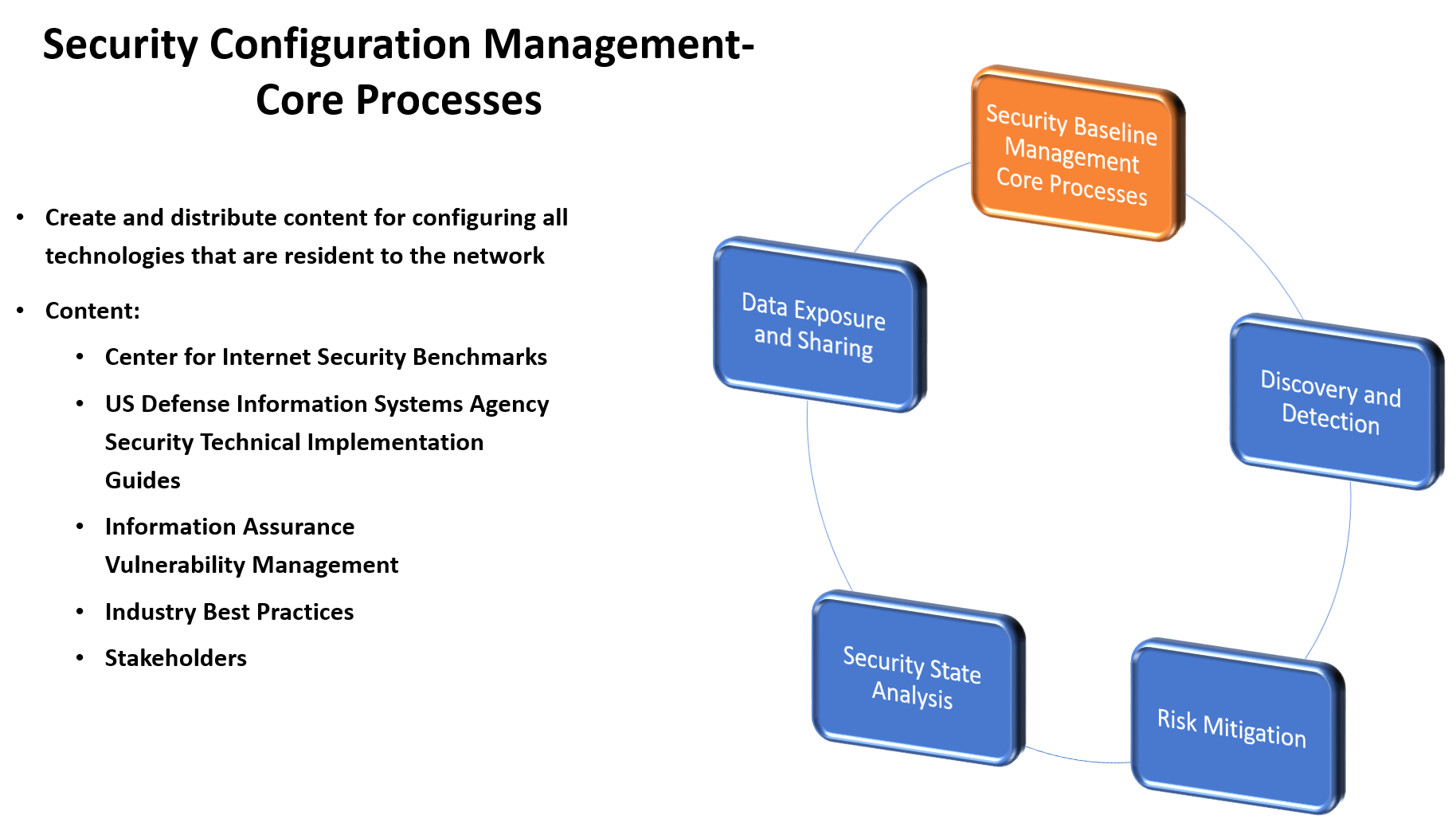
The Security Configuration Management service is responsible for:
- Developing the security baselines for all of the technologies that exist on the network
- Distributing the baselines to the applicable stakeholders
- Scanning and reporting for controls that are non-compliant to organizational standards
- Assisting is a risk in any exception request reviews