Today, many applications provide APIs to the external developers to interact with the application. Depending on the type of services that the application offers, the API can perform simple URL-based data manipulations or even an advanced service oriented architecture model:
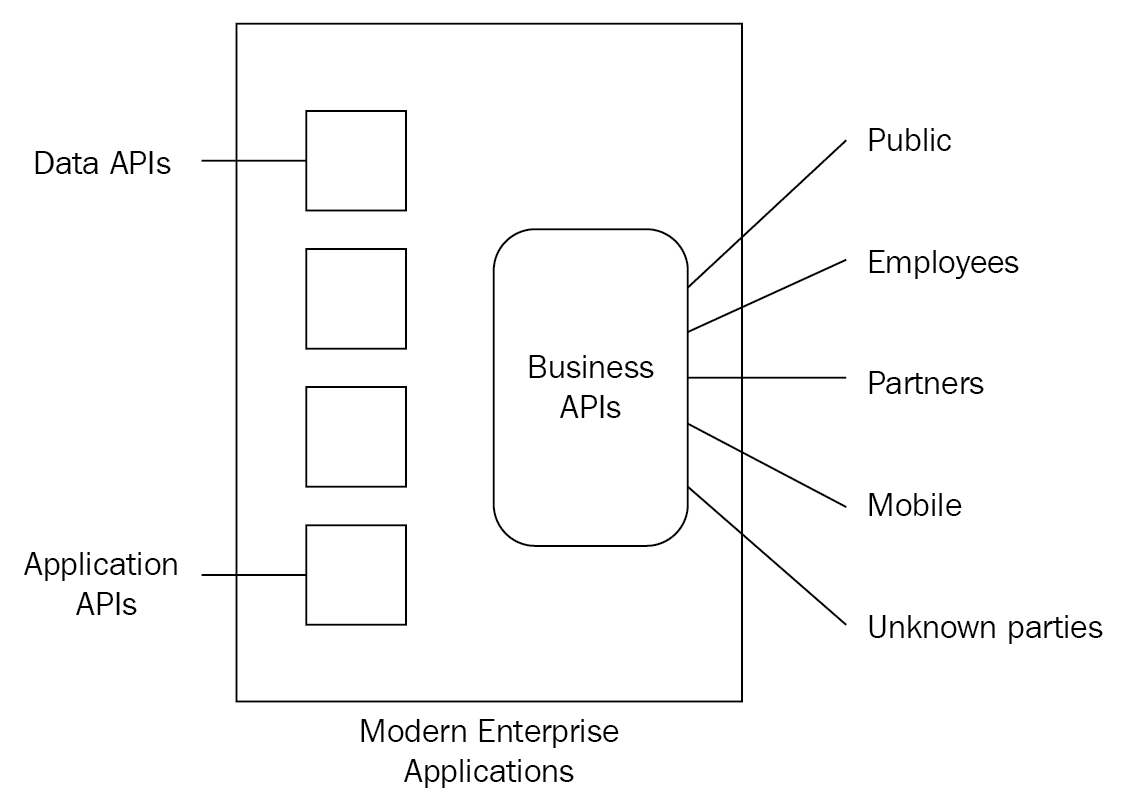
These APIs may be invoked to fetch, update, and delete data on the server or database, depending on the type of the API implementation. These APIs can simply be invoked by sending an HTTP GET, PUT, POST, or DELETE request along with the JSON representation of the resources. If these API endpoints deal with sensitive data, there is a risk of ...

