1.1 Secure Communications
In the basic communication scenario, depicted in Figure 1.1, there are two parties, we’ll call them Alice and Bob, who want to communicate with each other. A third party, Eve, is a potential eavesdropper.
Figure 1.1 The Basic Communication Scenario for Cryptography.
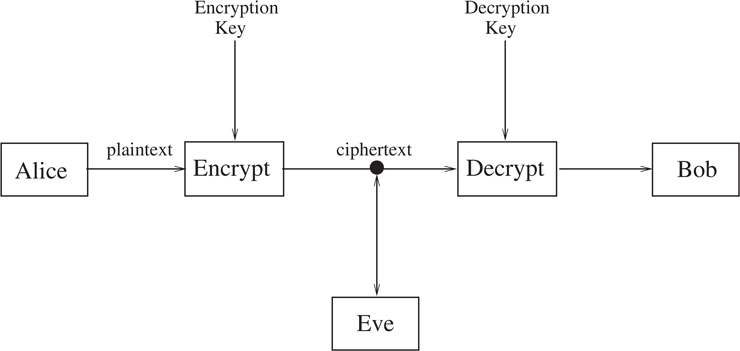
When Alice wants to send a message, called the plaintext, to Bob, she encrypts it using a method prearranged with Bob. Usually, the encryption method is assumed to be known to Eve; what keeps the message secret is a key. When Bob receives the encrypted message, called the ciphertext, he changes it back to the plaintext using ...
Get Introduction to Cryptography with Coding Theory, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

