Chapter 5. Leveraging Snowflake Access Controls
An organization’s data repositories may be filled with valuable, confidential information. Thus, securing and protecting this data is essential and is often a regulatory or statutory requirement. Though critical, the need for data security must be reasonably balanced against business needs for efficient data access. In other words, data access should not be so restrictive as to hobble a business’s ability to operate effectively and efficiently for the sake of security. Rather, the necessary data must be made available to just the right users at just the right time without sacrificing security. To achieve that balance, developing a good security model must encompass planning and involvement with the right stakeholders. Snowflake makes achieving this balance easy.
Creating multiple layers of security that take advantage of Snowflake’s built-in security options is among the best practices for managing security. The outer security layer (the outermost concentric square in Figure 5-1) relies on network policies, key pair authentication, multifactor authentication (MFA), and secure private networks as options to ensure that only authenticated users gain access to a Snowflake account. Snowflake provides data security protection through data encryption. Both of these outer layers of security are discussed in more detail in Chapter 7.
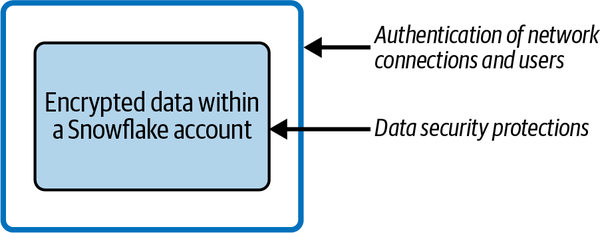
Figure ...
Get Snowflake: The Definitive Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

