Chapter 4. Microsoft Azure Cloud Networking
Azure networking is essential to any public cloud; it allows us to bring both on-premise and cloud networks together. We can scale resources to meet our demands as well as protect our infrastructure; this gives us the flexibility to change to meet any resource demand that our organization or customer may need. With Azure networking, we get compliance and security. It also saves on costs and time which gives us the flexibility to adapt and meet our demands, both current and future.
Ryan O’Connell, IT Solutions Architect, Microsoft Azure MVP, Microsoft Certified Trainer, IT Manager, Blogger at RockITWorks
In Chapter 3, you learned about Azure compute services and their benefits for application development in Microsoft Azure. In this chapter we will deep dive into the concepts you need to learn to implement these compute services with the networking services in Azure. By the end of this chapter, you will have learned how you can use the appropriate networking service with existing applications. This will also help in planning networking and hybrid solutions in Azure.
Azure Networking
Azure Networking is a category of services in Microsoft Azure that provides fully managed and scalable networking and connectivity options like making a connection between your on-premises data center and the cloud. With networking services in Azure, you can also build secure virtual network infrastructure, manage your application’s network traffic, and protect your applications against DDoS attacks. Networking resources in Azure can also be used to enable secure remote access to internal resources within your organizations and globally route your network connectivity with monitoring and security features.
Using your Azure subscription, while logged in, you can view all of the Azure resources you can create in the networking category on the Azure Portal. You just need to click “Create a resource” and select the Networking category on the Azure Marketplace and there you can explore the rest of the networking resources offered by Microsoft and Microsoft Partners.
Azure Networking Services Categories
There are many networking services to choose from in Azure; they are categorized according to their purpose.
- Services for connectivity
-
You can use these Azure networking resources to create and build connectivity-related solutions in the cloud. For example, if you want to connect your Azure resources to your on-premises resources, you can use Azure Virtual Network (Azure VNet), ExpressRoute, Virtual WAN, Virtual Network NAT Gateway, VNet peering service, VPN Gateway, Azure Bastion, and Azure DNS.
- Services for application protection
-
These networking resources will help secure and protect your applications or systems in Azure. For example, you can implement networking services like Azure Load Balancer, Firewall, VNet Endpoints, Private Link, and DDoS protection.
- Services for application delivery
-
These services are ideal in use cases involving application delivery. Such networking resources include Azure Content Delivery Network (Azure CDN) for content delivery, global web traffic routing using Azure Front Door Service, load balancing your traffic across Azure regions globally using the Azure Traffic Manager, and other resources like Application Gateway and Internet Analyzer.
- Services for network monitoring
-
Monitor your network resources using any or a combination of these Azure networking services: Network Watcher, ExpressRoute.monitor, Azure Monitor, and VNet Terminal Access Point (TAP).
We’ll explore each of these categories in greater detail throughout the rest of the chapter to gain a better understanding of the different networking services for different use cases.
Azure Networking Services for Connectivity
Azure provides a network infrastructure that is robust, fully managed, and dynamic to support complex network architecture. These network solutions vary from creating public access to application network security and making hybrid connections between infrastructure on-premises and in the cloud.
Azure Virtual Network
Azure Virtual Network (Azure VNet) plays an important role in building networks within the Azure infrastructure. It is a fundamental component of keeping your Azure resources in a private network where you can securely manage and connect to other external networks (public and on premises) over the internet.
Azure VNet goes beyond the usual on-premises and traditional networks. Aside from the benefits of isolation, high availability, and scalability, Azure VNet helps secure your Azure resources by allowing you to administrate, filter, or route network traffic based on your preference.
For example, Azure VMs are connected or attached to an Azure VNet through virtual network interface cards (VNICs), as shown in Figure 4-1, where an Azure VM is attached to three NICs: Default, NIC1, and NIC2.
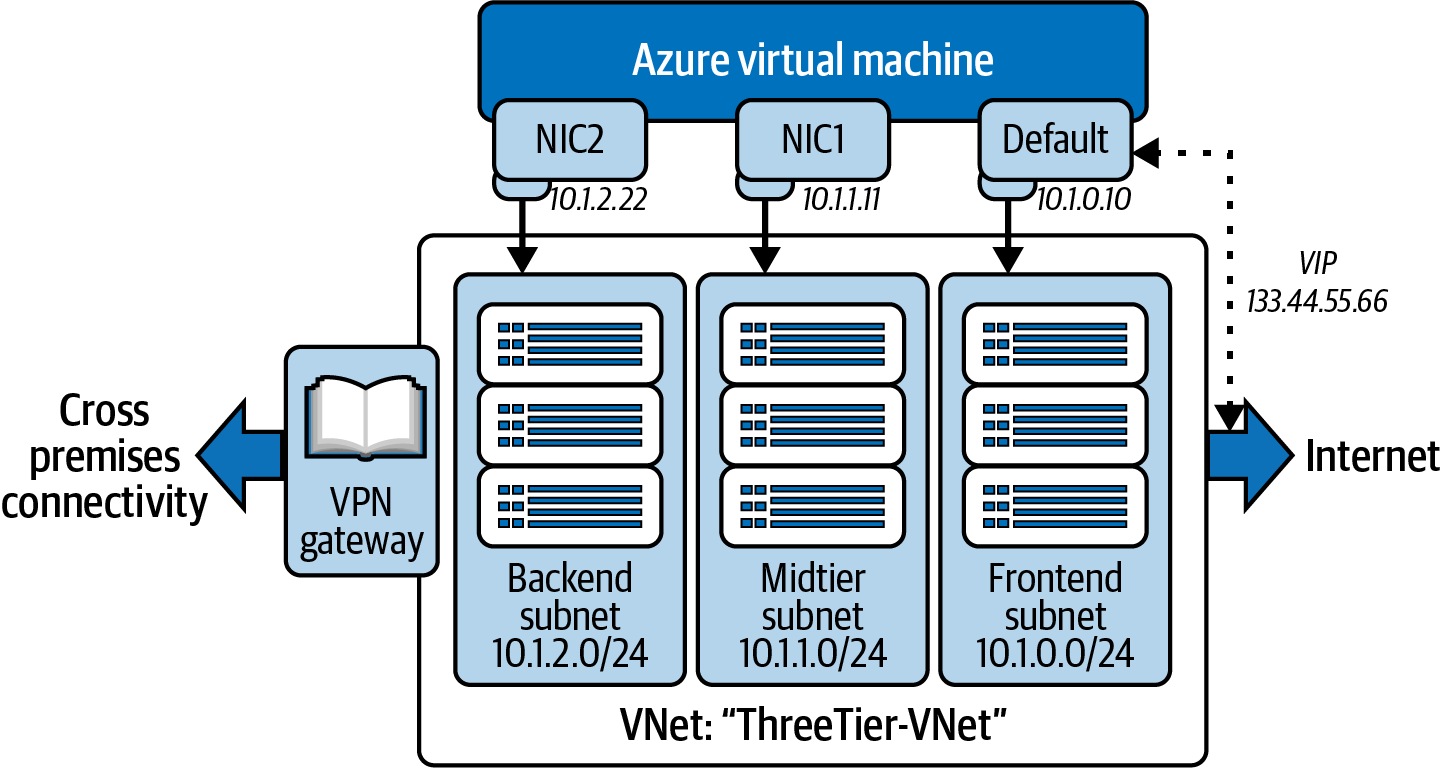
Figure 4-1. ThreeTier-VNet an Azure VM with several NICs
Azure resources need to securely communicate with each other internally on the private network, over the internet, and also networks on on-premises infrastructure. Azure VNet makes this possible. Let’s take a closer look at these forms of communication.
- Internet communication
-
Azure VNet by default is capable of communicating outbound to the internet. If you want to communicate to an Azure resource inbound, you may do that using an Azure public IP address or Azure Load Balancer that is set to public.
- Communication and connection with Azure resources
-
Azure resources can securely communicate through the virtual network and VNet peering and by extending virtual network service endpoints. For example, it is possible to deploy some dedicated Azure resources like AKS, Azure Batch, Azure SQL Manage Instance, Microsoft Entra Domain Services, Azure Container Instance (ACI), Azure Functions, Azure App Service Environments, and Azure VM Scale Sets within the same virtual network.
- Network traffic routing and filtering
-
The network traffic can be filtered between subnets in several ways. Network security groups (NSG) and application security groups can be used to control security rules (inbound and outbound) to control and filter network traffic. Another good option is to use a network VM where you can configure your firewall settings and network rules and optimize your WAN. On Azure Marketplace, you will find some networking appliance managers available for external services or within Microsoft.
Azure VNet Peering
Azure Virtual Network peering (VNet peering) allows you to connect several virtual networks in Azure. The connectivity and traffic between the VMs in the peered virtual networks uses Microsoft’s infrastructure on a secure private network. Virtual networks that are peered can directly share and connect with the resources located in either virtual network.
Currently, Azure supports both VNet peering and global VNet peering. The difference between these two is that global VNet peering connects virtual networks across Azure regions while VNet peering connects virtual networks within the same Azure region.
Figure 4-2 illustrates how VNet peering works between two virtual networks, VNet A and VNet B, that have several connections to other networking resources.
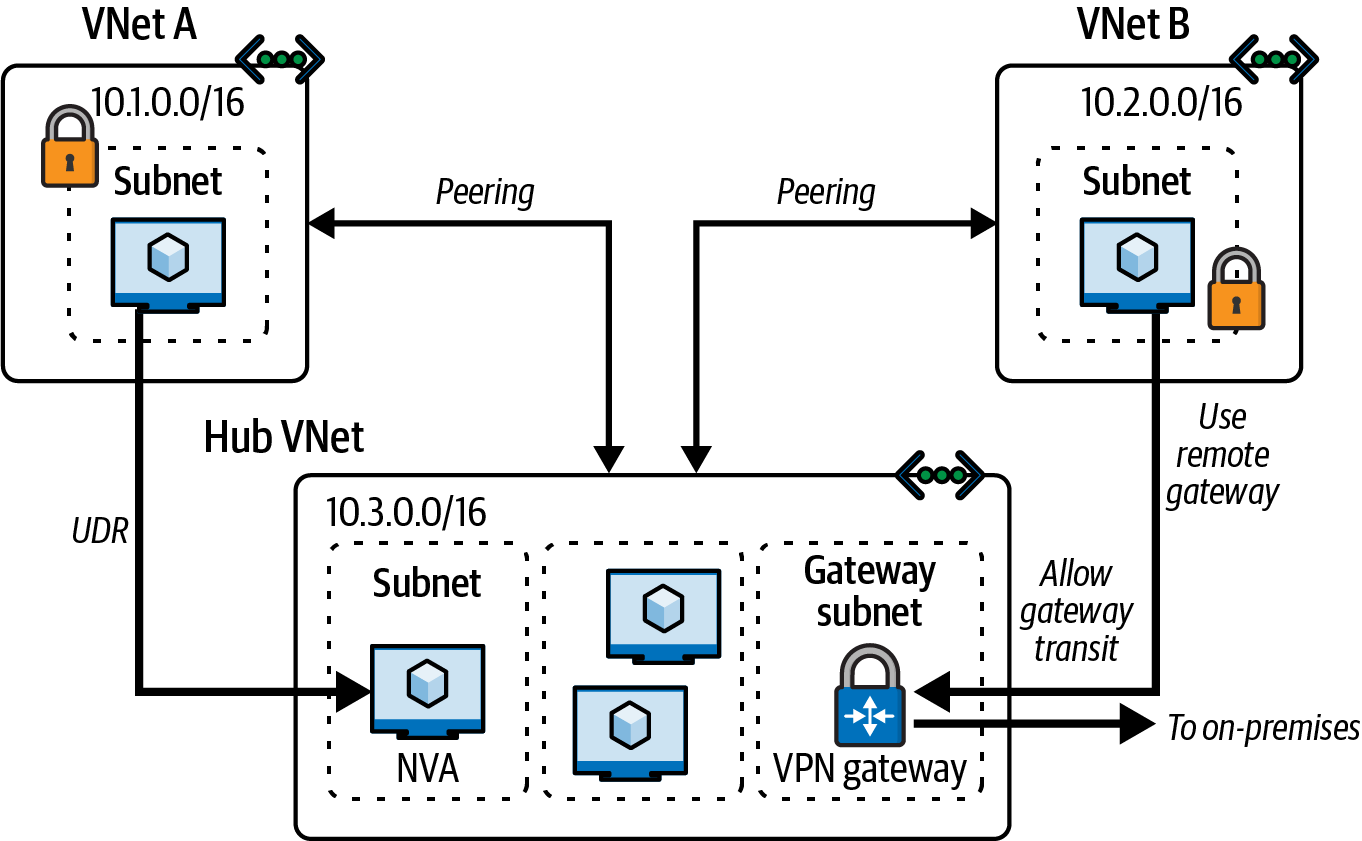
Figure 4-2. VNet peering in Azure
Both VNet peering and global VNet peering support gateway transit, a property in peering that allows a virtual network to use the peered virtual network’s VPN gateway for cross-premises connectivity or VNet-to-VNet connectivity. You can configure VPN gateway transit for VNet peering through Azure Portal, Powershell, ARM template, and Azure CLI.
Warning
Azure VNet peering issues can occur; therefore, troubleshooting is necessary to understand the root cause of the issue. One of the common troubleshooting questions to consider is whether the virtual networks are in the same subscription or not and if they are in the same region or a different region. For more details about different types of problems with VNet peering, please refer to Microsoft’s documentation on troubleshooting VNet peering issues.
On a final note, VNet peering uses IP addresses. There are two types of IP addresses that are used in Azure: public IP and private IP. The private IP addresses are used for the connectivity and Azure resource communication within the same resource group. On the other hand, public IP addresses are used to allow internet resources to communicate inbound to Azure resources. Using this type of IP address enables communication of Azure resources and public-facing Azure services over the internet.
Learn more in the Microsoft documentation about IP services and some recommended best practices for Azure Virtual Network.
Azure Virtual Wide Area Network
Azure Virtual WAN is a managed networking service and unified framework for networking, security, and routing features. The Azure global network enables Azure Virtual WAN to be available. It includes site-to-site, point-to-site VPN connectivity, ExpressRoute, etc.
Virtual WAN helps organizations or business units to connect to the internet and other Azure resources, for example, networking and remote user connectivity, which is effective and useful for those who prefer to work from home or other remote locations. It can also be used to move existing infrastructure or data center from on premises to Microsoft Azure with the help of utilizing Azure Virtual WAN.
Features of Azure Virtual WAN include:
-
Branch connectivity (via connectivity automation from Virtual WAN partner devices such as SD-WAN or VPN CPE)
-
Site-to-site VPN connectivity
-
Point-to-site VPN connectivity for remote users
-
Private connectivity using ExpressRoute
-
Intracloud connectivity for virtual networks
-
Interconnectivity using VPN ExpressRoute
-
Routing, Azure Firewall, and encryption for private connectivity
Azure Virtual WAN also has benefits like integrated connectivity solutions in the hub and spoke, automated spoke configuration, and troubleshooting and monitoring tools. When configuring it, you need Virtual WAN resources such as Virtual Hub, Hub VNet Connection, hub-to-hub connection, a hub route table, and site resources.
Figure 4-3 shows an example of Azure Virtual WAN being used and implemented for remote connectivity.
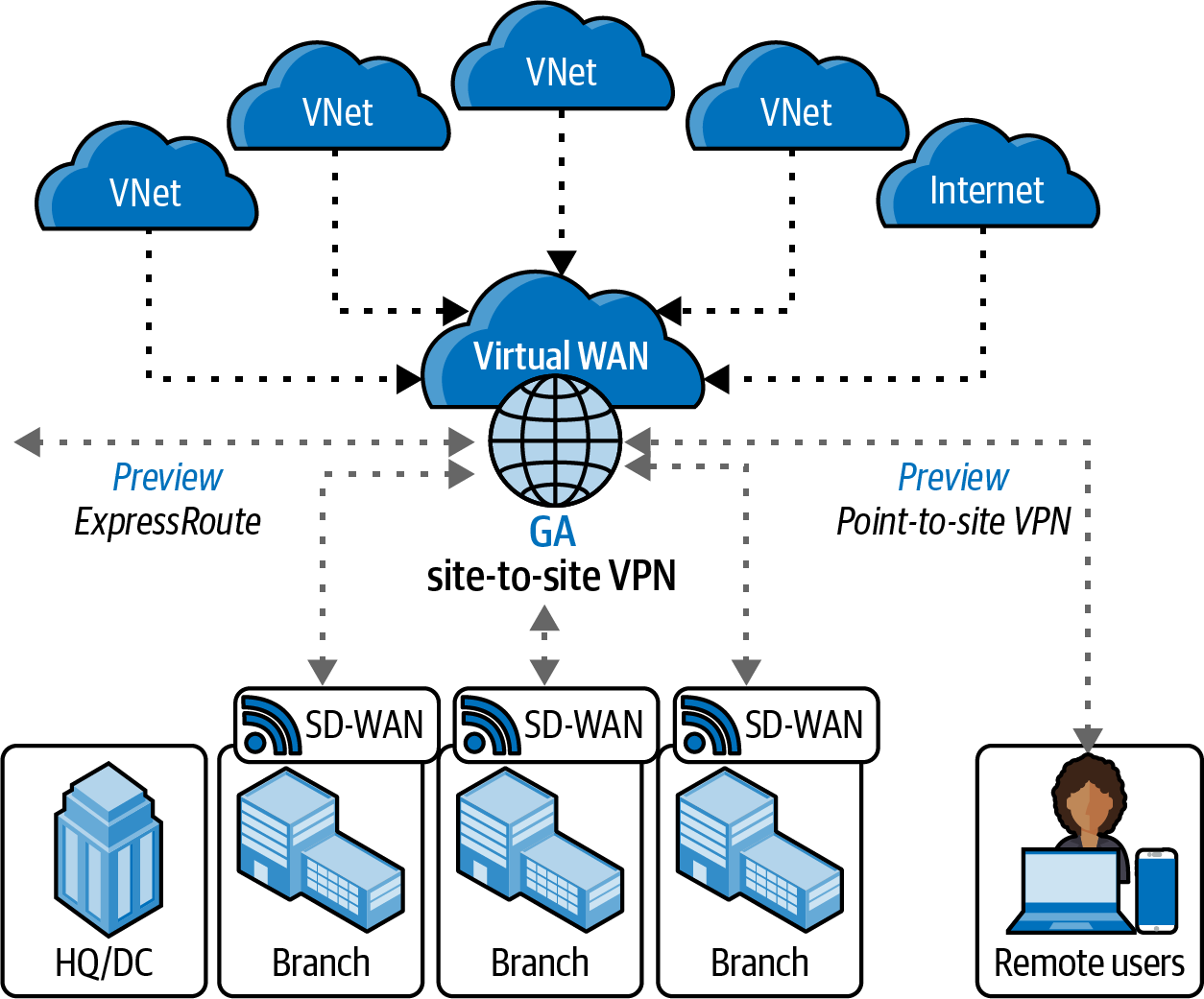
Figure 4-3. Azure Virtual WAN (adapted from an image by Microsoft documentation)
Tip
Each migration is unique; use the options and resources available to help you navigate your migration to Azure Virtual WAN.
Azure Virtual WAN is a broad and complex topic. For a deeper diver, see Microsoft’s Virtual WAN documentation.
Azure ExpressRoute
Azure ExpressRoute allows you to expand networks that are on premises into Microsoft’s cloud infrastructure using a connectivity provider over a private connection. Basically, this networking service enables connecting your on-premises networks with Azure. This connection between an on-premises network and Azure can be initiated using an any-to-any (IPVPN) network with Layer 3 connectivity, which enables you to interconnect with Azure to your own on-premises WAN or data center.
The connection in Azure ExpressRoute is private, and the traffic with this connection does not go over the internet. This means that the connections made using ExpressRoute promise speed, reliability, availability, and better security compared to connections over public networks.
A secure network connection can be established with other cloud resources in Microsoft like Microsoft 365, Dynamic 365, and Microsoft Azure, as shown in Figure 4-4.
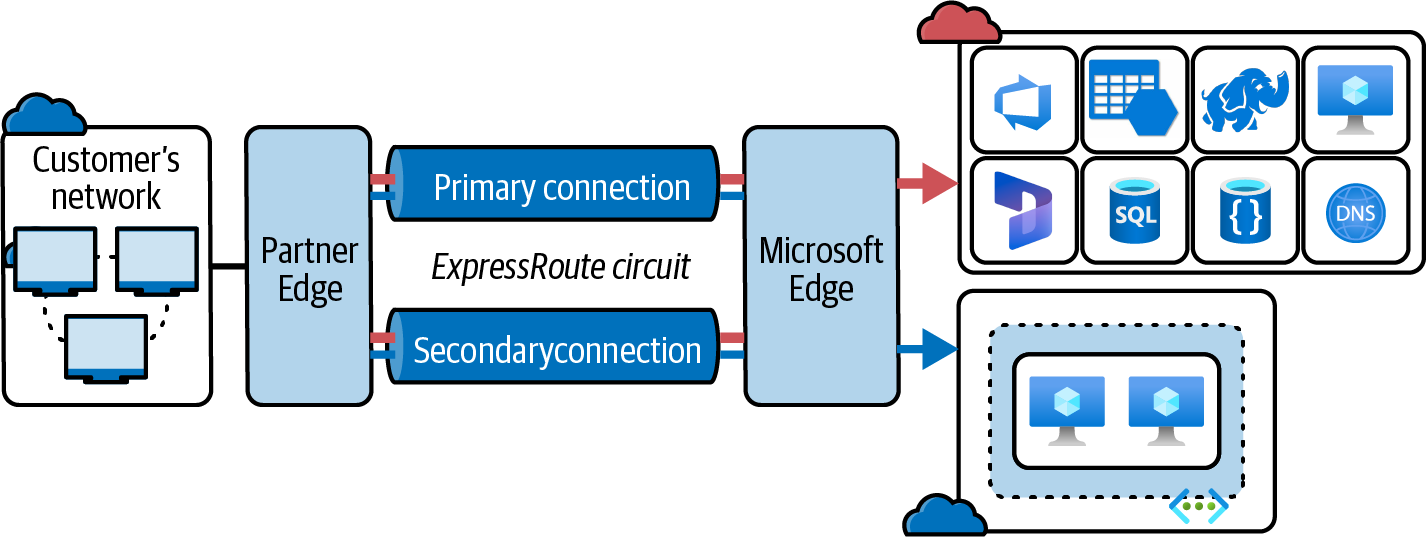
Figure 4-4. Azure ExpressRoute connections between public and on-premises networks (adapted from an image by Microsoft documentation)
ExpressRoute has several useful features such as support for different connectivity models between your on-premises network and Azure. As shown in Figure 4-5, these connectivity models can be implemented using service providers or directly. Service providers currently use three types of models: cloud exchange co-location, point-to-point Ethernet connection, and any-to-any (IPVPN) connection. ExpressRoute Direct can also be used for direct connection to Microsoft Azure.
ExpressRoute Direct is a good Azure service if you want to directly connect your network into Microsoft’s network globally at peering locations at up to 10 GBps or 100 GBps connectivity. You can create an ExpressRoute Direct connection through the Azure Portal, Azure CLI, and Azure PowerShell. Learn more about ExpressRoute Direct circuits, workflows, VLAN tagging, SLA, and pricing in the Microsoft documentation. Azure Storage can be integrated with ExpressRoute Direct if you have a use case that requires ingestion of data.
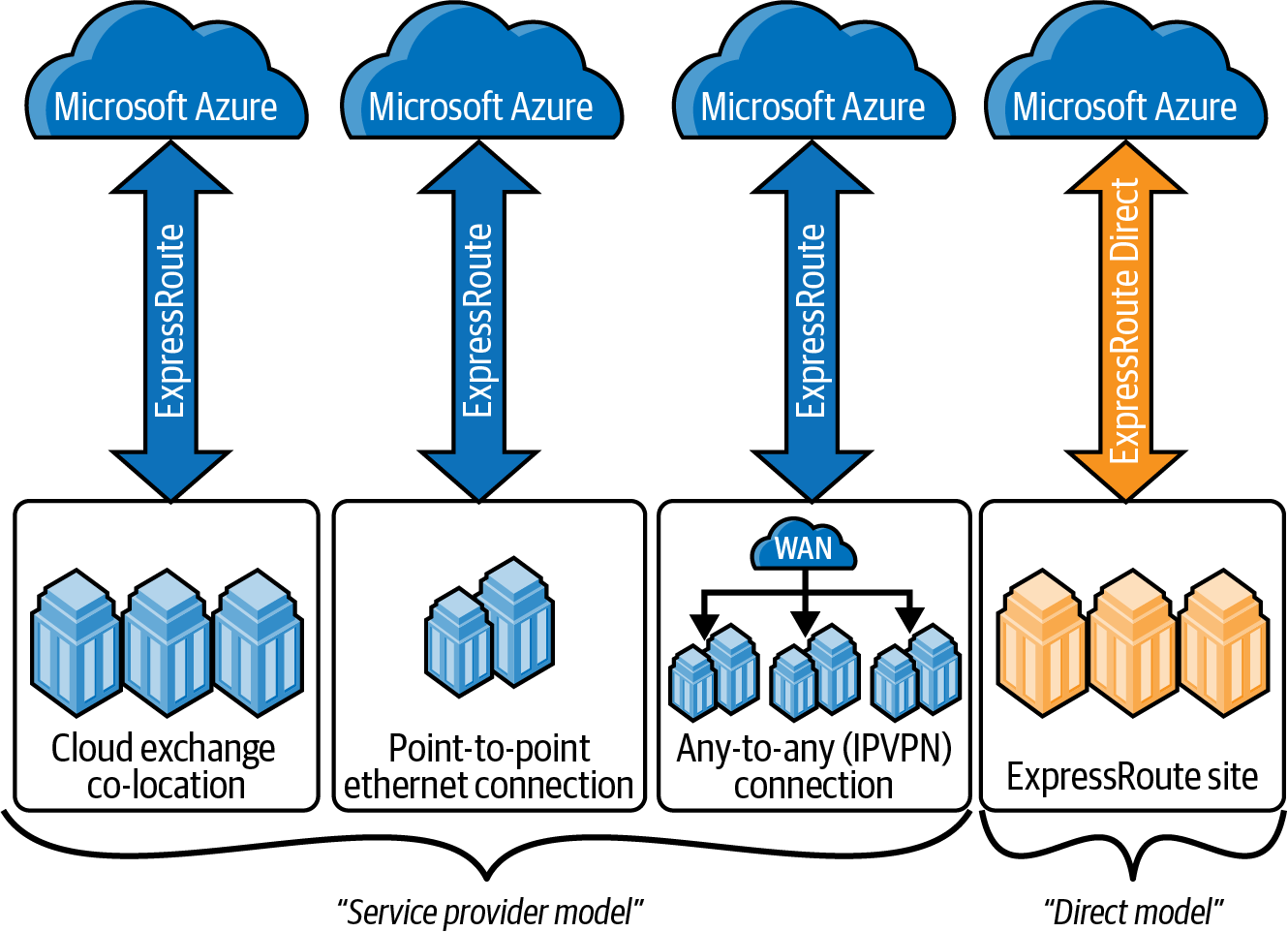
Figure 4-5. Different connectivity models of Azure ExpressRoute
Warning
When you configure and manage ExpressRoute, network address translations (NATs) are needed to connect to Microsoft cloud services. Connectivity service providers usually offer NAT management as a service. Otherwise, there are some NAT requirements for Microsoft peering and Azure public peering. There are also some ExpressRoute routing requirements that you need to be aware of.
Azure ExpressRoute has the option to implement private peering for Azure resources like VMs and Azure Virtual Desktop RDP Shortpath within the virtual networks.
Azure ExpressRoute Global Reach
In addition to the different connectivity models of Azure ExpressRoute for direct connection and service providers, there is another related networking service called ExpressRoute Global Reach, which is designed for scenarios like connecting an organization’s branch offices across the world.
For example, if your ExpressRoute service provider does not operate in certain locations or countries of your office branch, you may consider using the service provider locally in that location or country. Microsoft will be able to help connect your organization’s branch offices to the ExpressRoute service provider in your main office location using its global network.
The locations of ExpressRoute are the starting connection point to the globally distributed network infrastructure of Microsoft. Due to this capability ExpressRoute users are able to connect around the world using Microsoft’s network.
Azure VPN gateway
A VPN gateway is a specific type of virtual network gateway used to send encrypted traffic between an Azure virtual network and an on-premises location over the public internet. You can also use a VPN gateway to send encrypted traffic between Azure virtual networks over the Microsoft network. Each virtual network can have only one VPN gateway. However, you can create multiple connections to the same VPN gateway. When you create multiple connections to the same VPN gateway, all VPN tunnels share the available gateway bandwidth.
Different types of VPN gateway connections
To create a VPN gateway connection, we need to know the different configurations. These different types of connections will give you a clear overview and understanding on what is ideal based on what suits your business requirements.
- Site-to-site VPN (S2S)
-
The site-to-site (S2S) connection runs over the IPsec/IKE ((IKEv1 or IKEv2) VPN tunnel. IPsec VPN is one of the common VPN protocols used for establishing a VPN connection. The S2S VPN gateway connections can be hybrid or cross-premises use cases. This type of gateway also requires a VPN device that must be located on premises. This VPN device should have a public IP address designated to it.
- Point-to-site VPN
-
The point-to-site (P2S) type of VPN connection is applicable if you want to connect a client computer to a virtual network like Azure VNet. This type of VPN connection needs to be initiated from the client computer, which is useful for remote work.
- VNet-to-VNet (IPsec/IKE VPN tunnel)
-
Unlike the P2S VPN connection, the VNet-to-VNet connection is for connecting between VNets, even virtual networks on premises. This type of VPN gateway uses a secure connection through IPsec/IKE. Configuring for multiple site connections is also possible using this type of VNet-to-VNet connection.
- Site-to-site and ExpressRoute
-
The network traffic for the S2S VPN gateway is securely encrypted through the public internet. ExpressRoute also creates a private and direct connection from a WAN to Azure and other Microsoft services. This means that configuring ExpressRoute together with S2S VPN has advantages, especially if it is set for the same virtual network.
Note
The VNets you connect using VNet-to-VNet (IpSec/IKE VPN tunnel) connections can be in different or the same Azure regions, subscriptions, and deployment models.
One of the important steps when configuring the VPN gateway is choosing the appropriate type. A virtual network can have only one VNet gateway. For example, if you are configuring VNet gateway for VPN, then you would need to use -GatewayType Vpn and for ExpressRoute you would similarly use its keyword value. Check the guide for configuring VPN gateway settings and some requirements you need to know.
Azure NAT gateway for virtual networks
Azure Virtual Network NAT helps in simplifying the outbound internet connectivity for virtual networks (one or several subnets). Once a subnet is associated with a NAT gateway, the NAT gives the benefit of providing a source network address translation (SNAT). For example, you can utilize Azure NAT Gateway to securely connect to your VMs using dedicated public IP while having control over the ports you share. When a VNet NAT is configured on a subnet level, the outbound connectivity will use the specified static public IP addresses. Figure 4-6 illustrates how Azure VNet NAT gateway works with a VM with public IP. The Azure VMs in Subnet A have instance-level Public IP addresses but the VMs on Subnet B do not. The network traffic inbound are directed to Subnet A virtual machines that are still directed to an instance-level IP. However, all the outbound traffic from both Subnets A and B is routed through Azure NAT Gateway.
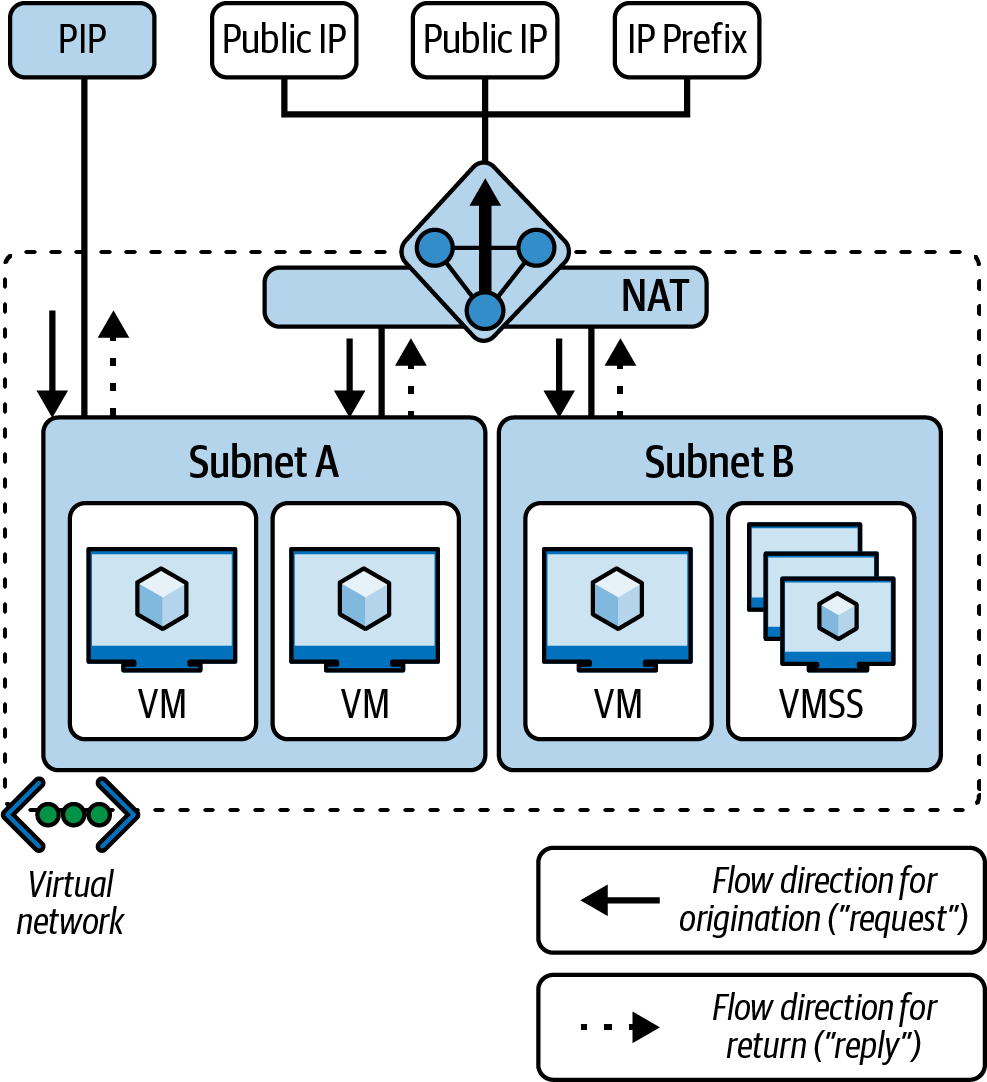
Figure 4-6. Instance-level Public IP with a VM and NAT
The following are some of the benefits of using Azure VNet NAT:
- Security and privacy
-
Azure VNet NAT gateway doesn’t need public IP addresses; therefore, the connection between virtual networks is fully private and secured. Resources can still connect to external resources outside the VNet even without public IP addresses.
- Scalability
-
All compute resources belong to a subnet. All subnets can communicate and use the same resource in the same virtual network. Automatic scaling is possible with the use of a public IP prefix, which assists in identifying and scaling how many outbound IP addresses are required.
- Resiliency
-
NAT does not have any individual dependency on other compute instances, which is the result of it being a distributed and fully managed service. This feature makes it very resilient as a software-defined networking service.
- Performance
-
The performance of a NAT gateway is satisfactory because it is a software defined networking service; when it is running it will not have a negative effect on network bandwidth.
Azure VNet NAT gateway provides the ability to control who has access to your organization’s resources and what locations they can be accessed from. For these reasons, NAT gateway can be useful for whitelisting a group of people working as contractors for a company.
NAT is not applicable or supported to work with basic public IP addresses and load balancers. If you need to use NAT gateway in your implementation, you would need to use standard versions virtual networks (one or several subnets). Once a subnet is associated with a NAT gateway, the NAT gives the instead or upgrade Azure Public Load Balancers to higher versions.
If you want to try designing a virtual network using NAT gateway, see the Microsoft documentation and a video about it from Azure Friday.
Azure Domain Name System
Azure Domain Name System (DNS) is a hosting service for DNS domains that provides name resolution using the Microsoft Azure infrastructure. By hosting your domains in Azure, you can manage your DNS records using the same credentials, APIs, tools, and billing as your other Azure services. You can’t use Azure DNS to buy a domain name. For an annual fee, you can buy a domain name by using App Service domains or a third-party domain name registrar. Your domains then can be hosted in Azure DNS for records management.
The following are some of the key features of Azure DNS:
- Reliability and performance
-
DNS domains in Azure DNS are hosted on Azure’s global network of DNS name servers. Azure DNS uses anycast networking. Each DNS query is answered by the closest available DNS server to provide fast performance and high availability for your domain.
- Security
-
Azure DNS is secured because it is linked to Azure Resource Manager, which is associated with user identity control services like Azure RBAC and Azure Resource Lock. Resource locking is used to prevent other users in your organization from accidentally deleting or modifying critical resources.
- Alias records
-
Azure DNS supports alias record sets. You can use an alias record set to refer to an Azure resource, such as an Azure public IP address, an Azure Traffic Manager profile, or an Azure Content Delivery Network (CDN) endpoint. If the IP address of the underlying resource changes, the alias record set seamlessly updates itself during DNS resolution. The alias record set points to the service instance, and the service instance is associated with an IP address. Also, you can now point your apex or naked domain to a Traffic Manager profile or CDN endpoint using an alias record.
Warning
Domain Name System Security Extensions (DNSSEC) are currently not supported in Azure DNS. However, a work-around alternative is using HTTP/TLS in the configuration of your applications. If your DNS zones require DNSSEC, host them externally through DNS providers.
By using Azure DNS, you host your own domain websites in Azure, manage your DNS records and integrate them with the resources hosted in Azure. If you have an existing domain, there are a number of ways to host it in Azure DNS. Microsoft has different guides for setting up your own custom domain on a function app, web app, blob storage, or other Azure resource.
Azure Bastion
The Azure Bastion service is a new, fully platform-managed PaaS service that enables secure VM connections without exposing the confidential ports of your network to the public Internet. It provides secure and seamless RDP/SSH connectivity to your VMs directly in the Azure Portal over TLS. When you connect via Azure Bastion, your VMs do not need a public IP address.
You can connect securely via RDP and SSH to all of the VMs in the virtual network where Azure Bastion is provisioned. By doing this, you are securely connecting to your VMs and are not exposing RDP/SSH ports to the public internet.
Key benefits and uses of Azure Bastion include:
- RDP and SSH directly in a web browser
-
Since Azure Basion uses an HTML5-based web client, you can access your VMs on any device. This means you don’t need to download a supported RDP or SSH client to connect to a VM. You can connect to your VMs securely using RDP and SSH sessions directly on any web browsers through the Azure Portal.
- Public IP not required on the Azure VM
-
Azure Bastion opens the RDP/SSH connection to your Azure VM using a private IP on your VM. You don’t need a public IP on your VM.
- Save time managing network security groups (NSGs)
-
Azure Bastion is hardened internally to provide you secure RDP/SSH connectivity. You don’t need to apply any NSGs to the Azure Bastion subnet. Because Azure Bastion connects to your VMs over a private IP, you can configure your NSGs to allow RDP/SSH from Azure Bastion only. This removes the hassle of managing NSGs each time you need to securely connect to your VMs.
- Protection against port scanning
-
VMs are secured and protected against port scanning by rogue and malicious users located outside your virtual network.
- Protect against zero-day exploits
-
Azure Bastion protects against zero-day exploits. A zero-day exploit is a cybersecurity attack that takes advantage of a security vulnerability. The term is also known as “0-day,” which means that the developer had 0 days to work on an update to fix the issue. Using anti-virus, firewall, and data protection tools can help avoid these security threats. You’ll learn more about zero-day exploits and cloud security on Azure’s cloud resources in Chapter 9.
Azure Bastion is a flexible and secure way to connect VMs on the go. To learn more, check out this video guide from Azure Friday.
Services for Application Protection
This section describes networking services in Azure that help protect your network resources. Using any or a combination of these networking services in Azure, you can secure your applications and workloads in the cloud.
Azure Firewall
Azure Firewall is a cloud-native intelligent network firewall security service that provides threat protection for your cloud workloads running in Azure. It’s a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability.
Following are the different types of Azure Firewall to help you identify which is right for your needs:
- Azure Firewall Standard
-
Azure Firewall Standard provides Layer 3 to Layer 7 firewall filtering and threat intelligence feeds from Microsoft Cyber Security. These threat feeds can be used to notify about any important alert and can even deny network traffic from/to any malicious domains and IP addresses to protect Azure resources against possible hacking or attacks.
- Azure Firewall Premium
-
Azure Firewall Premium provides advanced capabilities such as signature-based IDPS that enable detection of attacks by analyzing and detecting specific patterns, such as byte sequences in network traffic or any known malicious instruction sequences used by malware. This tier also supports third-party offerings available from WatchGuard, Sophos, Palo Alto, Check Point, and the like.
Warning
There are documented, known issues for both the standard and premium version of Azure Firewall. Note that the Azure Firewall tier names might change, so it is important to keep up with the recent updates on this security service on Azure.
Aside from the different Azure Firewall categories and tiers, you can centrally manage Azure Firewalls across multiple Azure subscriptions using Azure Firewall Manager. It supports setting up centralized security and route management. This firewall policy can be utilized by applying a common set of firewall rules in your network or application in your Azure tenant. Azure Firewall Manager supports firewalls in environments like VNets and Virtual WANs (Secured Virtual Hub).
Azure Firewall is an excellent choice to secure your Azure resources. The team behind Azure Firewall will continue to add features to both the standard and premium tiers.
Azure DDoS Protection
Azure DDoS Protection provides countermeasures against the most sophisticated DDoS (distributed denial of service) threats that can cause severe and highly impactful loss. It provides advanced DDoS mitigation features for your applications and resources.
Customers using Azure DDoS Protection also have access to support and communicate with DDoS experts using Azure DDoS Rapid Response during an active attack. An Azure DDoS Protection standard plan is a prerequisite to this support.
Figure 4-7 illustrates how Azure DDoS Protection works in securing an application gateway in a virtual network.
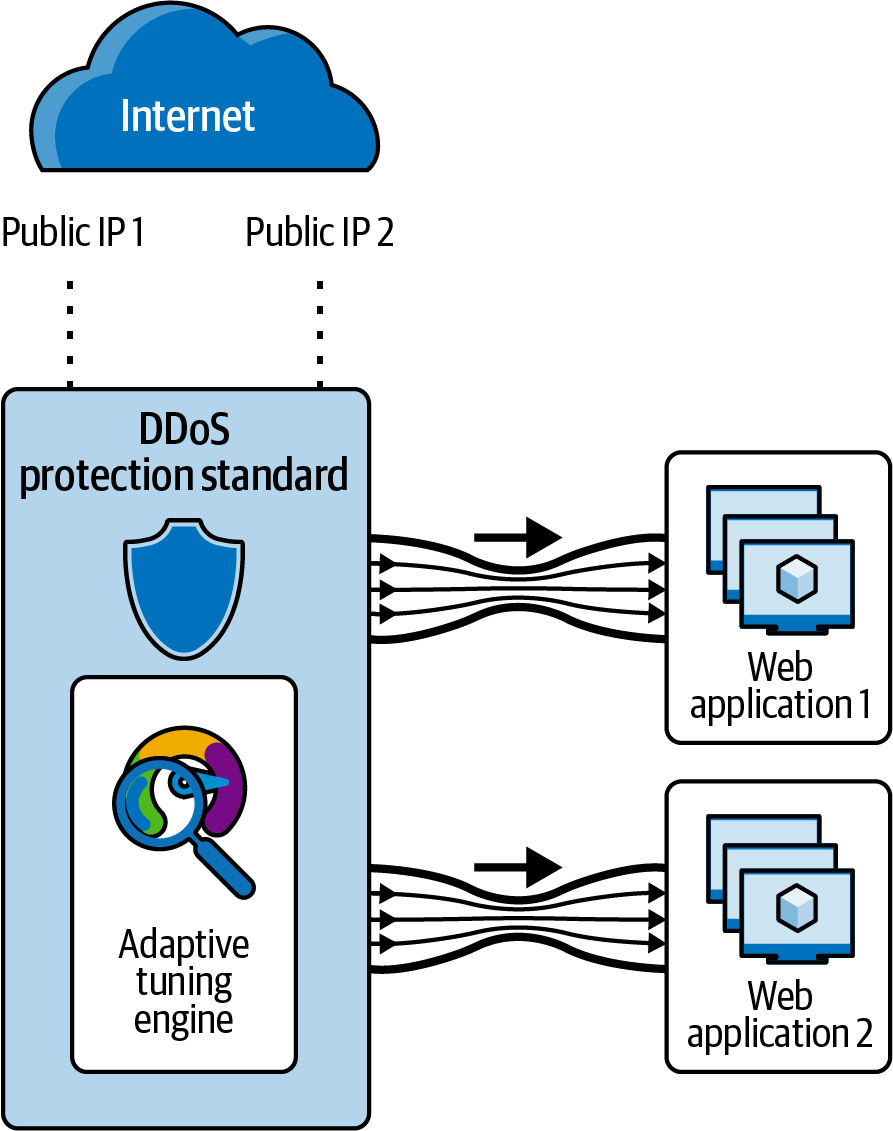
Figure 4-7. Azure DDoS Protection for a web application in a virtual network
Engineers with a role involving securing resources in Azure should learn the basic concepts of Azure security and protecting Azure resources from attacks. Check out Microsoft’s learning path for for an introduction to Azure DDoS Protection.
Azure Private Link
Azure Private Link enables you to access Azure PaaS Services (for example, Azure Storage and SQL Database) and Azure-hosted customer-owned/partner services over a private endpoint in your virtual network. Traffic between your virtual network and the service travels through the Microsoft backbone network. Exposing your service to the public internet is no longer necessary. You can create your own private link service in your virtual network and deliver it to your customers.
Web Application Firewall
Azure Web Application Firewall (WAF) provides protection to your web applications from common web exploits and vulnerabilities such as SQL injection and cross-site scripting. Figure 4-8 illustrates how Azure WAF works.
Azure WAF provides out-of-the-box protection from the Open Worldwide Application Security Project’s top 10 vulnerabilities via managed rules. Additionally users of WAF can also configure custom rules, which are customer-managed rules to provide additional protection based on source IP range, and request attributes such as headers, cookies, form data fields, or query string parameters.
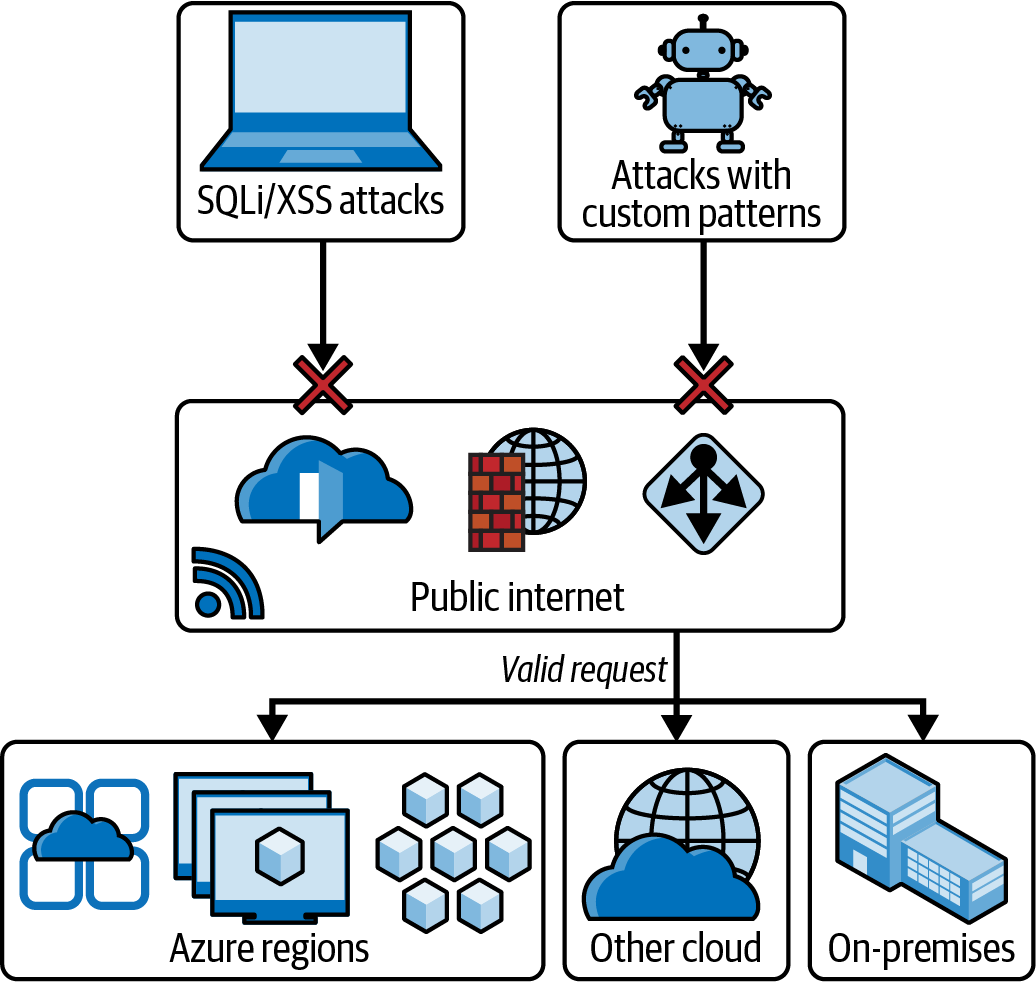
Figure 4-8. Azure Web Application Firewall
Users or Azure administrators can choose to deploy Azure WAF with Application Gateway, which provides regional protection to entities in public and private address spaces. It is also possible to deploy Azure WAF with Azure Front Door, which provides protection at the network edge to public endpoints.
Network security group (NSG)
Network security groups (NSGs) are built-in tools for network control that allow us to control incoming and outgoing traffic on a network interface or at the subnet level. They contain sets of rules that allow or deny specific traffic to specific resources or subnets in Azure. An NSG can be associated with either a subnet (by applying security rules to all resources associated with the subnet) or a network interface card (NIC), which is done by applying security rules to the VM associated with the NIC.
Figure 4-9 illustrates how NSGs are used at different levels to protect several VMs in different subnets in a virtual network.
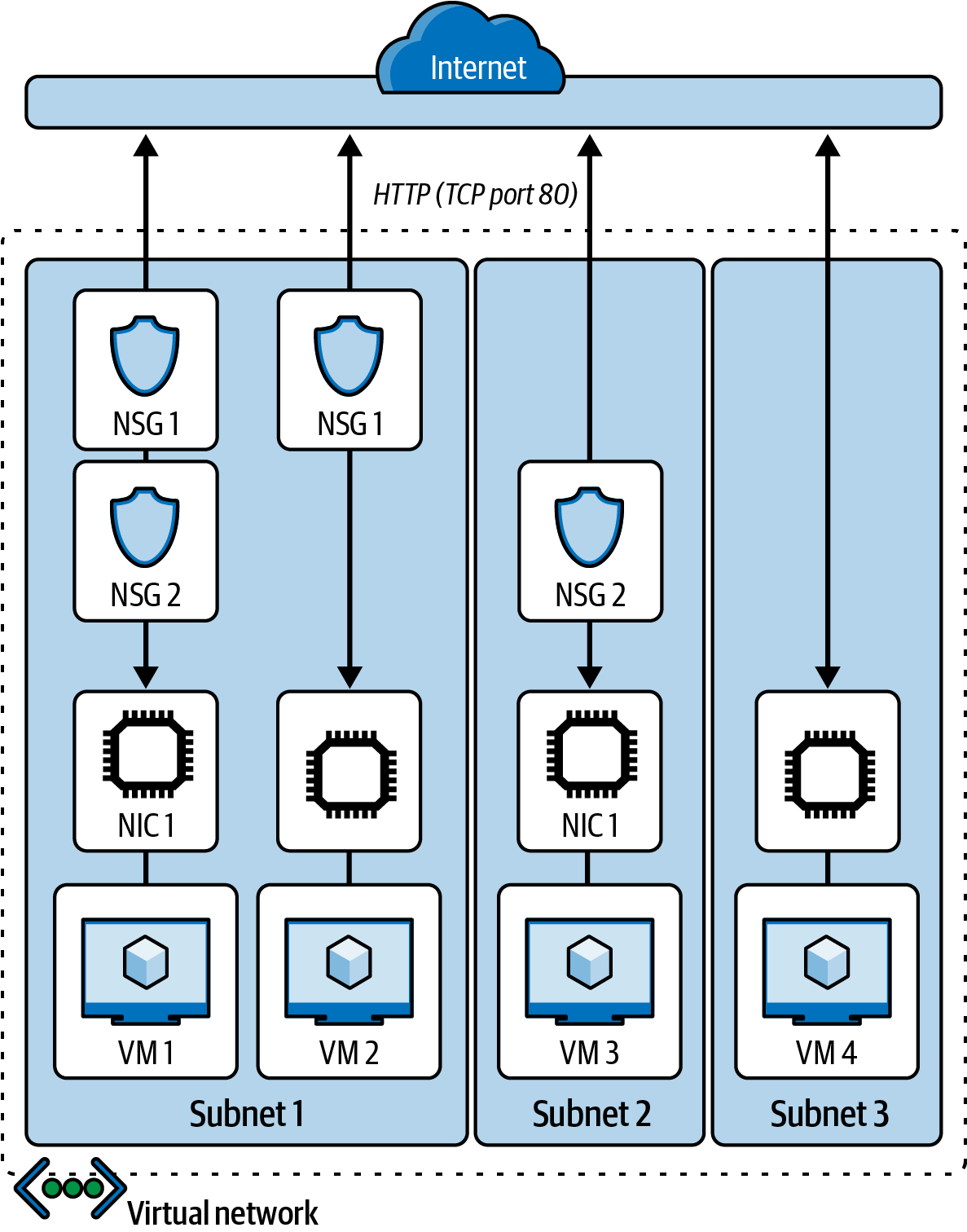
Figure 4-9. A virtual network protected with NSGs
Azure Load Balancer
Load balancing is a term commonly used for workload distribution across several computing resources. This process helps optimize the uses of resources, fix issues with response times, increase throughput, and prevent single resource overloading. Typically, load balancers can be public or internal. Public load balancer supports network traffic for your virtual machines by translating your private IP addresses to public IP addresses of your VMs. On the other hand, internal load balancers support load balancing inside your virtual network. If you have a hybrid infrastructure as a setup, this type of private load balancing is also possible with a frontend load balancer. In Azure, services for load balancing include Azure Load Balancer, Traffic Manager, Azure Front Door, and Application Gateway.
Azure Load Balancer is a load-balancing networking service that distributes traffic across multiple VMs (Azure VMs) or a group of resources in a single Azure region. This resource is best known for its performance with ultra-low latency. The algorithm for Azure Load Balancer uses a tuple-based hashing distribution, which means that the tuple hashes itself on the bases of its elements.
Figure 4-10 shows a 5-tuple hash (source IP, source port, destination IP, destination port, and protocol type) that is mapped to the traffic to any available servers.
The hash-based and source IP affinity are both supported in the Azure Load Balancer service. This means you have the option to set up the configuration of your preferred distribution mode for traffic distribution.
Key uses of Azure Load Balancer
Azure Load Balancer is a powerful resource for creating applications that are highly available and scalable for inbound and outbound connections.
Uses and benefits of using the standard Azure Load Balancer include:
-
Improve the distribution of Azure resources with better availability
-
Configure connectivity and load balancing of Azure VMs for incoming and outgoing traffic
-
Monitor Azure resources that are being load-balanced and distributed by the Azure Load Balancer
-
Require port forwarding, load-balance with IPv6, multiple ports or IP addresses
-
Ability to migrate load-balancing resources across different Azure regions
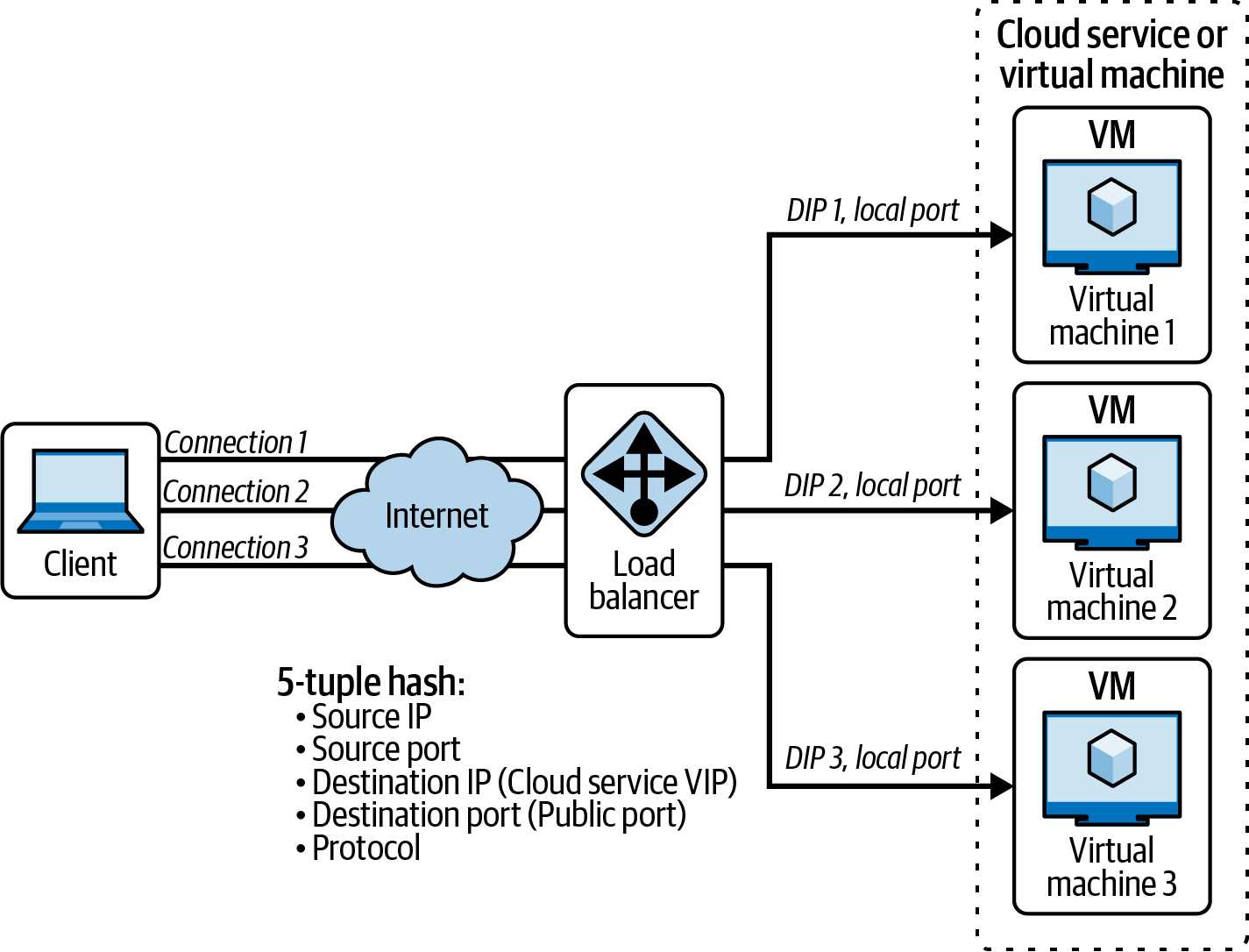
Figure 4-10. Azure Load Balancer with 5-tuple hash distribution
The load balancer operates in the Open Systems Interconnection (OSI) model at Layer 4, which distributes traffic based on protocol, source IP address and port numbers, and destination IP address and port. The main purpose of the load balancer is to distribute the inbound flows from both backend and frontend pool instances.
The Azure Load Balancer components are described in Table 4-1; a few key components can be configured in your Azure subscription on the Azure Portal. You also have the option to configure using other Azure tools like Azure PowerShell, Azure CLI, or ARM templates.
| Component | Description |
|---|---|
Frontend IP configuration |
The IP address (public or private) you set on a load balancer will be your client’s access point. The type of load balancer depends on what kind of IP address you have. For example, the private IP address is for the internal load balancer while the public IP is for the public load balancer. |
Backend pool |
It is generally recommended to add more instances to the backend pool to cost-effectively scale and handle the high demands of incoming traffic. To optimize operations, it is worth considering designing for the least number of individual backend pool resources. |
Load balancer rules |
A load balancer configured with protocol -all and port -0 is known as following the high availability (HA) port rule. This rule enables a single rule to load-balance all TCP and UDP flows that arrive on all ports of an internal Standard Load Balancer. The HA port’s load-balancing rules help with critical scenarios, such as high availability and scale for network virtual appliances (NVAs) inside virtual networks. |
Health probes |
A health probe is used to determine the health status of the instances in the backend pool. During load balancer creation, configure a health probe for the load balancer to use. This health probe will determine if an instance is healthy and can receive traffic. |
Inbound NAT rules |
An inbound NAT rule forwards incoming traffic sent to a frontend IP address and port combination. The traffic is sent to a specific VM or instance in the backend pool. Port forwarding is done by the same hash-based distribution as load balancing. |
Outbound rules |
An outbound rule configures outbound NAT for all VMs or instances identified by the backend pool. This rule enables instances in the backend to communicate (outbound) to the internet or other endpoints. |
High availability ports |
The HA ports load-balancing rules help you with critical scenarios, such as high availability and scale for NVAs inside virtual networks. The feature can help when a large number of ports must be load-balanced. |
Tip
If you need to set up load balancers in more than one frontend, you can also configure it for multiple frontends. Check out Microsoft’s guide for multiple frontends for Azure Load Balancer
To learn more about which load-balancing network service is suitable for specific scenarios, check out this discussion about reviewing network options and identifying requirements for workload networking.
There are several load-balancing options in Azure; the load-balancing decision tree guide provided by Microsoft is shown in Figure 4-11. You can also read the details of this flowchart in Microsoft’s guide for load-balancing options.
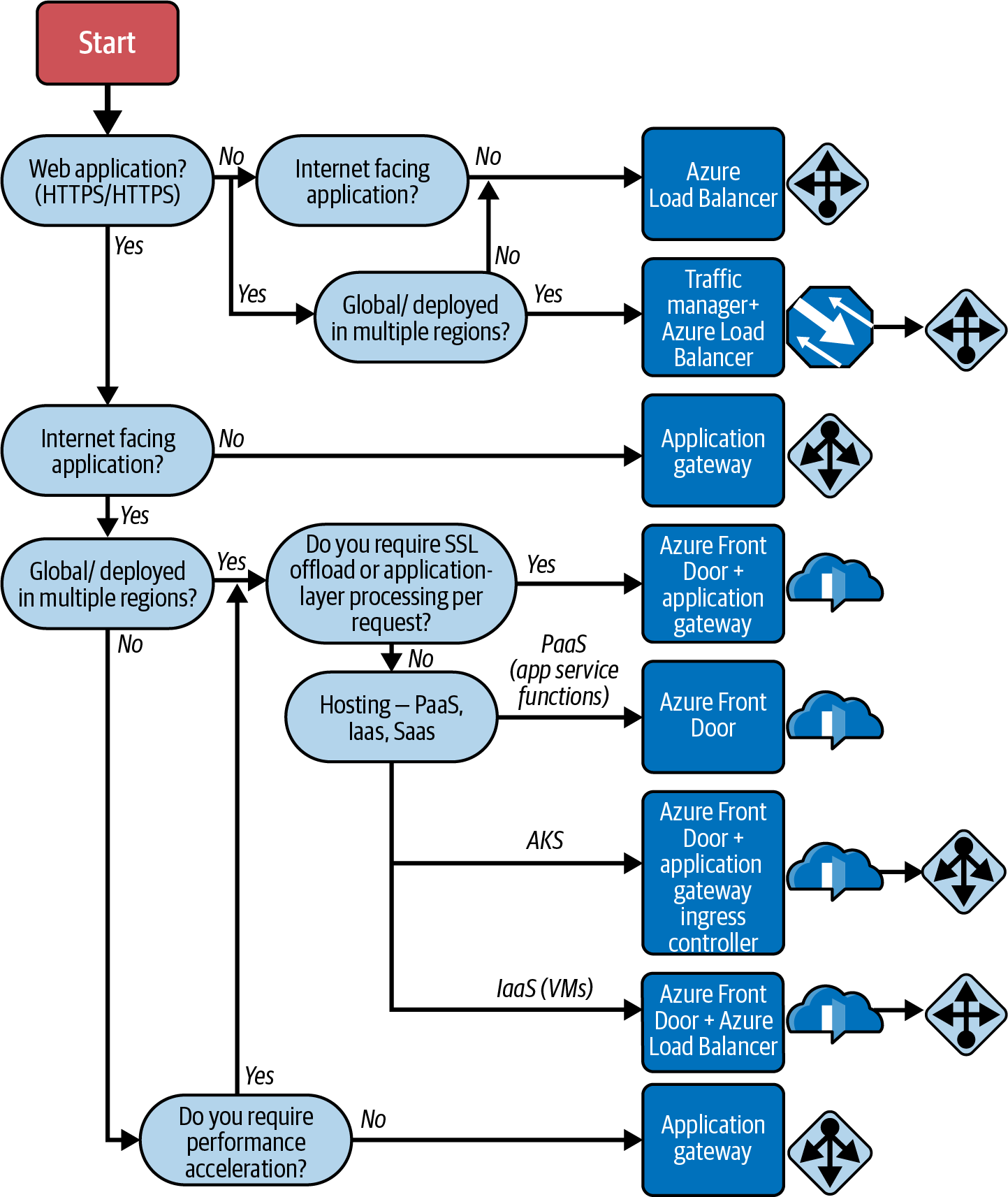
Figure 4-11. Microsoft’s decision tree guide for load-balancing options (adapted from an image by Microsoft documentation)
Each application can have different implementations and can consist of multiple workloads. Each workload needs to be evaluated separately.
Azure Networking Services for Application Delivery
Application delivery is another category of Azure networking services. Azure networking services like Azure Front Door, Azure CDN, Azure Balancer, etc., will help speed up delivery and user experience on your cloud-hosted applications globally.
Azure Front Door
Azure Front Door is a global, scalable entry point that uses the Microsoft global edge network to create fast, secure, and widely scalable web applications. With Front Door, you can transform your global consumer and enterprise applications into robust, high-performing personalized modern applications with content that reaches a global audience through Azure.
With the Azure Front Door service, the content on your applications will be delivered quickly to your application users wherever they are located. This service uses Microsoft’s global edge network that interconnects to many points of presence (POPs) distributed around the world.
With Front Door you can develop, operate, and scale your dynamic web applications and even static content. It also allows you to configure, manage, and monitor the global routing for your web traffic by optimizing for top-tier end-user performance and reliability through quick global failover.
Following are additional key benefits and uses of Azure Front Door:
-
Cookie-based session affinity, which is useful for keeping a user’s session active on the same device or server
-
SSL offloading and certificate management
-
Custom domains if you want to configure your own domains
-
Integration with Web Application Firewall (WAP) for security
-
HTTP/HTTPS redirection helps ensure that the connection between your web client and server are secured and encrypted
-
URL rewrites and custom redirection
-
Smart monitoring for resources in the backend that will help track and debug issues
-
Multiple website hosting and support for wildcard domains
-
End-to-end IPv6 connectivity and HTTP/2 protocol support
There are different tiers to choose from: Azure Front Door Standard and Azure Front Door Premium. For more details about the different tiers, see Microsoft’s guide for Azure Front Door tiers.
Azure Application Gateway
Azure Application Gateway is a load balancer for web traffic. It enables you to manage and control the traffic to your web applications. It is an application delivery controller (ADC) as a service that supports several Layer 7 load-balancing capabilities for your applications.
Microsoft’s Azure Application Gateway is ranked #3 in application delivery controller solutions based on a Peerspot.com ranking survey.
Features of Application Gateway include:
-
Support for autoscaling (scale up and scale down) based on the ongoing traffic load of your application
-
SSL/TLS termination at the gateway to secure unencrypted traffic to servers
-
Zone redundancy and support for multiple availability zones to ensure high availability and fault tolerance
-
URL-based routing, multiple site hosting and redirection
-
Protection and security using Web Application Firewall (WAF)
-
Use as an ingress controller for an Azure Kubernetes Service (AKS) cluster
-
Integration with Azure Monitor for monitoring, logging, and insights
Azure has several fully managed load-balancing solutions that suit different use cases or needs. Azure Load Balancer is an alternative if you want to do load balancing at the network layer level. There’s also Azure Front Door for optimizing global routing of web traffic and Azure Application Gateway if you need server load balancing at the application layer.
Azure Traffic Manager
The Azure Traffic Manager is a DNS-based traffic load balancer. This networking service allows you to effectively distribute traffic to your public-facing applications across the global Azure regions. Traffic Manager also provides your public endpoints with high availability and quick responsiveness.
Key benefits of Azure Traffic Manager include:
- Integrate and associate hybrid applications
-
Traffic Manager supports external, non-Azure endpointss enabling it to be used with hybrid cloud and on-premises deployments, including “burst-to-cloud,” “migrate-to-cloud,” and “failover-to-cloud” scenarios.
- Improve availability, maintainability, and performance
-
Azure Traffic Manager promises to deliver high availability for critical applications by monitoring endpoints and automatic failover if an endpoint goes down. You can have planned maintenance done on your applications without downtime. Traffic Manager can direct traffic to alternative endpoints while the maintenance is in progress. It also can help improve your application’s performance by directing web traffic to the endpoint with the lowest latency.
- Manage complex traffic distribution and advanced deployments
-
By using Nested Traffic Manager profiles, you can use multiple traffic-routing methods to create flexible rules to scale to the demands of more complex and larger deployments.
Note
Priority, Weighted, Geographic, Performance, MultiValue, and Subnet are the traffic-routing methods supported by Azure Traffic Manager. These routing methods are used to check how network traffic is routed to different service endpoints.
Figure 4-12 shows how Azure Traffic Manager can be used to direct a web application’s client request to a specific endpoint based on the traffic-routing method being configured.
Warning
Azure Traffic Manager and Azure Front Door have similarities and differences. For example, for routing options, Traffic Manager uses on-premises routing at the DNS layer, while Azure Front Door works with HTTP requests, which have independent scalability. Traffic Manager works with any protocol like UDP, TCP, HTTP, and more. However, Front Door uses HTTP acceleration, which means that its traffic is on a proxy on Microsoft’s edge network.
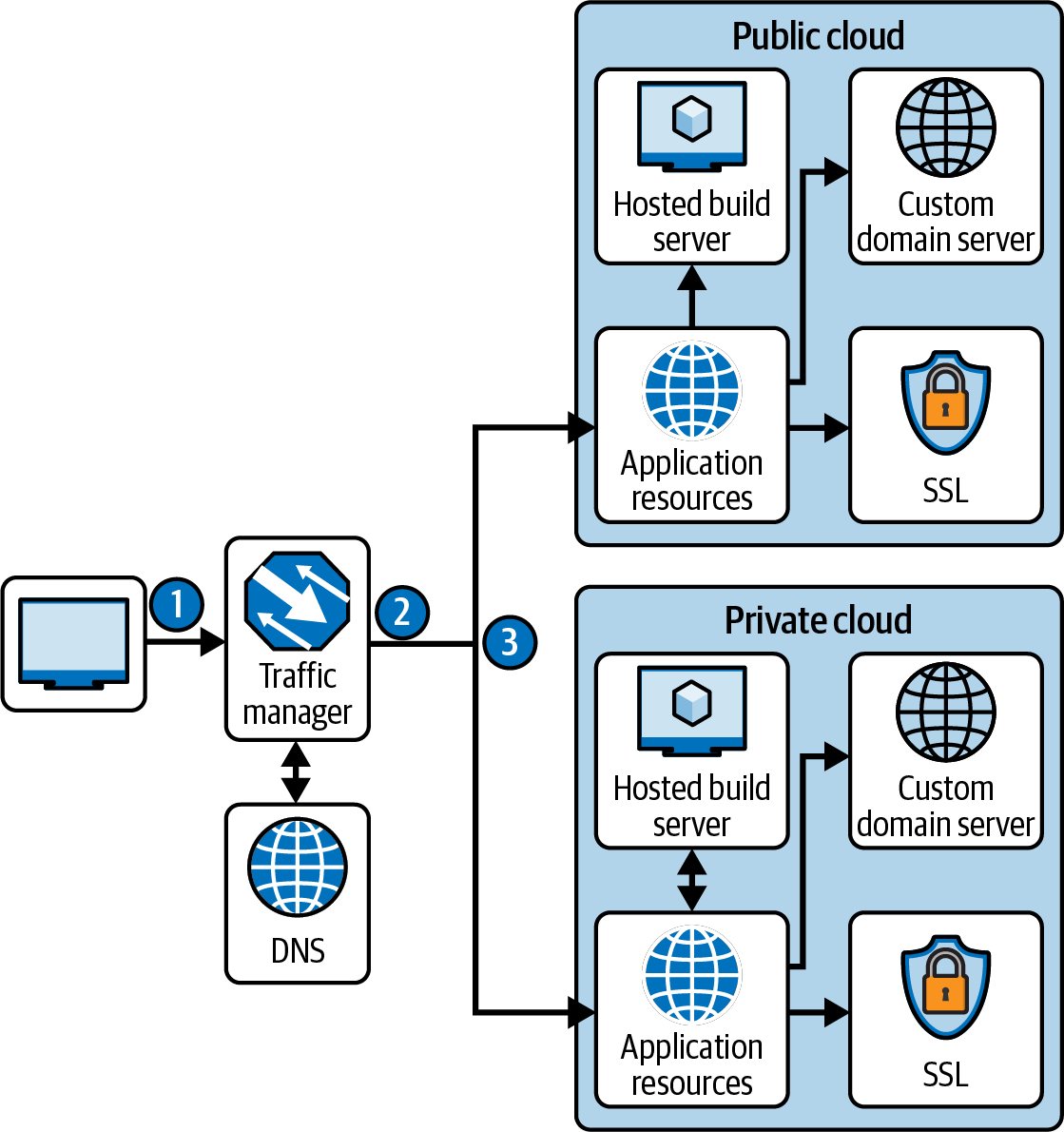
Figure 4-12. An example of Azure Traffic Manager being used for a web application to scale and load-balance traffic in a hybrid cloud environment
If you have several instances in different Azure regions and one of these instances fails during the health check, the traffic for your application is directed to the Azure region that is healthy. However, a performance problem can occur in the latency of the traffic to a region located far away.
Therefore, there are some performance considerations when using and managing Azure Traffic Manager. There are several tools you can use to measure your DNS latency and performance. Discussing the technical details of these traffic monitoring tools is beyond the scope of this book, but if you want to learn more, see Microsoft’s recommendations for measuring traffic manager performance.
Azure CDN
Azure Content Delivery Network (CDN) is a global CDN solution for delivering high-bandwidth content by caching content in different locations. You can choose Azure CDN for applications hosted in Azure or any other servers or locations.
Azure CDN enables you to cache static objects coming from your web applications, Azure Blob storage, or a web server that is publicly available. It uses the closest POP server, as shown in Figure 4-13, to accelerate dynamic content.
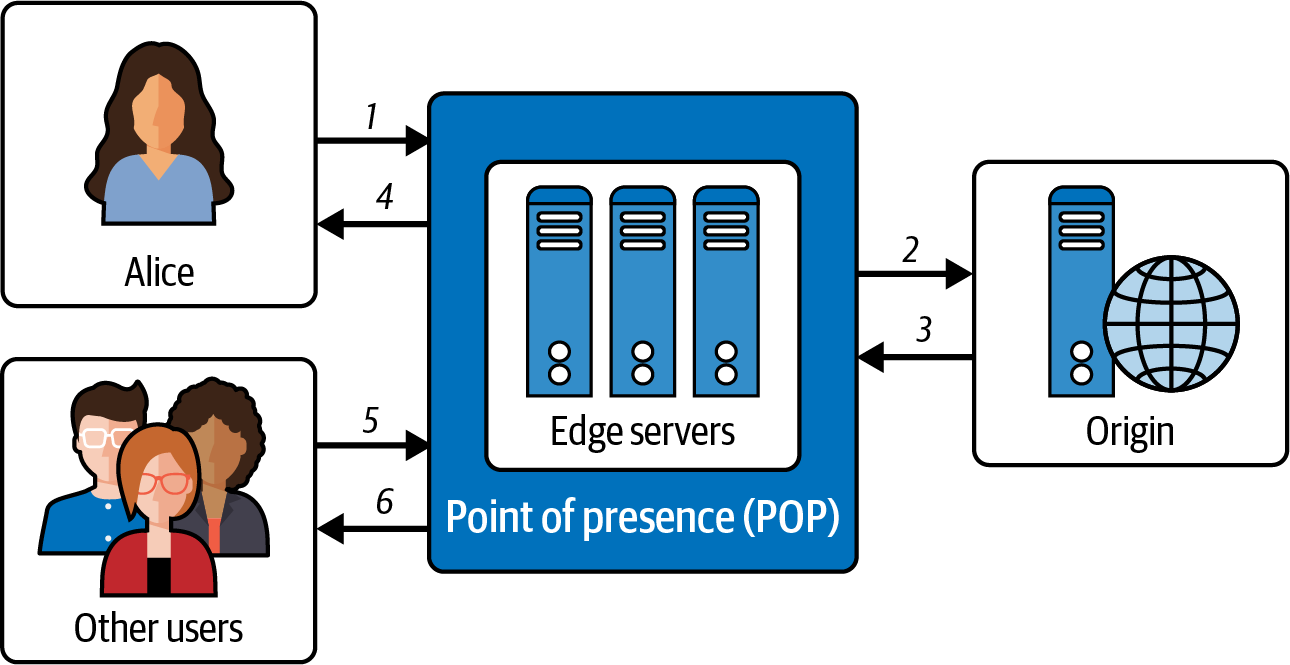
Figure 4-13. Point of presence server with Azure CDN
The following outlines the steps described in Figure 4-13:
-
A user accesses an asset from a web application using Azure CDN, which routes the request to the best possible POP server location.
-
If there a cache of the requested asset on the POP edge servers, it will return it directly to the user.
-
If the asset requested is not cached, it will request it from an origin. An origin can be your Azure Storage or Azure Web App.
-
The edge servers will cache the file or asset and return the response to the user with requested asset.
-
Other users from different locations can access the same file or asset.
-
Since the file or asset is already cached on POP edge servers, it arrives faster back to these users.
Additionally, here are some of the features of Azure CDN:
-
Better performance and user experience for end users globally
-
Gain the ability to scale to handle instantaneous high load and demand
-
Azure storage blobs can be used to cache content to make it publicly available
-
CDN caching of web content, images, scripts, and other web assets
-
Allows you to cache content based on specific query strings
-
Access the cached content from a custom domain through CDN HTTP endpoint mapping
Azure CDN has different tiers such as Azure CDN Standard from Microsoft, Azure CDN Standard from Akamai, and Azure CDN Standard and Premium from Verizon. Prior to setting up your Azure CDN account, you should understand the different tiers and the comparison of the different features they offer.
Azure Networking Services for Network Monitoring
This section describes networking services in Azure that help monitor your network resources such as Azure Network Watcher and Azure Monitor Network Insights. We will take a look at each of these services and how to use them to monitor your network.
Azure Network Watcher
Azure Network Watcher is a composed of different tools used for monitoring, diagnosing, logging, and metrics management for an Azure Virtual Network. This networking service is commonly used to track and monitor network health statuses of IaaS services such as VMs, application gateways, load balancers, virtual networks, etc.
Following are some of the benefits of using Azure Network Watcher:
-
Monitor communication between VMs and network endpoints at regular intervals with alerts and notifications
-
Vizualize the overview and relationships of Azure resources in a virtual network
-
Detect and troubleshoot any network traffic filtering problems between your VMs
-
Diagnose problems of network routing and outbound connections for VMs
-
VMs packet capturing that helps detect possible network anomalies
Azure Network Watcher is useful when you are troubleshooting issues related to detecting network traffic anomalies in Azure IaaS resources. For example, if you want to troubleshoot a problem with a VPN connection between two VMs, you can use Azure Network Watcher to monitor the traffic between them.
One limitation of using Azure Network Watcher is worth knowing. It will not work with web analytics and monitoring PaaS services because Network Watcher was not designed to be used with these two services.
Azure Monitor Network Insights
Azure Monitor Network Insights provides an overall view of health and metrics for all the network resources that you have deployed and hosted in Azure. This Network Insights service is part of Azure Monitor and allows you to track networking metrics easily without advanced configuration.
It is structured around these key components of monitoring:
-
Network health and metrics for the visualization of all your networking resources with the option to search, filter, and set up alerts and dependency views
-
Connectivity helps you visualize all the configured tests done via Connection Monitor
-
Traffic gives you a view of all flow logs for network security groups (NSGs) and also the traffic analytics for the selected set of subscriptions, grouped by location
-
Diagnostic Toolkit can be used in troubleshooting network issues such as IP flow verification, packet capture, etc.
If you are using Azure Monitor for monitoring and gathering metrics for your Azure resources, then Network Insights is good tool to use, especially when you house multiple networking resources in Azure.
Azure Space: Networking Beyond the Clouds
Azure Space is one of Microsoft’s most-advanced innovations. Microsoft wanted to create networking and connectivity beyond the clouds, to the space. It was created and serves as an ecosystem and platform for the space community.
As of this writing, there are three services created for Azure Space: Azure Orbital, Azure Modular Data Center, and Azure Orbital Emulator.
- Azure Orbital
-
Azure Orbital is a fully managed ground station as a service (GSaaS). This service is currently in a preview version. It helps users to communicate, downlink, schedule service, control their satellites, and scale operations from Azure. With the use of Azure Orbital, integrated data processing is easily managed on the Azure platform. Data being processed is transferred securely through the user’s virtual network, which can be stored on Azure Storage or any Azure service. The main use of Azure Orbital is for global communications and earth observation. Figure 4-14 illustrates how Azure Orbital is connected to Azure data centers using Azure WAN and how it connects to satellites in space using an orbital downlink.
- Azure Orbital Emulator
-
Azure Orbital Emulator enables satellite developers to use AI algorithms to evaluate satellites before launching, and it can simulate complex satellite networking. The Orbital Emulator assists in getting perspective on how an application functions when it is in orbit. This tool enables satellite developers to test their applications in the cloud (Azure) first before they deploy them to space.
- Azure Modular Datacenter
-
Azure Modular Datacenter (MDC) was designed and created to help users who need cloud computing solutions in hybrid, challenging environments and remote locations. As an MDC user, you have the capability to deploy your own self-contained transportable data center unit near the location you need it to be. In simple terms, Azure provides a portable data center unit (MDC unit) that is fully equipped with full network connectivity and secure network connectivity using satellite communications.
If your organization is interested in learning more about Azure Orbital and cloud services for space, check out their Azure Space Partner Community program.
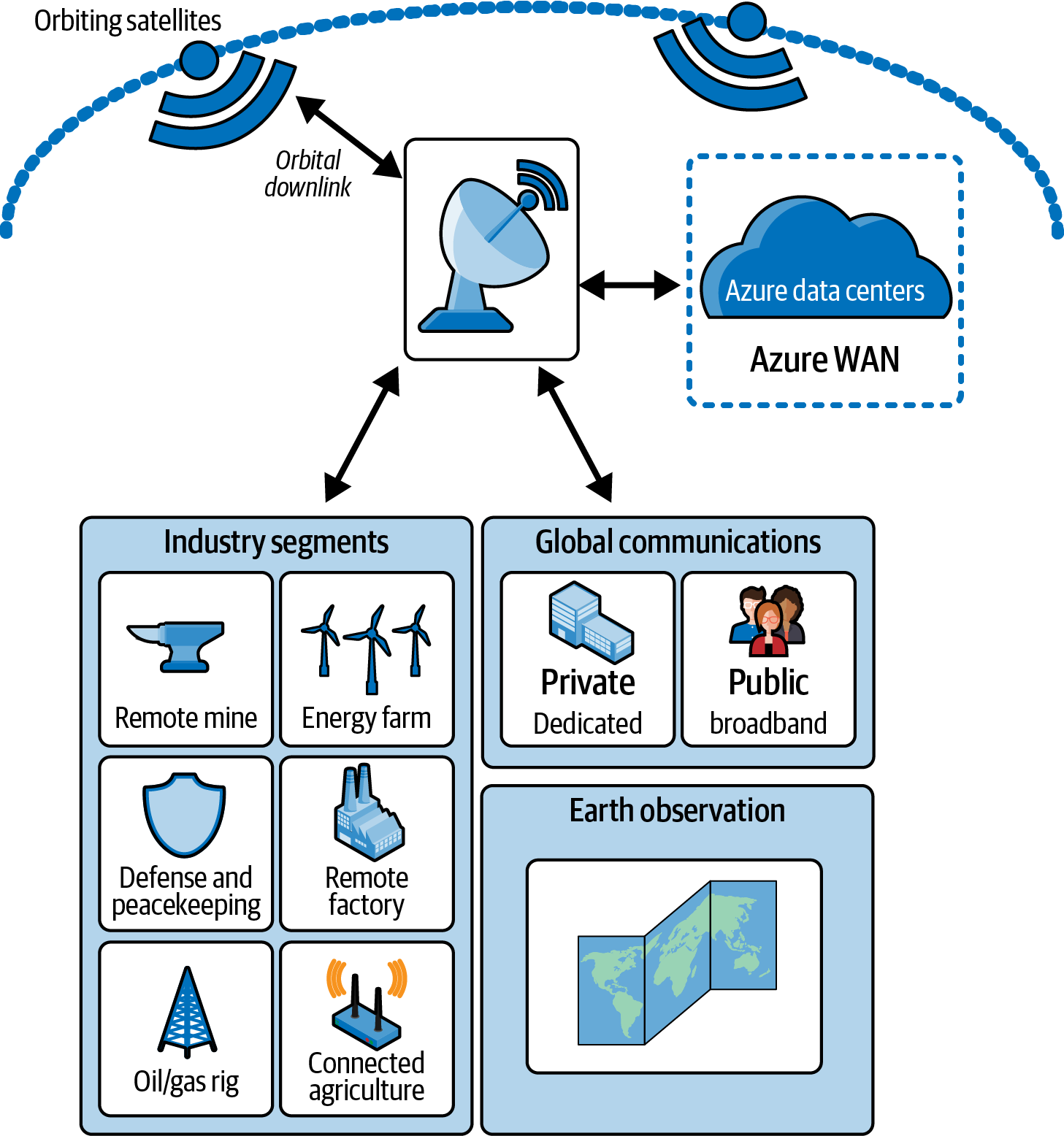
Figure 4-14. Global satellites and networks connect using Azure Orbital (adapted from an image by Microsoft documentation)
Learn By Doing (Try It!)
In addition to the hands-on lab repository for the topics in the this chapter, the following quick-start tutorials are recommended as they are updated based on Microsoft’s technical updates for the service:
Summary
In this chapter, we explored basic concepts, descriptions, features, and limitations of Azure’s most common networking services and tools. We learned that networking services are categorized by their different purposes, such as connectivity, application delivery, security, and monitoring. Information on these networking services, grouped by category, provides an overview and ideas on which networking service to use along with compute resources in your cloud application development.
Azure has several load-balancing solutions, including Front Door, Traffic Manager, Application Gateway, which can be used individually or in combination. We also learned that Azure networking goes beyond the clouds of cloud computing to outer space through Azure Space services like Azure Orbital, Azure Orbital Emulator, and Azure Modular Datacenter that are offered as ground station as a service (GSaaS). GSaaS allows space explorers and researchers to communicate globally through space stations for research and innovation.
In the next chapter, you will learn more about the different storage and database solutions in Azure.
Check Your Knowledge
-
What is the basic block of a private network in Azure that enables your Azure resources to communicate with each other?
-
How can you protect and secure your applications in Azure using the networking resources available? (List a few examples.)
-
You need to securely connect your on-premises network to Azure in a private connection; which Azure networking services would you use?
-
What networking service would you use if you wanted to filter inbound and outbound traffic of Azure resources and secure your VNets?
-
What Azure networking service would you use if you want features like dynamic site acceleration, file compression, geo-filtering, and set caching rules for web content?
For the answers to these questions, see the Appendix.
Recommended Learning Resources
“Architect Network Infrastructure in Azure.” Microsoft Learn, https://oreil.ly/I2nQ-.
“Azure Front Door and CDN Documentation.” Microsoft Learn, https://oreil.ly/lJGne.
“Azure Networking Architecture Documentation.” Microsoft Learn, June 13, 2023, https://oreil.ly/bnmIM.
“Azure Networking Fundamentals Documentation.” Microsoft Learn, https://oreil.ly/QOgMe.
“Azure Orbital Documentation.” Microsoft Learn, https://oreil.ly/payyz.
“Enable Remote Work by Using Azure Networking Services.” Microsoft Learn, April 9, 2023, https://oreil.ly/uNJzr.
“Get Up and Running with Kubernetes.” Microsoft Azure, https://oreil.ly/s3Vzj.
Marczac, Adam. “AZ-900 Episode 10 | Networking Services | Virtual Network, VPN Gateway, CDN, Load Balancer, App GW.” Adam Marczak – Azure for Everyone, YouTube video, August 18, 2020, https://oreil.ly/eJmgP.
“Microsoft Azure Fundamentals: Describe Azure Architecture and Services.” Microsoft Learn, https://oreil.ly/XY5vc.
Savill, John. “Azure Master Class V2 – Module 6 – Networking.” John Savill’s Technical Training, YouTube video, January 17, 2023, https://oreil.ly/q4-Fx.
Smith, Derek. “Zero to Hero with Azure Virtual WAN by Derek Smith.” MC2MC, YouTube Video, December 20, 2021, https://oreil.ly/Xn9Gv.
Smith, Derek. “Azure Network Engineer Associate (AZ-700) Cert Prep: Secure Network Connectivity to Azure Resources.” LinkedIn Learning, September 25, 2023, https://oreil.ly/DC82Y.
Valiramani, Avinash. Microsoft Azure Networking: The Definitive Guide. Microsoft Press, 2022.
“Why Use Azure Orbital Ground Station?” Microsoft Learn, August 15, 2023, https://oreil.ly/qYhet.
Get Learning Microsoft Azure now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

