Time for action – beating MAC filters
Let's follow the instructions to get started:
- Let's first configure our access point to use MAC filtering and then add the client MAC address of the victim laptop. The settings pages on my router looks as follows:
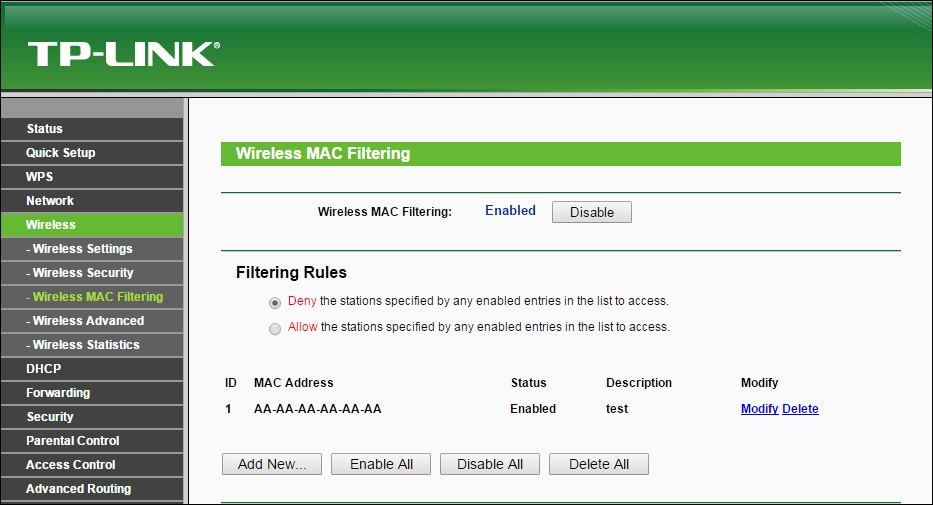
- Once MAC filtering is enabled, only the allowed MAC address will be able to successfully authenticate with the access point. If we try to connect to the access point from a machine with a non-whitelisted MAC address, the connection will fail.
- Behind the scenes, the access point is sending Authentication failure messages to the client. The packet trace resembles the following:
- In order to beat MAC filters, ...
Get Kali Linux Wireless Penetration Testing : Beginner's Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

