Chapter 6: Monitoring and Auditing Your Cloud Environments
In chapters 2–5, we covered the fundamental building blocks of cloud services (from compute, storage, and networking services to identity and access management services).
Following previous chapters where we reviewed various network security-related services, the following diagram demonstrates traffic flow from external customers, through security controls (Distributed Denial of Service (DDoS) protection, Web Application Firewall (WAF), and access control lists such as AWS NACL and security groups), till the customer reaches a resource:
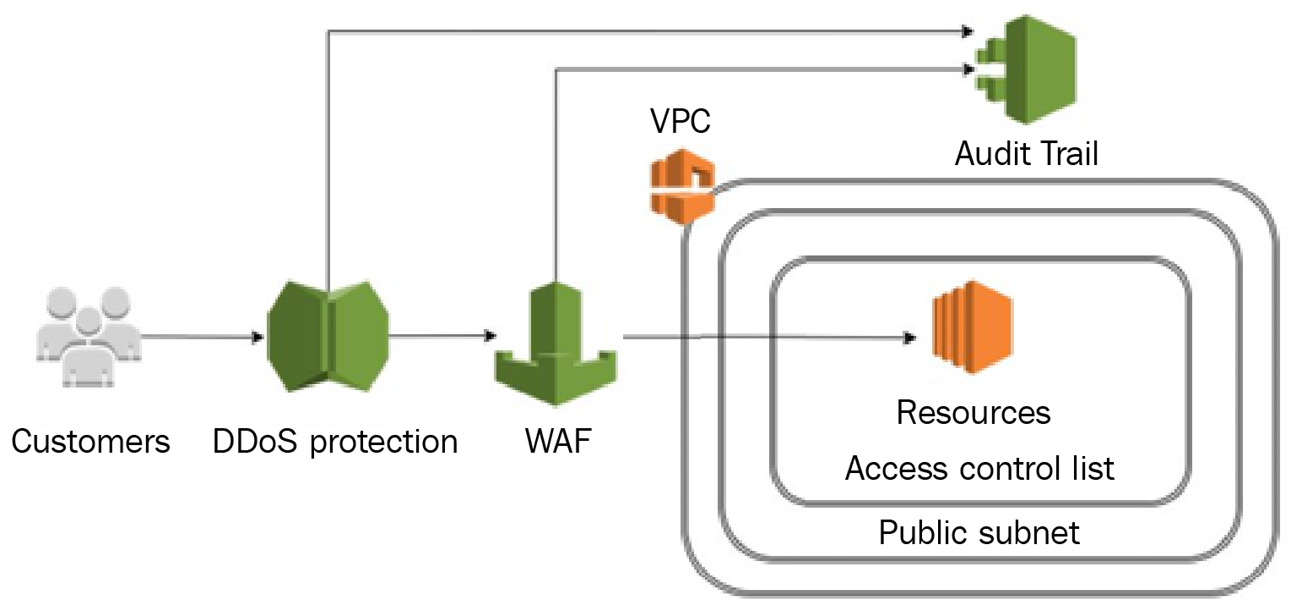
Figure 6.1 – Customer traffic flow
Important ...
Get Cloud Security Handbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

