Once we've added hosts to Metasploit, the next step is scanning. Metasploit has an inbuilt wrapper for Nmap that gives us the same functionality of Nmap within the Metasploit console. The benefit of this wrapper is that it saves the output in the database by default.
To run a scan against a host, we can use the db_nmap <IP> command. Here, we have used the --open flag to view only open ports. -v is used for verbose, -Pn is used to perform a no-ping scan, -sV is used to perform a service scan, and -sC is used to run script scans against discovered ports:
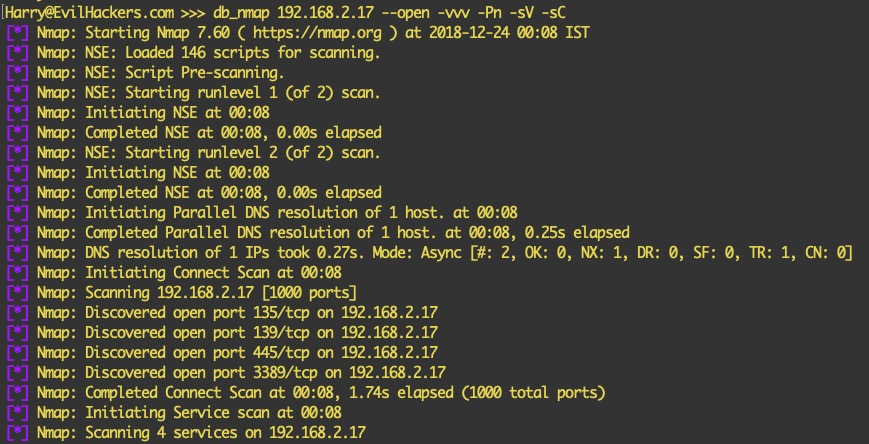
The following screenshot shows the output of the scan that was run ...

