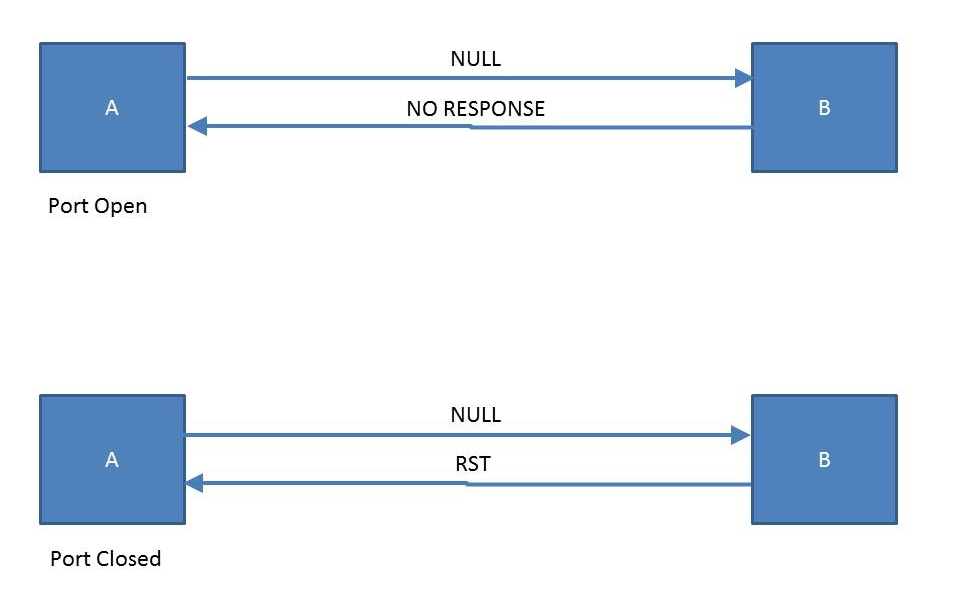
In a null scan, the attacker sends a packet to the target without any flags set within it. Once again, the target will be confused and will not respond. This will indicate the port is open on the target. However, if the target responds with an RST packet, this means the port is closed on the device. The following diagram illustrates this process:
To execute a NULL scan, select TCP Null from the list in the nmap window in the NetHunter app and enter the target IP address: