The Linux kernel has a very powerful built-in tracing mechanism (well, it's one of them) – Ftrace. Using ftrace, you can verify that it's indeed the LSM code that, while honoring its security policy, caused the userspace-issued system call to return failure. I ran a trace (with ftrace):
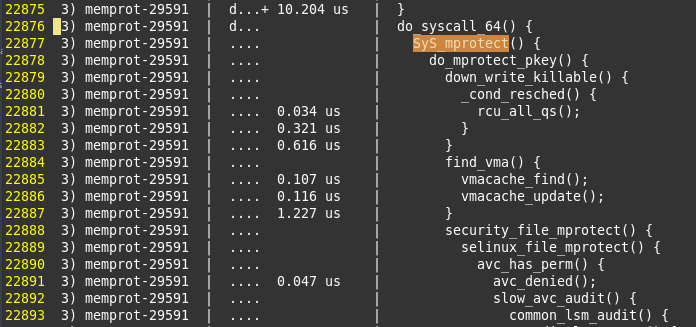
The SyS_mprotect function is what the mprotect(2) system call becomes within the kernel; security_file_mprotect is the LSM hook function that leads to the the actual SELinux function: selinux_file_mprotect; apparently, it fails the access.
Interestingly, Ubuntu 18.04 LTS also uses an LSM – AppArmor. However, it seems that it has ...

