The cSploit app allows for easy information-gathering, session-hijacking, and Denial-of-Service (DoS) and Man-in-the-Middle (MitM) attacks, with the tap of a button. Upon startup, cSploit first prompts the user to select a target network. The user is then presented with several modules, as seen in the following screenshot:
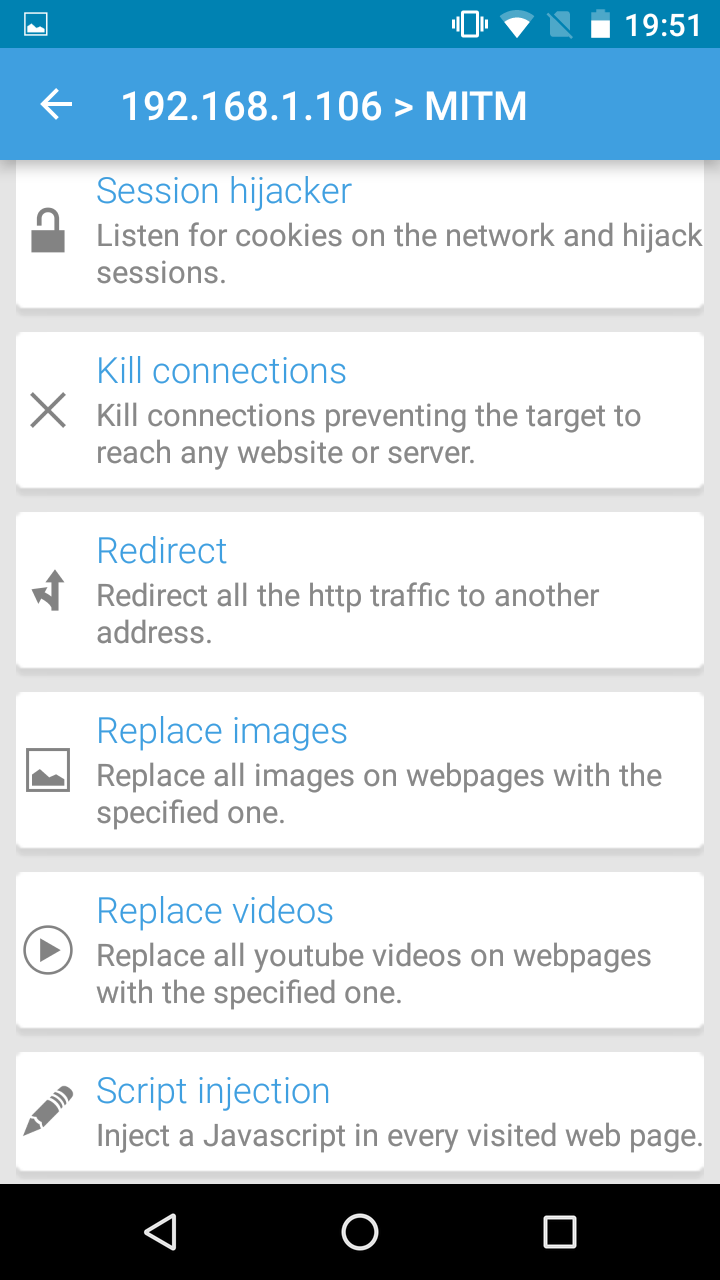
This tool is rather impressive considering that all modules can be run from a mobile device and can be hidden on the penetration tester's person or easily concealed while the attacks are carried out for as long as the battery lasts.

