Chapter 17. Authentication, Authorization, and Admission Control
The API server is the gateway to the Kubernetes cluster. Any human user, client (e.g., kubectl), cluster component, or service account will access the API server by making a RESTful API call via HTTPS. It is the central point for performing operations like creating a Pod or deleting a Service.
In this chapter, we’ll focus on the security-specific aspects relevant to the API server. For a detailed discussion on the inner workings of the API server and use of the Kubernetes API, refer to Managing Kubernetes by Brendan Burns and Craig Tracey (O’Reilly).
Processing a Request
Figure 17-1 illustrates the stages a request goes through when a call is made to the API server. For reference, you can find more information in the Kubernetes documentation.
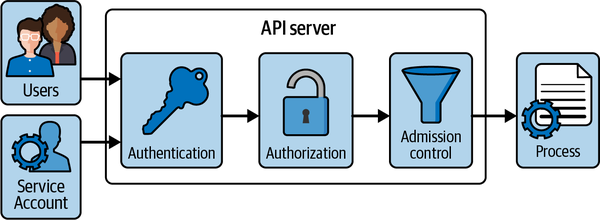
Figure 17-1. API server request processing
The first stage of request processing is authentication. Authentication validates the identity of the caller by inspecting the client certificates or bearer tokens. If the bearer token is associated with a service account, then it will be verified here.
The second stage determines if the identity provided in the first stage can access the verb ...
Get Certified Kubernetes Application Developer (CKAD) Study Guide, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

