CHAPTER 2Gaining Initial Access
In Chapter 1, “Fulfilling Pre-ATT&CK Objectives,” we discussed how an attacker can perform reconnaissance and develop the resources required to carry out their attack. After planning the attack and putting those resources into place, the next logical step is to attempt to gain access to the target environment.
This objective is described in the Initial Access tactic of the MITRE ATT&CK framework. As shown in Figure 2.1, this tactic includes nine techniques that detail the various ways in which an attacker can achieve initial access.
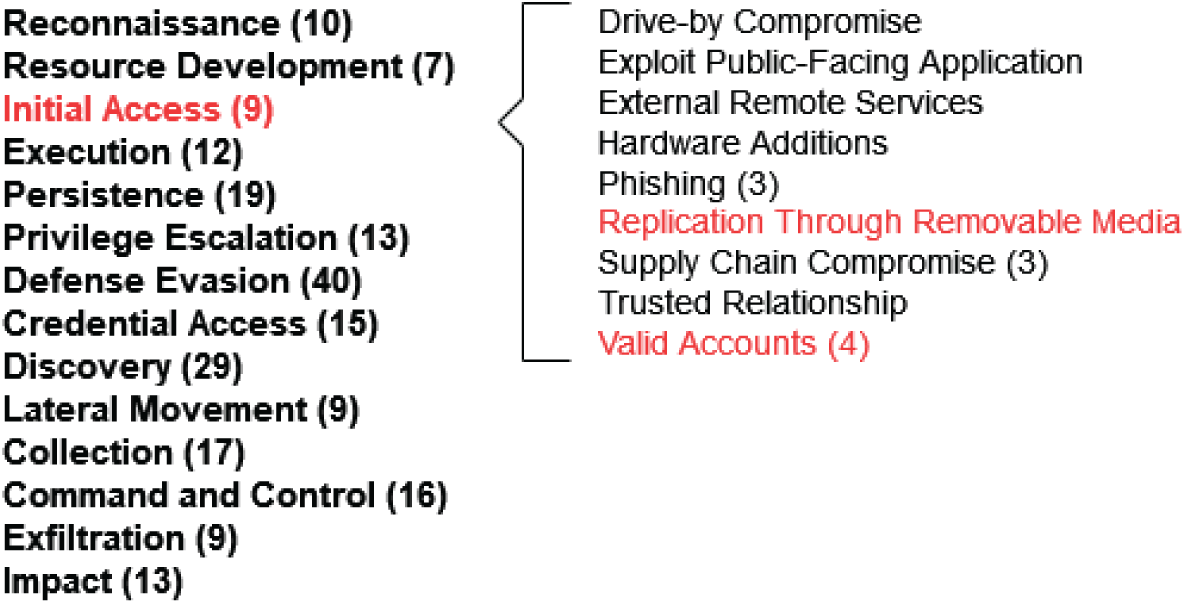
Figure 2.1: MITRE ATT&CK: Initial Access
In this chapter, we will focus on two of these techniques: Valid Accounts and Replication Through Removable Media. The sample Python code will demonstrate how Python can be used to set up or perform these attacks and also how defenders can use Python to defend against them.
The code sample archive for this chapter can be found at https://www.wiley.com/go/pythonforcybersecurity and contains the following sample code files:
TestDefaultCredentials.pyValidAccountDetection.pyAutorunSetup.pyAutorunDetection.py
Valid Accounts
The Valid Accounts technique of the Initial Access tactic takes advantage of the fact that user and machine accounts must exist on a target system. If an attacker can guess or otherwise learn the credentials of these accounts, they can easily gain access ...
Get Python for Cybersecurity now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

