Interception of radio communications has been a problem for as long as radios have been used to transmit sensitive information. Radio-based communication can be used to transmit instructions to troops during warfare, credit-card info from a cell phone, or passwords from a laptop to a remote web site. Since radio transmissions travel in unsecured areas, interception of these radio signals by an attacker is a real threat. In order to protect the data from eavesdroppers, various forms of encryption have been used to scramble the data. Sometimes these encryption mechanisms have been successful; other mechanisms have been compromised, thereby subverting the security of the data.
The 802.11 MAC specification describes an encryption protocol called Wired Equivalent Privacy (WEP). The goal of WEP is to make WLAN communication as secure as wired LAN data transmissions would be. If WEP were to meet this goal, it would allow network architects to deploy wired and wireless LANs interchangeably without regard to different security risks.
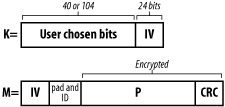
WEP provides two critical pieces to the wireless security architecture: authentication and confidentiality. WEP uses a shared key mechanism with a symmetric cipher called RC4. The key that a client is using for authentication and encryption of the data stream must be the same key that the AP uses. The 802.11 standard specifies a 40-bit key, however most vendors have also implemented a 104-bit key for greater security.
Encryption of the data stream provides confidentiality of the data transmitted between two WLAN devices. The encryption mechanism used in WEP is a symmetric cipher; this means that the key that encrypts the data is the same key that will decrypt the data. If both WLAN devices do not have the same encryption key, the data transfer fails.
When WEP is used for communication, the original data packet (P) is first checksummed (c). Then the checksum is added to the data to form the data payload. Then the transmitting device creates a 24-bit random initialization vector (IV). The device uses the IV and the shared key (K) to encrypt the data (EK,IV(P,c)) with the RC4 algorithm to create the ciphertext data. Figure 1-6 shows how a WEP encrypted packet is formed.
The device then transmits the ciphertext and the IV to the remote device. The remote device uses the IV that it received from the network and the shared key to decrypt the data and verify the checksum.
Tip
Some vendors claim to have 40-bit and 104-bit encryption. Other vendors claim to have 64-bit and 128-bit encryption. 40-bit and 64-bit encryption are actually the same thing. Some vendors treat the IV as part of the key, others do not. While the IV is technically part of the key that RC4 uses to encrypt the data, it is transmitted in the clear with the packet. Therefore it is not part of the secret key. The same goes for 104-bit and 128-bit encryption.
When a station associates with an AP, the station must authenticate itself to the AP. When the association occurs, the station and AP exchange the type of authentication they will accept. If the authentication type is specified as “open,” then there is effectively no authentication. The AP and station identify themselves to each other and the association is complete.
The devices may also select the “shared secret” authentication mechanism. Station Alpha will send a nonce (random number) to station Beta. Station Beta encrypts the random number using WEP and sends the result to station Alpha. Station Alpha decrypts the packet and verifies the decrypted payload equals the nonce it sent to station Beta. If the numbers match, then station Alpha notifies station Beta that the authentication was successful and the association is formed.
Get 802.11 Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.