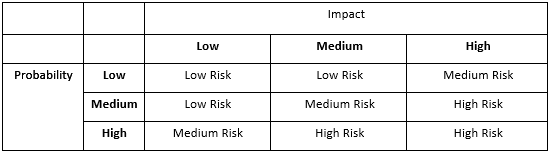
Now that we have developed our lists of threats and vulnerabilities, and developed our rules on how we measure likelihood and impact, we are able to analyze risk. We will use the following risk assessment matrix utilizing the likelihood and impact rules developed previously:
We will take the threat and vulnerability pairs table that we developed previously and include the likelihood, impact, and risk ratings from the preceding table:
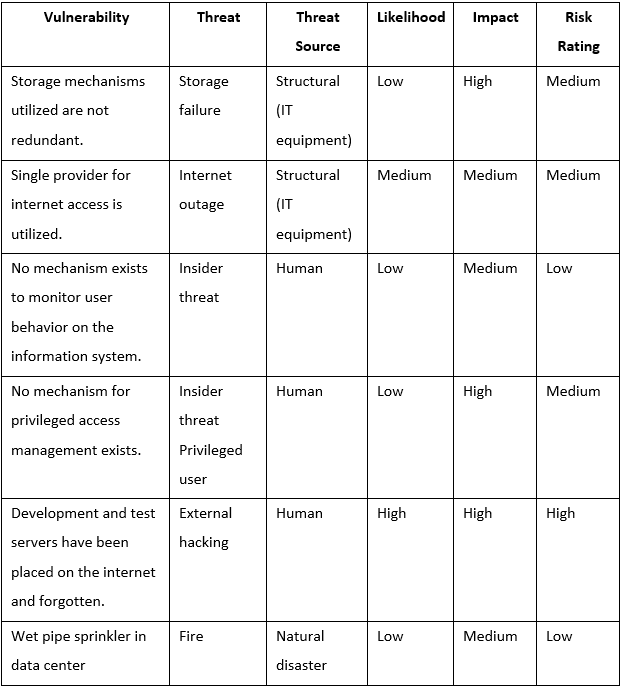
Now that we have completed the risk assessment table, you can clearly see that ...

