Appendix A. A Pod-Level Attack
This appendix is a hands-on exploration of attacks on the pod level, as we discussed in Chapter 2.

Dread cyberpirate Captain Hashjack can now execute code inside a pod remotely and they will start to explore its configuration to see what else can be accessed.
Like all good pirates, Captain Hashjack has a treasure map, but this is no ordinary map with a clearly defined destination. Instead, this map describes only the journey, with no guarantee of reaching a conclusion. It’s a cluster attack map, as shown in Figure A-1, and it is used to guide us through the rest of the appendix. And now, from inside the pod, it’s time to explore.
Tip
Securing any system is difficult. The best way to find vulnerabilities and misconfiguration is to methodically observe your environment, build up a library of your own attacks and patterns, and not give up!
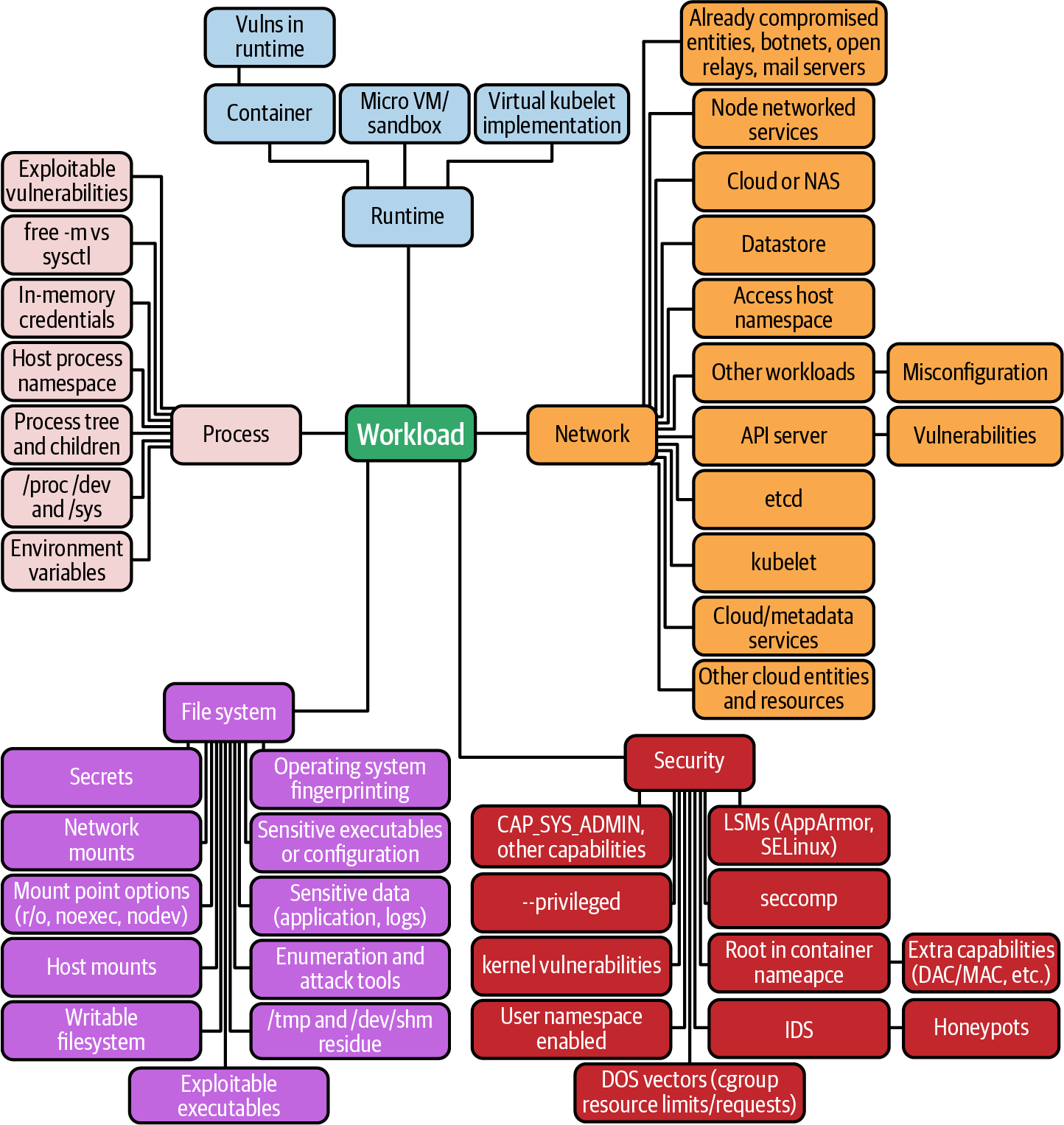
Figure A-1. Pod attack map
Filesystem
Upon entering a new environment, a little basic checking may lead to useful discoveries.
The first thing Hashjack does is check to see what kind of container they’re in. Checking /proc/self/cgroup often
gives a clue, and here they can see they’re in Kubernetes from the clue /kubepods/besteffort/pod8a6fa26b-...:
adversary@hashjack-5ddf66bb7b-9sssx:/$ cat /proc/self/cgroup ...Get Hacking Kubernetes now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

