Execute the following steps to perform data exfiltration using Burp Suite:
- First, configure Burp Suite to intercept the request made by the application, and stop when the request which sends the $id value, using the Intercept is on option in the Proxy tab, as shown in the following screenshot:
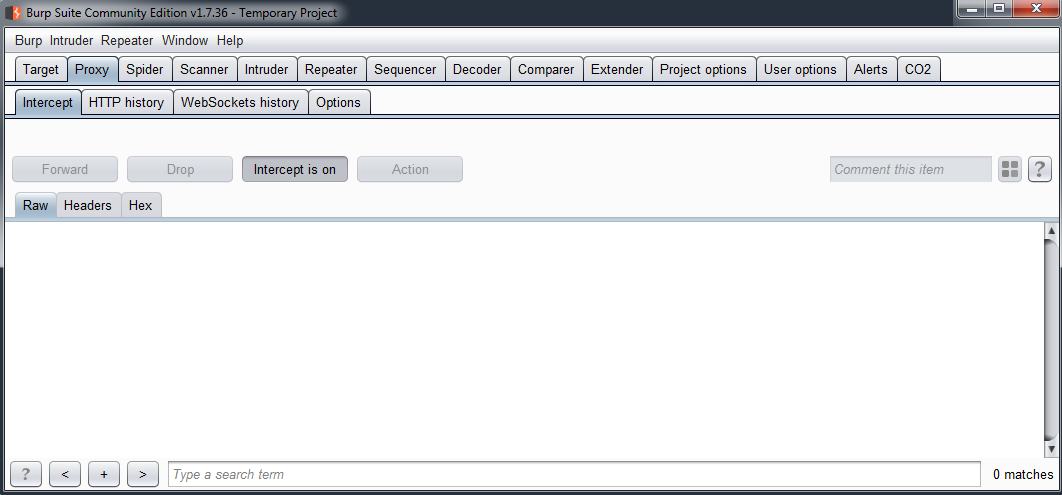
- Once the request is stopped, right-click on it, and select the Send to intruder option, as follows:

By default, Burp Suite creates wildcards for each variable detected in the request and creates values in the ...

