- Discovery Phase
- Detect Phase
- Threat Score Phase
- Threat Response Phase
- Protect Phase
- Monitor Phase
- Conclusion
- Firms in AI Cybersecurity
Chapter Outline
- How to handle AI/ML models for security solutions
Key Learning Points
- Learn and understand how AI/ML applies to security areas
- Data preparation for
- Input
- Output
- Training data
- Validation data
- Evaluate different algorithms
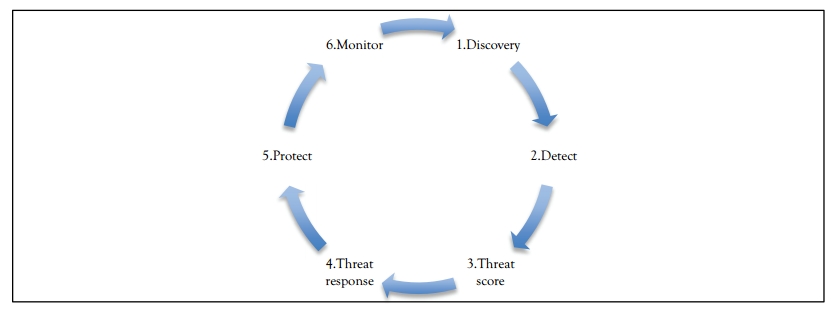
Figure 5.1 Security AI process
Security AI Process
The artificial intelligence (AI) system being developed uses the following design approach:
- Discovery phase
- Detect phase
- Threat score phase
- Threat response phase
- Protect phase
- Monitor phase ...
Get Artificial Intelligence for Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

