By default, Nmap establishes a TCP three-way handshake on any open TCP ports found. After the handshake has been established, the messages are exchanged. The following snippet displays the handshake process, where Host A wants to communicate with Host B:
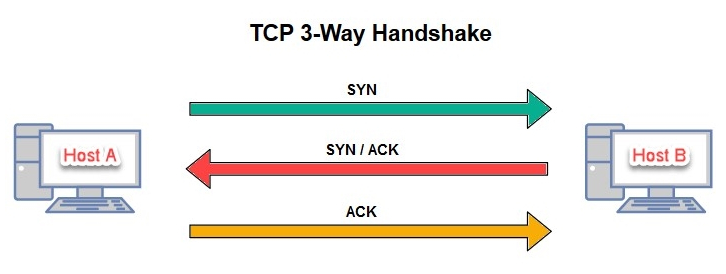
During a penetration test, we need to remain as stealthy as possible on the network. This creates the effect of an actual hacker attempting to compromise the system/network without being caught by the organization's security controls and systems. By establishing a TCP three-way handshake with our target devices, we are making ourselves ...

