Now that we have used Wfuzz and ffuf to fuzz the URI path, let's try the same in Burp Suite Intruder. The concept here is the same. Let's place a payload marker (as shown in the following screenshot) for the fuzzer to send data to the vector:
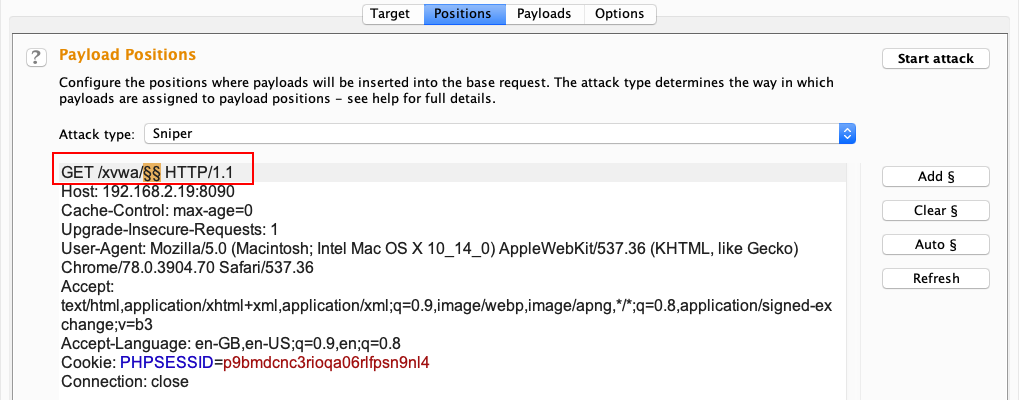
Let's set Payload type to Simple list and import a wordlist using the Load … button:
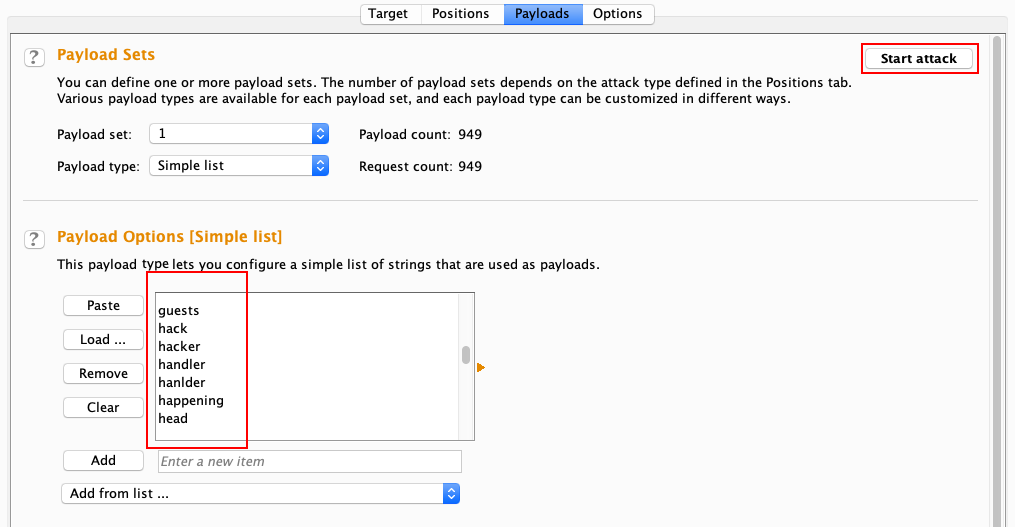
Click on the Start attack button (as shown in the preceding screenshot) and Intruder will try to fuzz the URI path with the custom wordlist given to it. The result ...

