Chapter 1. Exam Details and Resources
This introductory chapter addresses the most pressing questions candidates ask when preparing for the Certified Kubernetes Security Specialist (CKS) exam. We will discuss the target audience for the certification, the curriculum, and the exam environment, as well as tips and tricks and additional learning resources. If you’re already familiar with the certification program, you can directly jump to any of the chapters covering the technical concepts.
Kubernetes Certification Learning Path
The CNCF offers four different Kubernetes certifications. Figure 1-1 categorizes each of them by target audience. You will find that the CKS is the most advanced certification you can acquire. It is the only one with a prerequisite of passing another certification first; all others are standalone programs.
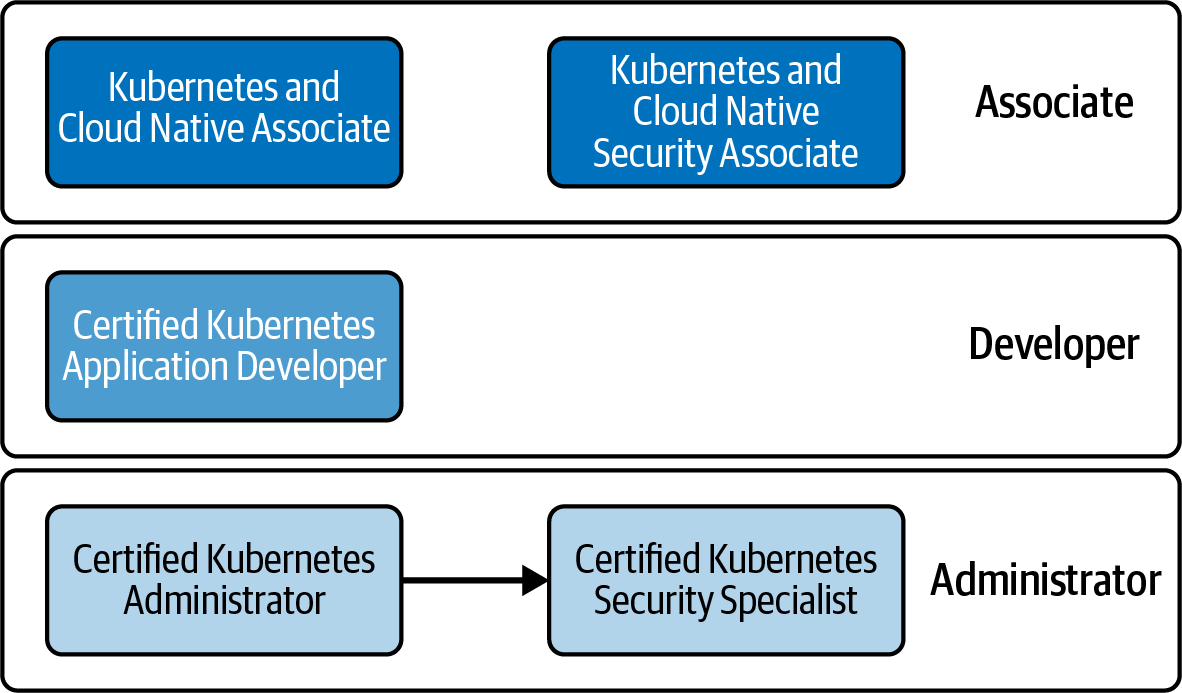
Figure 1-1. Kubernetes certifications learning path
Let’s have a very brief look at the details for each certification to see if the CKS is the right fit for you.
Kubernetes and Cloud Native Associate (KCNA)
KCNA is an entry-level certification program for anyone interested in cloud-native application development, runtime environments, and tooling. While the exam does cover Kubernetes, it does not expect you to actually solve problems in a practical manner. This exam is suitable for candidates interested in the topic with a broad exposure to the ecosystem.
Certified Kubernetes Application Developer (CKAD)
The CKAD exam focuses on verifying your ability to build, configure, and deploy a microservices-based application to Kubernetes. You are not expected to actually implement an application; however, the exam is suitable for developers familiar with topics like application architecture, runtimes, and programming languages.
Certified Kubernetes Administrator (CKA)
The target audience for the CKA exam are DevOps practitioners, system administrators, and site reliability engineers. This exam tests your ability to perform in the role of a Kubernetes administrator, which includes tasks like cluster, network, storage, and beginner-level security management, with a big emphasis on troubleshooting scenarios.
Certified Kubernetes Security Specialist (CKS)
The CKS exam expands on the topics verified by the CKA exam. Passing the CKA is a prerequisite before you can even sign up for the CKS exam. For this certification, you are expected to have a deeper knowledge of Kubernetes security aspects. The curriculum covers topics like applying best practices for building containerized applications and ensuring a secure Kubernetes runtime environment.
Exam Objectives
Vulnerabilities in software and IT infrastructure, if exploited, can pose a major threat to organizations. The Cloud Native Computing Foundation (CNCF) developed the Certified Kubernetes Security Specialist (CKS) certification to verify a Kubernetes administrator’s proficiency to protect a Kubernetes cluster and the cloud native software operated in it. As part of the CKS exam, you are expected to understand Kubernetes core security features, as well as third-party tools and established practices for securing applications and infrastructure.
Kubernetes version used during the exam
At the time of writing, the exam is based on Kubernetes 1.26. All content in this book will follow the features, APIs, and command-line support for that specific version. It’s certainly possible that future versions will break backward compatibility. While preparing for the certification, review the Kubernetes release notes and practice with the Kubernetes version used during the exam to avoid unpleasant surprises.
In this book, I am going to explain each of the security threats by providing a specific use case. We’ll start by talking about a scenario that allows an attacker to gain access to a cluster, inject malicious code, or use a vulnerability to hack into the system. Then, we’ll touch on the concepts, practices, and/or tools that will prevent that situation. With this approach, you’ll be able to evaluate the severity of a security risk and the need for implementing security measures.
Curriculum
The following overview lists the high-level sections, also called domains, of the CKS exam and their scoring weights:
-
10%: Cluster Setup
-
15%: Cluster Hardening
-
15%: System Hardening
-
20%: Minimize Microservice Vulnerabilities
-
20%: Supply Chain Security
-
20%: Monitoring, Logging, and Runtime Security
How the book works
The outline of the book follows the CKS curriculum to a T. While there might be a more natural, didactical organization structure to learn Kubernetes in general, the curriculum outline will help test takers prepare for the exam by focusing on specific topics. As a result, you will find yourself cross-referencing other chapters of the book depending on your existing knowledge level.
Let’s break down each domain in detail in the next sections.
Cluster Setup
This section covers Kubernetes concepts that have already been covered by the CKA exam; however, they assume that you already understand the basics and expect you to be able to go deeper. Here, you will be tested on network policies and their effects on disallowing and granting network communication between Pods within the same namespace and across multiple namespaces. The main focus will be on restricting communication to minimize the attack surface. Furthermore, the domain “cluster setup” will verify your knowledge of setting up an Ingress object with Transport Layer Security (TLS) termination.
A big emphasis lies on identifying and fixing security vulnerabilities by inspecting the cluster setup. External tools like kube-bench can help with automating the process. As a result of executing the tool against your cluster, you will receive an actionable list of vulnerabilities. Changing the configuration settings of your cluster according to the recommendations can help with significantly reducing the security risk.
Last, locking down cluster node endpoints, ports, and graphical user interfaces (GUIs) can help with making it harder for attackers to gain control of the cluster. You need to be aware of the default cluster settings so that you can limit access to them as much as possible. Kubernetes binaries and executables like kubectl, kubeadm, and the kubelet need to be checked against their checksum to ensure they haven’t been tampered with by a third party. You need to understand how to retrieve the checksum file for binaries and how to use it verify the validity of the executable.
Cluster Hardening
Most organizations start out with a cluster that allows developers and administrators alike to manage the Kubernetes installation, configuration, and management of any objects. While this is a convenient approach for teams getting comfortable with Kubernetes, it is not a safe and sound situation, as it poses the potential of opening the floodgates for attackers. Once access has been gained to the cluster, any malicious operation can be performed.
Role-based access control (RBAC) maps permissions to users or processes. The exam requires deep knowledge of the API resources involved. The domain “cluster hardening” also focuses the topic of keeping the cluster version up-to-date to ensure the latest bug fixes are picked up. Kubernetes exposes the API server via endpoints. You should be aware of strategies for minimizing its exposure to the outside world.
System Hardening
This domain is all about understanding how to minimize access to the host system and external network to reduce the attack surface. This is where OS-level tools like AppArmor and seccomp come into play. You will need to demonstrate their use to fulfill the requirement. The domain also touches on the use of AWS IAM roles for clusters running in Amazon’s cloud environment specifically.
Minimize Microservice Vulnerabilities
Security contexts define privilege and access control for containers. Platform and security teams can govern and enforce desired security measures on the organizational level. The exam requires you to understand Pod security policies and the OPA Gatekeeper for that purpose. Moreover, you’ll be asked to demonstrate defining Secrets of different types and consuming them from Pods to inject sensitive runtime information.
Sometimes, you may want to experiment with container images from an unverified source or a potentially unsafe origin. Container runtime sandboxes like gVisor and Kata Containers can be configured in Kubernetes to execute a container image with very restricted permissions. Configuring and using such a container runtime sandbox is part of this domain. Further, you need to be aware of the benefits of mTLS Pod-to-Pod encryption and how to configure it.
Supply Chain Security
Container security starts with the base image. You need to be aware of the best practices for building container images that minimize the risk of introducing security vulnerabilities from the get-go. Optimally, you will only allow pulling trusted container images from an organization-internal container registry that has already scanned the image for vulnerabilities before it can be used. Allowing only those registries is paramount and will be one of the topics important to this domain. Tools like Trivy can help with the task of scanning images for vulnerabilities and are listed as a requirement to pass the exam.
Monitoring, Logging, and Runtime Security
One of the focus points of this domain is behavior analytics, the process of observing abnormal and malicious events. Falco is the primary tool to get familiar with in this section. A container should not be mutable after it has been started to avoid opening additional backdoors for attackers. You will need to be aware of best practices and demonstrate the ability to apply them in the configuration of a container.
Audit logging can be helpful for a real-time view on cluster events or for debugging purposes. Configuring audit logging for a Kubernetes cluster is part of the exam.
Involved Kubernetes Primitives
Some of the exam objectives can be covered by understanding the relevant core Kubernetes primitives. It is to be expected that the exam combines multiple concepts in a single problem. Refer to Figure 1-2 as a rough guide to the applicable Kubernetes resources and their relationships.
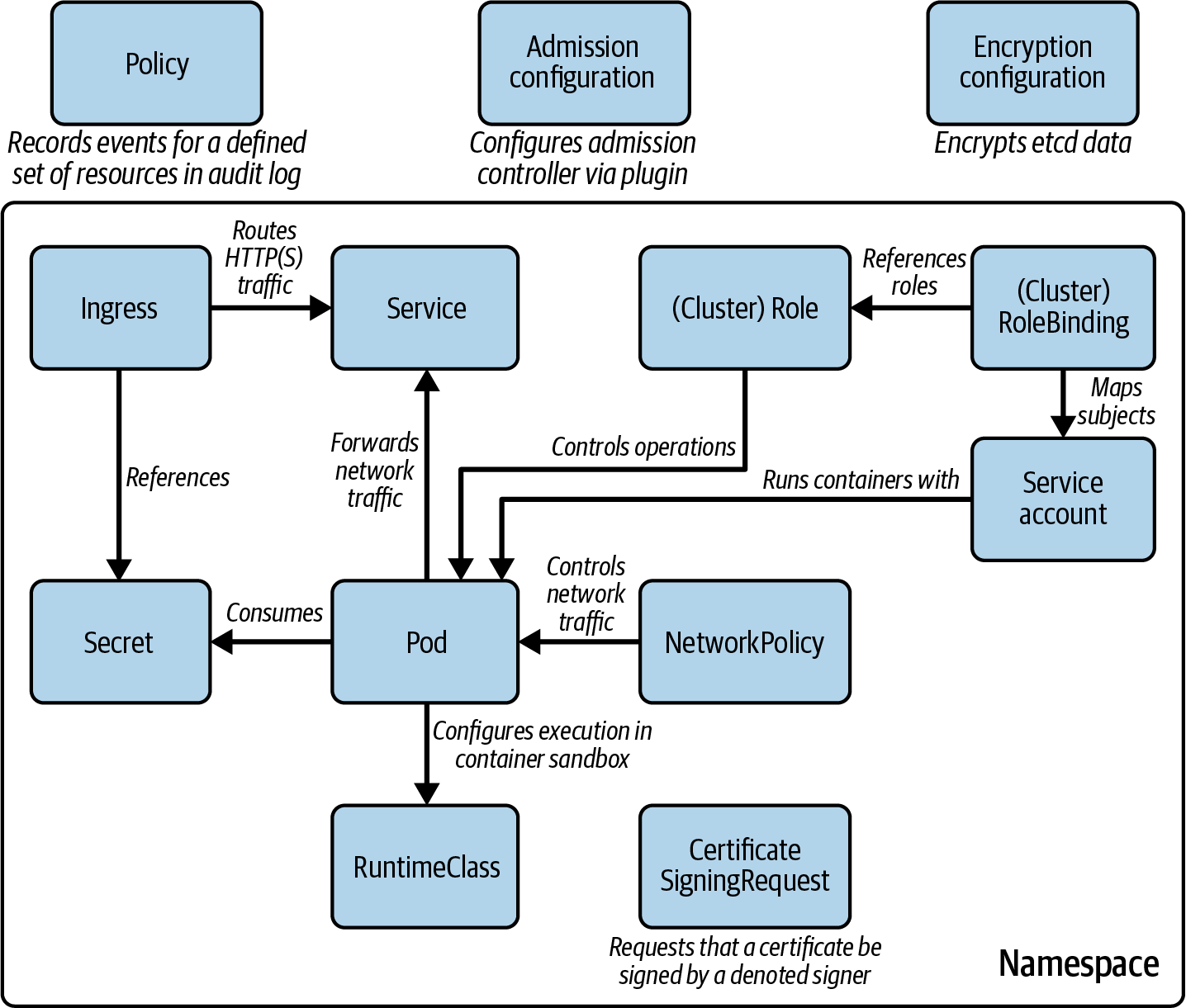
Figure 1-2. Kubernetes primitives relevant to the exam
In addition to Kubernetes core primitives, you will also need to have a grasp of specific Custom Resource Definitions (CRDs) provided by open source projects. For example, the Open Policy Agent (OPA) Gatekeeper provides the primitives’ ConstraintTemplate.
Involved External Tools
A significant portion of the exam requires you to demonstrate expertise with external, security-related tools. Some of the tools have been spelled out explicitly in the curriculum, but there are other tools that fall into the same functional category. At the very least, you will have to be familiar with the following tools:
Documentation
During the exam, you are permitted to open a well-defined list of web pages as a reference. You can freely browse those pages and copy-paste code in the exam terminal. The Frequently Asked Questions (FAQ) for the CKS spells out a list of permitted URLs.
The official Kubernetes documentation includes the reference manual, the GitHub site, and the blog:
-
Reference manual: https://kubernetes.io/docs
-
GitHub: https://github.com/kubernetes
For external tools, you are allowed to open and browse the following URL:
Candidate Skills
The CKS certification assumes that you already have an administrator-level understanding of Kubernetes. The CNCF requires you to acquire the CKA certificate as a prerequisite. Without those credentials, you won’t be able to sign up for the CKS exam. If you have not passed the CKA exam yet or if you want to brush up on the topics, I’d recommend having a look at my book Certified Kubernetes Administrator (CKA) Study Guide.
For the remainder of the book, I will simply assume that you already have the knowledge needed for the CKA. Therefore, I won’t repeat the basics on overlapping topics anymore. For convenience reasons, I will point you to the relevant information in the CKA book as needed. Please revisit the sections on the exam environment and time management in the CKA book. They equally apply to the CKS exam.
Practicing and Practice Exams
Hands-on practice is extremely important when it comes to passing the exam. For that purpose, you’ll need a functioning Kubernetes cluster environment. The following options stand out:
-
I found it useful to run one or many virtual machines using Vagrant and VirtualBox. Those tools help with creating an isolated Kubernetes environment that is easy to bootstrap and dispose on demand. Some of the practice exercises in this book use this setup as their starting point.
-
It is relatively easy to install a simple Kubernetes cluster on your developer machine. The Kubernetes documentation provides various installation options, depending on your operating system. Minikube is useful when it comes to experimenting with more advanced features like Ingress or storage classes, as it provides the necessary functionality as add-ons that can be installed with a single command.
-
If you’re a subscriber to the O’Reilly learning platform, you have unlimited access to labs running a Kubernetes environment. In addition, you can test your knowledge with the help of the CKS practice test in the form of interactive labs.
You may also want to try one of the following commercial learning and practice resources:
-
The book Certified Kubernetes Administrator (CKA) Study Guide covers the curriculum of the CKA certification. Revisit the book’s materials for a refresher on the foundations.
-
Killer Shell is a simulator with sample exercises for all Kubernetes certifications.
-
The CKS practice exam from Study4exam offers a commercial, web-based test environment to assess your knowledge level.
Summary
The CKS exam verifies your hands-on knowledge of security-related aspects in Kubernetes. You are expected to understand core Kubernetes primitives and concepts that can fulfill security requirements, such as RBAC, network policies, and Ingress. The exam also involves helpful third-party security tools. You need to demonstrate how to effectively use those tools. Passing the CKA exam is mandatory for the CKS. Make sure you pass the CKA first if you haven’t done so yet.
The following chapters align with the exam curriculum so that you can map the content to the learning objectives. At the end of each chapter, you will find sample exercises to practice your knowledge. The discussion of each domain concludes with a short summary of the most important aspects to learn.
Get Certified Kubernetes Security Specialist (CKS) Study Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

