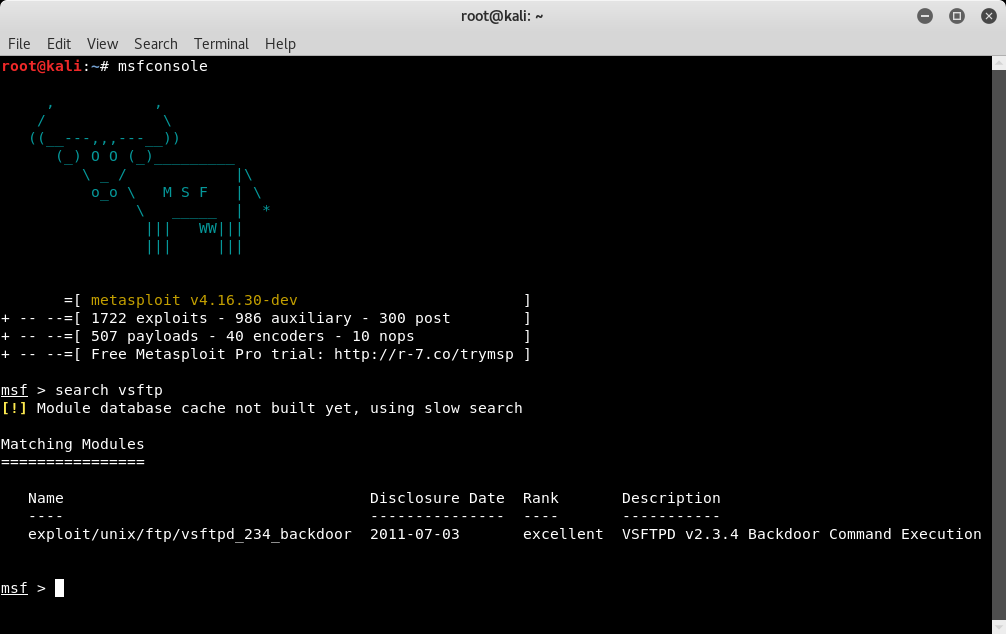
From the Nmap scan and enumeration, we got to know that our target is running an FTP server. The server version is vsftpd 2.3.4 and is active on port 21. We open the Metasploit framework using the msfconsole command and then search for any exploit matching vsftp as shown in the following image. Metasploit has an exploit vsftpd_234_backdoor which we can use to compromise the target.
We select the vsftp exploit and set the RHOST parameter as the IP address of the target. Then we run the exploit as shown in the following image. The exploit was successful and it opened up a command shell. Using the whoami command, we could know ...

