All of the targets that are stored in the Metasploit DB can be passed on to Nessus using the nessus_db_scan <policy ID> <scan name> <scan description> command. In our case, we have the target 192.168.2.1 IP stored in our Metasploit DB; upon executing this command, Nessus will start the scan (NOT only creating the task, but launching it as well) on the target IP, which is stored in the Metasploit DB:
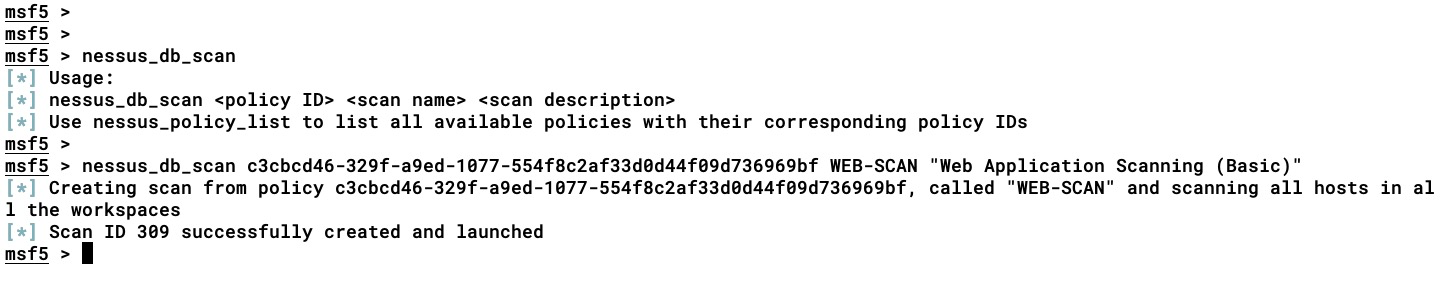
Follow these steps:
- Let's confirm the preceding execution from the Nessus web interface:
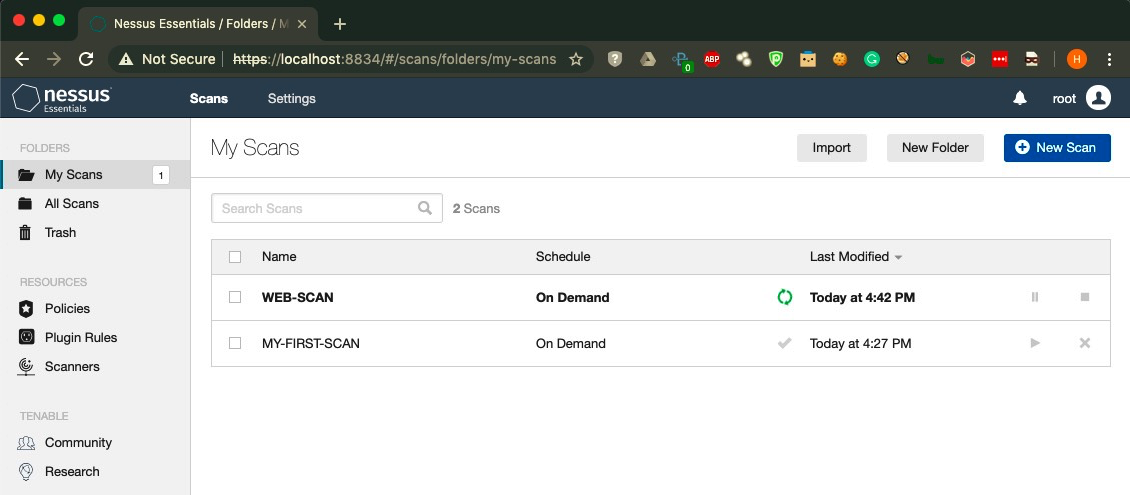
- As we can see ...

