheck62.html] Event ID: 62662 Event Reference: 62662 11/21/06-17:16:04.892127 172.16.0.136:34833 -> 172.16.5.12:1521 TCP TTL:64 TOS:0x0 ID:32755 IpLen:20 DgmLen:100 DF ***AP*** Seq: 0xB700F908 Ack: 0xF1594793 Win: 0x3309 TcpLen: 32 TCP Options (3) => NOP NOP TS: 2796076485 835448929 00 30 00 00 06 00 00 00 00 00 03 68 FB 01 00 00 .0.........h.... 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 01 ................
Is this a critical alert? The words buffer overflow attempt are sure to get your attention, yet this alert is benign—often triggered by Java applications using a strange database connection string.[24] By focusing your tuning and your monitoring, you can ignore and tune out these benign events. Across the enterprise, various logging and monitoring components generate millions of additional examples of such alerts. For effective monitoring, each alert will require detailed analysis, often involving support and application staff members to explain the anomalous traffic. This kind of tuning is an important part of security monitoring, and it’s a continuous task. Policy-based monitoring can’t spare you the tedium of such tuning; rather, it will narrow your focus to critical systems and to events that indicate policy violations. To apply policy-based monitoring, you must first select which systems you want to monitor.
This chapter will describe the various approaches for selecting monitoring targets. Once selected, we’ll drill deeper into the targets, providing guidance for how to discover the components within them, and documenting the details necessary to configure event feeds.
To effectively select systems to monitor (i.e., your targets), you must establish your priorities. Your approach will be based on the risk or perceived value of the targets and the information within them. You can develop a taxonomy of approaches in countless ways. Here’s the range we’ll consider in this chapter:
- Business impact analysis
Differentiating systems based on level of criticality in the context of availability
- Revenue impact
Applications that drive orders and delivery
- Expenses impact
Systems that manage contractual obligations to partners and customers
- Legal requirements
Statutes and contracts that highlight which information and systems to protect
- Sensitivity profile
Systems that access privileged, restricted information
- Risk profile
Systems that can’t be properly protected using existing controls
- Visibility profile
Systems which, if attacked or compromised, might prove embarrassing to the company or damaging to visitors
The process of conducting a business impact analysis (BIA) is part of the disaster recovery planning function in most enterprises. It’s a methodology for identifying critical processes and systems to establish their priority for backup and disaster recovery. Many books describe methodologies for this exercise, including guides for the Certified Information Systems Security Professional (CISSP) exam. Here’s a sample process taken from Roberta Bragg’s CISSP Training Guide:[25]
Identify time-critical business processes.
Identify supporting resources (personnel, facilities, technology, computers, software, networks, equipment, vital records, data, etc.) for the critical processes.
Determine Maximum Tolerable Downtimes (MTDs).
Return to business units for validation.
Provide the final report, including MTDs and recommendations for next steps, to senior management.
Bragg recommends a series of interviews with business stakeholders to determine the effect of downtime or disruption on business processes. BIA breaks down the impact over time, charting the results into a table for more detailed analysis and discussion, to guide prioritization.
The key input to these prioritization discussions is the impact to the business bottom line, which invites consideration of sales, revenue, financial interest, fines/penalties, and even costs to your customers and partners. This information is then verified in steps 4 and 5. Hopefully, your company’s disaster planning team has already performed a BIA. In any case, the generated list provides an excellent starting point for targeting your security monitoring.
The BIA focuses heavily on the revenue impact of disruptions, so let’s analyze revenue impact a bit further. Any application used in taking or fulfilling orders, for example, is tied directly to revenue (for companies that sell goods, not services). For an e-commerce company, Bragg suggests that the MTD is exactly 0, as even tiny amounts of downtime can result in staggering losses. According to Cavusoglu, Mishra, and Raghunathan, “Firms that solely depend on the Internet as a revenue generating mechanism pay higher prices in case of a security breach than firms that have multiple sales channels. Security of IT systems for net firms is extremely important for a net firm’s success.”[26]
Of course, not all companies make their money selling goods. Revenue for service-based companies depends on the companies’ ability to perform the task for which they’ve been hired. The auto body shop, the U.S. Postal Service, and eBay don’t receive revenue if they can’t fix, deliver, or auction your product.
When considering systems that are critical to revenue generation and recognition, order entry and fulfillment systems will have the largest impact on revenue for most companies:
- Order entry systems
Whether orders are entered directly by customers or they’re taken by a sales professional, the systems used for taking orders are critical to revenue generation. Typically, many systems are involved in the process, including inventory, order status, order booking, credit card processing, and return processing systems. These systems must not only be protected from unplanned downtime, but also are targets for fraud and theft.
- Order fulfillment systems
According to U.S. Generally Accepted Accounting Principles (GAAP), revenue is not recognizable (placed on the books) until the goods or services are delivered. Therefore, manufacturing, shipping, and service scheduling/tracking systems are key parts of revenue. Although these systems are not typically exposed to the Internet as directly as order entry systems (and therefore are not as directly in the path for fraud and hacking), they are critical for maintaining compliance with regulatory requirements and revenue recognition.
Applications that support payments are critical to managing expenses. If these applications are unable to function properly, your company will likely incur financial penalties. Though the cause of disruption is normally accidental, it’s now becoming feasible for malicious competitors to use distributed denial-of-service (DDoS) tools against you to impact your revenue or cause painful expenses. Such was the case in March 2008, when the gaming site Gala Coral was knocked offline for more than 30 minutes by a DDoS attack, likely at the direction of a competitor.[27]
Payroll and time-keeping systems directly impact expenses. Monitoring these systems can help prevent fraud and abuse, as was uncovered in an audit of Ashmont Cleaning Company, where an employee was changing system records of his work hours to receive extra overtime pay, and stole more than $30,000 before getting caught as the result of an audit (Belloli & McNeal 2006).[28] Two years ago, an unnamed company discovered that an employee was using its purchase order system to steal from the company by routing orders to shell companies, which the employee and her husband controlled. These cases demonstrate that monitoring financial systems such as those that process purchasing and payroll requires more than just watching for availability problems. Experts in the rules and exceptions of business processes must review reports and workflow, using periodic reports to catch problems early. System monitoring can augment human review by catching abuse of account system privileges or attempts to guess passwords for accounts with elevated system privileges.
A company may incur punitive expenses from the government or from partners in legal contracts if its systems do not perform their proper functions in terms of operating and protecting sensitive information. As dimensions of legal impact, let’s consider regulatory compliance and contractual obligation and how they can affect your company.
My neighbor manages production for a German manufacturer of industrial heat exchangers. One spring evening as we were sharing our experiences of being “called into a crisis” at the office, he topped our stories by explaining the huge penalties he faces if he’s caught violating local environmental regulations. His employees must maintain high purity standards when discharging waste water used in the manufacturing plant. If an auditor discovers a breach of compliance, the company will incur shattering monetary fines and corporate officers will face personal liability, including a prison sentence, upon conviction.
Every company must comply with some amount of regulation governing its business operations. Compliance is often demonstrated in routine audits and reporting; active monitoring is seldom necessary to achieve compliance. Regulations are often developed to protect information, and such systems typically contain the most sensitive information in your enterprise. Active monitoring is often required by regulation, and is a practical part of protecting regulated systems and data.
Most regulatory controls are aimed at protecting the integrity and confidentiality of financial information. The Sarbanes-Oxley Act of 2002 (SOX), which was enacted after a series of accounting scandals, specifies a set of legal controls and audits in an effort to prevent further scandals. SOX Section 404 is aimed at assessing the controls bounding financial reporting, and encourages companies to regulate and monitor the processes for storing and accessing financial information. Effective monitoring for financial systems should concentrate on the databases and applications used for such processing. This includes means for detecting unauthorized changes and abuse of privileges, as well as monitoring for database administrators and others with administrative access.
A U.S. regulation aimed at personal privacy, the Gramm-Leach-Blilely Act (GLBA) contains a “Safeguards Rule” which requires companies to protect non-public personal information:
In furtherance of the policy in subsection (a) of this section, each agency or authority described in section 6805 (a) of this title shall establish appropriate standards for the financial institutions subject to their jurisdiction relating to administrative, technical, and physical safeguards—
(1) to insure the security and confidentiality of customer records and information;
(2) to protect against any anticipated threats or hazards to the security or integrity of such records; and
(3) to protect against unauthorized access to or use of such records or information which could result in substantial harm or inconvenience to any customer.[29]
The GLBA applies only to financial institutions, but requires protection for systems that store nonpublic personal information, such as customer databases, online banking, and brokerage systems.
The Payment Card Industry Data Security Standard (PCI DSS) prescribes monitoring for credit card data in the section, “Regularly Monitor and Test Networks.” In Section 10.6, it specifically requires “Review logs for all system components at least daily. Log reviews must include those servers that perform security functions like intrusion detection system (IDS) and authentication, authorization, and accounting protocol (AAA) servers (for example, RADIUS). Note: Log harvesting, parsing, and alerting tools may be used to achieve compliance with Requirement 10.6.” The PCI DSS requires that specific systems, including AAA servers, be monitored for abuse.
Some forms of compliance are voluntary and very specific to the industry in which the company operates. Though not mandatory, compliance with such guidelines is often required by executive management to avoid external scrutiny and lawsuits. The “North American Electric Reliability Council (NERC) Critical Infrastructure Protection Committee (CIPC) Security Guidelines for the Electricity Sector”[30] provides requirements for securing, both physically and electronically, critical systems for electric utilities. The guideline prescribes detailed security configurations and monitoring for any business system that must connect to a control system. This standard requires you to discover the systems connecting to your control systems, such as trouble ticketing or inventory systems, and monitor them for security breaches.
Companies that offer packaged information technology services are often bound to contract requirements for availability, integrity, and performance. Such companies must monitor their systems very carefully, to help ensure that contract requirements are met before their customers discover a contract breach and exercise their contractual privileges, which often include financial penalties.
In recent years, large companies have turned increasingly to Application Service Providers (ASPs) to offload application processing. A common requirement specified in such contracts includes security monitoring.[31] For sensitive applications and data, security monitoring is vitally important, and such contracts often require monitoring of specific segments or systems as part of the agreement.
Sensitive data is the most common and obvious place to target monitoring. Information may be considered sensitive because it is associated with an individual’s privacy, it has competitive value (intellectual property), or it has government-labeled handling requirements (classified information).
The thriving malware underground is fueled largely by the ability to steal, market, and sell the private information of individuals. This information has a market value because thieves can use it to create fake identities, giving them the opportunity to steal thousands of dollars from their victims via the victims’ bank, credit card, or brokerage.
With the advent of outsourcing and ASPs, it’s becoming feasible for companies to relinquish all responsibility for storing sensitive data about employees and customers. For companies that must maintain such systems, it should be fairly obvious which applications access such sensitive information. Recent legislation in many countries outlines the definition of PII and the required protections. It usually involves a unique personal identifier combined with other data, such as a passport number stored along with the person’s name. Here are examples of systems that commonly store PII:
Payroll systems, which often contain bank account information for direct deposit of paychecks, along with tax identification numbers and Social Security numbers
Human resources systems, which often contain Social Security numbers, immigration identifiers, and other unique identifiers for use in complying with employment law
Systems that access credit card details, such as customer databases and purchasing systems
Medical records systems, which contain information protected under the Health Insurance Portability and Accountability Act of 1996 (HIPAA), such as individuals’ health history
Since 2005, reports of hackers using social engineering techniques to steal competitive intelligence have repeatedly surfaced. These techniques have involved sending targeted trojans to individuals within the victim company (commonly known as spearphishing), planting “back doors” that are later used to steal the data. In 2006, for example, CERT/CC warned that “The stealthy attacks have frequently been sent to a specific person at the targeted organization and show that attackers are researching the best way to convince the victim that the document containing the Trojan horse is real.”[32] Data has also been stolen with more traditional attack techniques such as guessing weak passwords. SAP allegedly used such techniques in 2007, when its employees were accused of stealing volumes of Oracle’s software and support materials in an attempt to gain an upper hand in engaging customers.[33]
Companies should classify proprietary information and label it for restricted distribution. Such information represents the most critical secrets a company maintains, and it can include examples such as the following:
Product designs, including blueprints, schematics, software design specifications, and steps in a manufacturing process
Components and assembly instructions
Lists of customers, contacts, and order history
Sales figures and leads
Orders in process
Plans for mergers and acquisitions
Products/ideas under development
Patents not yet filed or approved
Don’t overlook the value of monitoring the computers and accounts of your senior executives. These systems are surely accessing highly privileged information, making them the likely targets of spearphishers.
Handling classified information (as controlled by official markings and procedures of a government agency, bound by law) requires special handling and protections. For example, the U.S. Department of Defense directive number 5220.22-M sets forth requirements described in the National Industrial Security Program Operating Manual (NISPOM).[34] This directive requires that all TOP SECRET and SECRET information be monitored with a NIDS. It also requires special monitoring for any system connected to a classified information system, and that such connections are made via a Controlled Interface (CI), described as follows:
8-702. Controlled Interface Requirements. The CI shall have the following properties:
a. Adjudicated Differences. The CI shall be implemented to monitor and enforce the protection requirements of the network and to adjudicate the differences in security policies.
Based on this requirement, a connection to a classified information system requires monitoring and enforcement to protect the information it contains. This serves as an excellent example of a system for which targeted monitoring is required.
Due to availability requirements and vendor packaging, some systems cannot be regularly patched (and some cannot be patched at all). These systems present an increased risk to the enterprise, and you should monitor them carefully. You can use preventive controls such as firewalls and intrusion prevention systems (IPSs) to augment their security, but for sensitive or critical systems, active security monitoring is a necessary tool to further reduce risk. For example, Supervisory Control and Data Acquisition (SCADA) systems are used to control and manage a nation’s critical infrastructure, including energy, water, transportation, and communication systems. In recent years, these systems have been converted to commodity operating systems and networks (such as Windows and TCP/IP), moving away from proprietary systems. Connections to SCADA systems from external networks have placed them in the line of fire for security threats. Weaknesses in these systems have been repeatedly demonstrated, and the role these systems play in critical infrastructure makes them extremely vulnerable to electronic warfare and terrorist attacks.
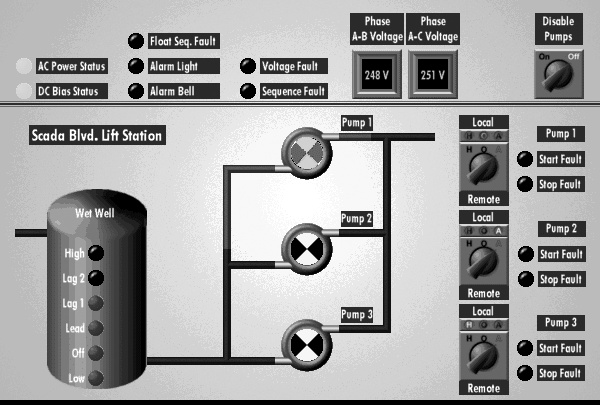
Figure 4-1 shows a screenshot from a SCADA water plant pumping system.
Figure 4-1. Screenshot from a SCADA water plant pumping system (see http://www.nordatasys.com/screens.htm)
SCADA systems are commonly plagued by three broad vulnerabilities, as described at a Black Hat Federal Briefing:[35]
- No authentication
These systems have automated components connected and running autonomously. This makes these systems ripe for worms and other self-replicating attacks.
- No patching
Commonly due to intolerance for downtime, these systems run for many years without interruption or attention for patching.
- No isolation/firewalling
As systems are interconnected and the network is extended, these systems are increasingly reachable via the Internet and other less-protected networks.
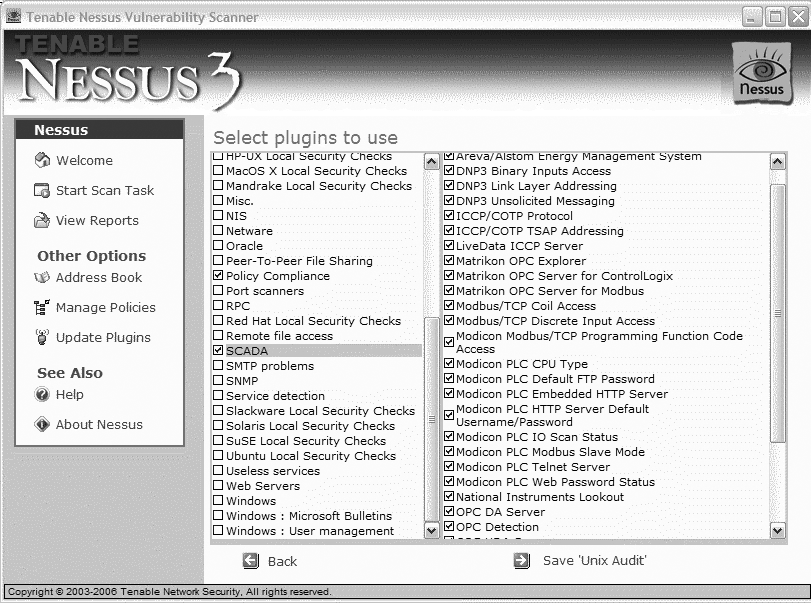
Because these problems are endemic to SCADA systems, security monitoring is required to mitigate the substantial risk they present. Some vulnerability scanning tools contain built-in SCADA probes, as illustrated in the Nessus screen capture in Figure 4-2.
An information technology security assessment (commonly called a risk assessment) is a focused study intended to locate IT security vulnerabilities and risks. The risk assessment normally includes an evaluation of both physical and technical risks, and uses personal interviews, vulnerability scans, and on-site observation to evaluate risk. Risk assessments are aimed at evaluating an organization’s compliance with a set of security standards. A common security framework used as a standard in such assessments is ISO 17799, which defines important administrative security guidelines for organizations.
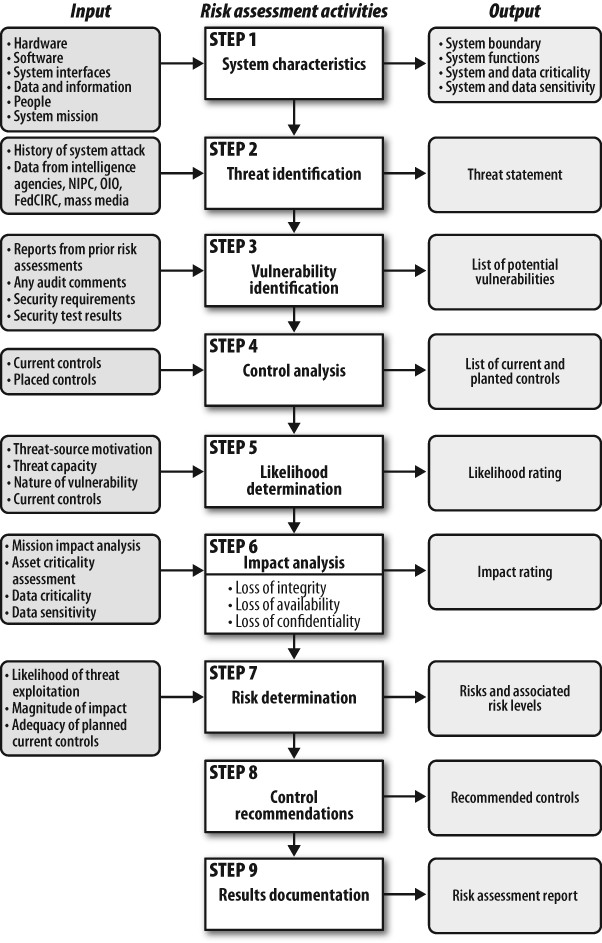
NIST Special Publication 800-30, “Risk Management Guide for Information Technology Systems,” describes nine steps for conducting information security risk assessments, as shown in Figure 4-3.
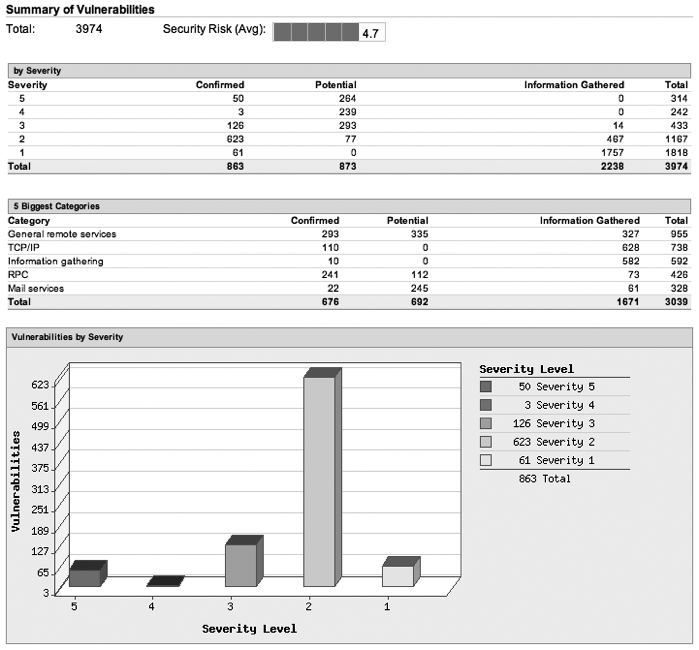
This process provides structured analysis of threats, vulnerabilities in deployed infrastructure, and available controls to produce a report of security risks (gaps) and recommended controls. Where recommended controls are considered too costly or impractical, security monitoring can often provide an acceptable alternative for mitigating security risks. In the security reviews I’ve conducted, business units have often been unwilling to implement strict controls to mitigate risk, fearing it will slow progress on time-sensitive projects. In those cases, I’ve required the business unit’s executive to accept the risk by signing a formal document explaining the risks of the project. This solution is effective for raising awareness, but it leaves the risks unmitigated. Security monitoring offers a unique compromise, allowing the business owner to mitigate risks by sponsoring targeted monitoring. Risk assessments commonly discover present risks via scans by specialized tools, producing reports similar to the Qualys report shown in Figure 4-4.
Your risk assessment should test compliance with your established policies, as described in Chapter 2. In addition, it should incorporate network address data, as described in Chapter 3, allowing you to aim specific tests according to where systems are placed on the network. For example, if your policy requires use of IT-sanctioned virtual private network (VPN) connections for all remote administration, you should audit the systems in the data center for rogue connections such as modems.
Your most visible systems are likely those exposed to the Internet, providing access to customers, shareholders, partners, and the press. This includes your company website, blogs, support tools, and other customer-accessible systems.
According to statistics from the 12th Annual Computer and Crime Survey,[36] website defacements have slightly increased in recent years, but remain a very small percentage of security incidents. Many companies are generating their content dynamically, even rebuilding their static content on a nightly basis. These advances seem to reduce the need for monitoring the static web content presented by your company. However, as noted in the sidebar, “A New Attack on Websites,” defacements are only one dimension of security threats for your static content.
Several tools and services can monitor for website defacements. These tools download each page and linked page, computing and storing a hash of the contents. They then periodically check the pages against the stored hash, calling out differences. Should the system discover a discrepancy, an administrator is notified to analyze the change and can then determine whether the change was authorized.
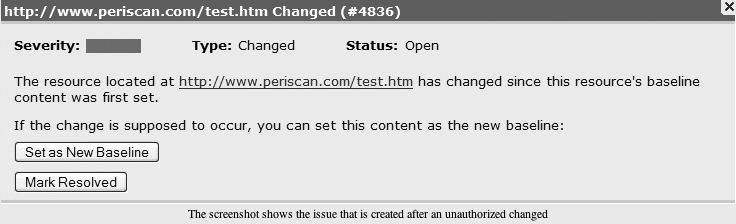
Site monitoring systems such as Catbird and Periscan (the latter shown in Figure 4-5) will watch your website for changes and alert you, allowing you to determine whether the change was authorized. For high-visibility systems such as your company’s website, these tools allow you to augment the security monitoring of traditional tools such as a NIDS.
[22] 24, “Episode 4×06: 12:00 P.M.–1:00 P.M.” Original air date: January 24, 2005. Trademark & © 2005 Twentieth Century Fox Film Corporation. Originally transcribed for TwizTV.
[24] OSDir Mail Archive, msg#00171: “False Positive in 2650.2 (ORACLE user name buffer overflow attempt).”
[25] Roberta Bragg. CISSP Training Guide (Que Publishing, 2002), pp. 454–458.
[26] Huseyin Cavusoglu, Birendra Mishra, and Srinivasan Raghunathan. “The Effect of Internet Security Breach Announcements on Market Value of Breached Firms and Internet Security Developers” (The University of Texas at Dallas School of Management, 2002), p. 14.
[29] U.S. Code Title 15,6801: Protection of Nonpublic Personal Information.
[30] NERC. Security Guidelines for the Electricity Sector (May 2005), p. 4.
[31] Cisco Systems. Evaluating Application Service Provider Security for Enterprises; http://www.cisco.com/web/about/security/intelligence/asp-eval.html (2008).
[34] National Industrial Security Program Operating Manual (NISPOM), DoD 5220.22-M, Section 5-307 (February 2006).
[35] RG & DM (X-Force Internet Security Systems). “SCADA Security and Terrorism, We’re Not Crying Wolf,” Black Hat Federal Briefings 2006.
[36] Robert Richardson. “2007 Computer Crime and Security Survey”; http://www.gocsi.com/forms/csi_survey.jhtml (March 2008).
[37] Provos, Mavrommatis, Rajab, and Monrose. “All Your iFrames Point to Us,” http://research.google.com/archive/provos-2008a.pdf (March 2008).
Get Security Monitoring now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.