Part V. Security Patterns
Security is a broad topic that has implications for all stages of the software development lifecycle, from development practices, to image scanning at build time, to cluster hardening through admission controllers at deployment time, to threat detection at runtime. Security also touches all the layers of the software stack, from cloud infrastructure security, to cluster security, to container security, to code security, also known as the 4C’s of cloud native security. In this section, we focus on the intersection of an application with Kubernetes from the security point of view, as demonstrated in Figure V-1.
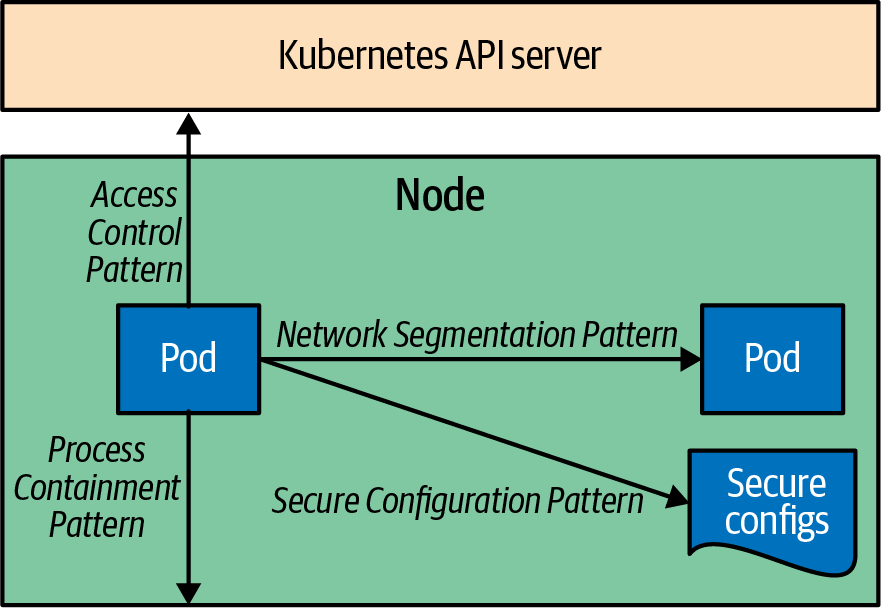
Figure V-1. Security patterns
We start by describing the Process Containment pattern to contain and limit the actions an application is allowed to perform on the node it is running on. Then we explore the techniques to limit what other Pods a Pod can talk to by doing Network Segmentation. In the Secure Configuration pattern, we discuss how an application within a Pod can access and use configurations in a secure way. And finally, we describe the Access Control pattern—how an application can authenticate and talk to the Kubernetes API server and interact with it in more advanced scenarios. These give you an overview of the main security dimensions of an application running on Kubernetes, and we discuss the resulting patterns in the following chapters: ...
Get Kubernetes Patterns, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

