Chapter 4. Road Ahead
In this final chapter, you will learn about Microsoft’s vision for confidential computing, its contributions to the advancement of the community, references to customer and partner case studies, and helpful resources for gaining more in-depth knowledge of Azure confidential computing.
Microsoft’s Vision for Confidential Computing
Trust is an essential factor for organizations to embrace cloud computing, and confidential computing is critical in building the trust, backed up by cryptographic guarantees, that data is always protected from unauthorized access even when it is in use. Microsoft has made it a top priority to provide customers with best-in-class security and privacy capabilities in Azure without sacrificing performance. Microsoft offered a preview of its first confidential computing offering, VMs with application enclaves, in September 2017 to assist customers in securing the confidentiality and integrity of their data and code while it is processed in the Azure cloud.
In 2018, Microsoft released the Open Enclave SDK under the MIT license, aiming for a consistent API surface centered on enclave abstraction, portability between TEE types such as Intel SGX and Arm TrustZone, and architectural freedom. This SDK was eventually incorporated into a CCC project. Microsoft Research has been instrumental not only in developing cutting-edge algorithms that improve confidential computing capabilities on the Microsoft platform but also in sharing them in research publications and open source projects for the benefit of the global community.
Innovation
Microsoft’s Azure Research team has been conducting groundbreaking research to identify methods for protecting privacy in applications and workloads deployed in public cloud as well as private and hybrid cloud environments. This research has developed cutting-edge techniques for memory tagging, malware containment, and data clean rooms that have been implemented by several hardware and software products across the industry. These innovations have also led to many open source projects:
-
Confidential Consortium Framework (CCF) is an open source framework for building a new category of secure, highly available, and performant applications that focus on multi-party compute and data.
-
Project Verona is a research programming language developed to explore the concept of concurrent ownership. Microsoft is providing a new concurrency model that seamlessly integrates ownership.
-
snmalloc is a high-performance allocator. It can be used directly in a project as a header-only C++ library, on Elf platforms (e.g., Linux, BSD), and in Rust.
-
Revizor is a security-oriented fuzzer for detecting information leaks in CPUs, such as from Spectre and Meltdown.
-
Privacy Estimates is a library for statistically estimating the privacy of machine learning training pipelines when subjected to membership inference attacks.
Moreover, this team’s research and development have contributed directly to multiple Microsoft products, including:
-
Confidential containers on Azure Container Instances
-
Azure Confidential Ledger
-
Azure Managed Confidential Consortium Framework (based on CCF)
-
Confidential computing with GPUs
-
Azure SQL Always Encrypted
Confidential Consortium Framework (CCF)
Microsoft Research developed the CCF for building secure, highly available, and performant applications that focus on multi-party compute and data. It combines TEEs and flexible decentralized governance to enable scalable and high-performance confidential applications, backed by an immutable ledger for auditability purposes. Figure 4-1 shows key characteristics of the CCF.
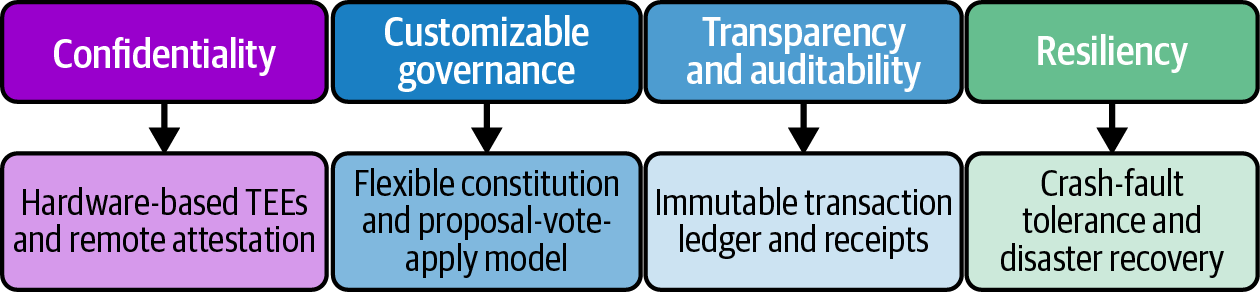
Figure 4-1. Key characteristics of the CCF
A basic CCF network is made of three nodes, and all nodes run the same application inside the TEE. All transactions made by the user and members are stored in a replicated encrypted ledger, where you can extract a receipt that can be used for an audit. Clients interact with the CCF using modern languages like JavaScript/TypeScript, and connections are secure via TLS.
Microsoft also released the Azure Managed Confidential Consortium Framework service that provides customers with the ability to use CCF to build their own multi-party applications with the ACC.
For more details on CCF, please visit the website.
Confidential Computing Consortium (CCC)
The CCC brings together hardware vendors, cloud providers, and software developers to speed up the adoption of TEE technologies and standards. Microsoft was a founding member of the CCC in 2019 and has been an active member since its inception. The CCC has grown to become home to a diverse group of market-leading vendors that are driving transformation. The consortium is also developing cross-industry standards under the Linux Foundation to promote the adoption of confidential computing by focusing extensively on open source communities and projects.
For more information on the CCC, please visit their website.
Resources
Azure confidential computing has been used by a diverse range of customers and partners from a variety of sectors. The case studies highlighted in the next section will show you how ACC helps protect data at cloud scale in different scenarios. The section concludes with a list of helpful resources that will aid in developing a more in-depth understanding of various features of ACC.
Customer and Partner Case Studies
The following are a few examples of how customers and partners are using ACC in real-world scenarios to protect data from unauthorized access while it is in use.
For more details, please visit the Microsoft Customer Stories site.
-
Signal is a free, open source, private messaging application designed to protect the privacy of messages and user data. It employed ACC as one of its cloud solutions, using secure enclaves to host backend services.
-
Royal Bank of Canada (RBC) provides value to millions of clients by offering trustworthy, modern financial services at scale. Combining data and digital analysis allows RBC to turn data into personalized offers with the piloted virtual clean room (VCR). The VCR is a privacy-preserving multi-party data-sharing and collective insight generation platform built on ACC that relies on Intel SGX secure enclave technology.
-
Leidos is a science, engineering, and technology organization focused on solving some of healthcare’s most demanding challenges. Sharing and aggregating real-world patient data and evidence is key to driving better healthcare outcomes. At the same time, patient privacy and medical records security need to be maintained. Leidos has employed Microsoft Azure confidential computing using Intel SGX to accelerate clinical trials and drive new insights, resulting in better patient outcomes while addressing privacy concerns.
-
BeeKeeperAI uses ACC to create secure data enclaves built on Intel SGX. Within the enclave, encrypted AI computes against an encrypted dataset such that all aspects of the solution remain within the HIPAA-compliant cloud environment.
-
Fireblocks is a blockchain infrastructure provider for creating an ecosystem to reduce the complexity of working with digital assets and cryptocurrencies and provide a higher level of security. Fireblocks uses ACC and Intel SGX to redefine the digital assets industry, processing more than $4 trillion in assets while achieving the highest international security certifications and creating new opportunities on the blockchain network for organizations of all types.
-
Decentriq is a Swiss company that offers an enterprise-grade SaaS platform for confidential data collaboration. Decentriq is not only making data collaboration simpler but, in many cases, is also using ACC to allow multiple groups to come together and use sensitive data. Since migrating to the cloud and accelerating its confidential computing journey with Azure, Decentriq has made collaboration on sensitive datasets highly scalable and helped customers to reach new milestones, including doubling the clickthrough rates for digital advertising.
-
Swift is a leading infrastructure provider for financial messaging services that has worked with over 11,500 institutions to drive new ways to detect and catch fraudulent transactions. It has partnered with Microsoft to innovate further in the fight against financial crime. Using federated learning techniques along with Azure Machine Learning and ACC, Swift and Microsoft are building an anomaly detection model for transactional data without copying or moving data from secure locations.
-
Carbon Asset Solutions has a goal to help the planet to get rid of damaging atmospheric carbon dioxide. It needed to capture and encrypt precision carbon measurement data, protecting against data tampering at both ends of the carbon credit process, while keeping long-term global scalability in mind. By using ACC, Carbon Asset Solutions is working to solve one of the earth’s pivotal environmental problems.
Readiness
Here are more resources to dive deeper into the capabilities of ACC:
-
Microsoft Learn course: “Intro to confidential computing with Azure Virtual Machines”
Here are conference sessions and other training videos:
-
Microsoft Build Conference 2023
-
Microsoft Secure Conference 2023
-
Open Confidential Computing Conference 2023
-
Others
This report examines the fundamental principles of confidential computing, the roles it plays in protecting the privacy of data while in use, and how it aligns with zero-trust principles. It also outlines how Microsoft ACC brings confidential computing to the Azure cloud. ACC enables organizations to deploy highly sensitive workloads in the cloud by providing guarantees backed up by cryptographic proofs that their workloads, including data and code, are not accessible when in use by any unauthorized party, including Microsoft. This allows for defense in depth and adherence to zero-trust principles by removing any implicit trust in using ACC features like attestation that provide assurance that hardware and software have not been tampered with. Furthermore, this strategy allows organizations to complete the entire trifecta of data security: protection of data at rest, in transit, and in-use. It helps organizations operate with an “always assume a breach” mindset, which is a fundamental tenet of zero trust.
Get Azure Confidential Computing and Zero Trust now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

