11 Implementation of the ICS Cybersecurity Management Approach
11.1. Introduction
11.1.1. Organization of the process
Securing a control command system has many facets. Several possibilities exist to organize the process. A fairly natural approach is to consider the different phases of the risk evolution, or more precisely the course of events leading to damage.
First of all, it is necessary to put in place controls to limit the possibility of occurrence of unwanted events. In the case that, despite these controls, attacks occur, it is important to be able to detect them and provide appropriate mechanisms. If an attack is detected, to limit damage, an appropriate response must be planned and implemented. Finally, after this crisis phase, if damage has occurred, we must be able to restore the system and learn lessons to improve system security. This approach is the one proposed in the well-known NIST Cyber Security Framework (Figure 11.1), which focuses on the different phases of risk management:
- – identification;
- – protection;
- – detection, during operation;
- – the response to attack;
- – recovery.
For each phase, a number of areas have been identified. They include a list of security measures to be implemented.
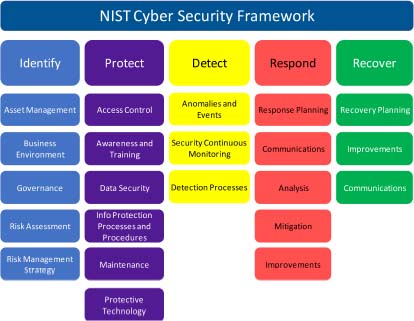
Figure 11.1. Structure of the NIST framework. For a color version of this figure, see www.iste.co.uk/flaus/cybersecurity.zip
For the protection phase, an approach ...
Get Cybersecurity of Industrial Systems now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

