Let's understand how we can hack users of a website using browser exploits through the following diagram:
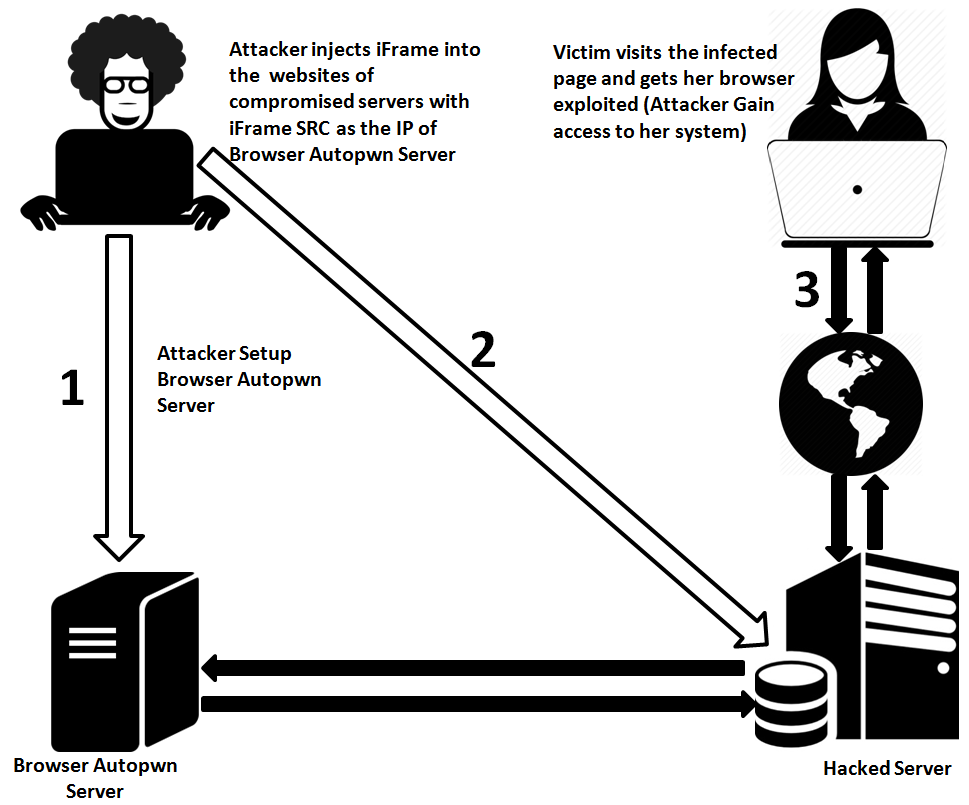
The preceding diagram makes things very clear. Let's now find out how to do it. But remember, the most important requirement for this attack is access to a vulnerable server with appropriate permissions. Let's understand more about injecting the malicious script through the following screenshot:

We have an example website with a web application vulnerability that allows us to upload a PHP-based third-party ...

